The Layer 2 Forwarding, L2F Protocol, developed by Cisco Systems, marked a significant advancement of Virtual Private Networks (VPN). As a media-independent tunneling protocol, L2F laid the groundwork for secure, remote network access, allowing data to traverse through public networks like the Internet with the confidentiality of a private network.
This article delves into the technical details, historical significance, and the evolution of L2F into modern VPN technologies. By exploring L2F’s mechanisms, applications, and legacy, we aim to provide a comprehensive understanding of its role in the development of secure and efficient network tunneling solutions.
Table of Contents:
- What is L2F Protocol?
- Technical Overview
- Historical Context and Development by Cisco
- L2F vs. Other Tunneling Protocols
- The Legacy and Evolution of L2F Protocol
- References

1. What is L2F Protocol?
L2F stands for Layer 2 Forwarding, is a media-independent tunneling protocol developed by Cisco Systems. The Layer 2 Forwarding or L2F protocol tunnels data-link layer frames in such protocols as Point-to-Point Protocol (PPP) or Serial Line Internet Protocol (SLIP), making it possible to create virtual private networks (VPNs) over a public network such as the Internet.
On the server side, L2F protocol can be used with such features as user authentication through Remote Authentication Dial-In User Service (RADIUS), dynamic allocation of addresses, and quality of service (QoS). L2F is implemented in Cisco routers through Cisco’s Internetwork Operating System (IOS).
2. Technical Overview of the L2F Protocol
The Layer 2 Forwarding (L2F) protocol, engineered by Cisco Systems, was designed to establish a foundation for Virtual Private Network (VPN) connectivity by enabling secure tunneling across diverse network architectures. L2F’s architecture and operational principles reflect its core objective: to facilitate remote network access with an emphasis on security and versatility.
Architecture and Operation Principles
L2F protocol operates at the data link layer (Layer 2) of the OSI model, which allows it to encapsulate and forward data packets across different media without being tied to a specific network layer protocol. This level of operation is crucial for supporting media-independent tunneling, enabling L2F to transport various types of traffic, such as IP, IPX, or AppleTalk, across an IP network.
The protocol encapsulates data frames within L2F headers, which are then transmitted through tunnels established between an L2F Access Concentrator (LAC) and an L2F Network Server (LNS). The LAC typically resides at the user’s end, acting as the initiator of the tunnel, while the LNS operates on the network side, managing the reception of tunneled data and its appropriate routing.
Data Encapsulation and Secure Tunnel Establishment
L2F’s encapsulation mechanism wraps the original data packet with an L2F header, creating a new packet that can traverse the tunnel securely. This process includes the addition of a tunnel ID, which uniquely identifies the tunnel, and a session ID, which identifies the session within the tunnel. These identifiers are critical for managing multiple simultaneous connections and ensuring that data packets are correctly associated with their respective sessions.
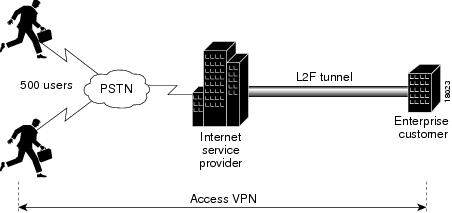
For secure tunnel establishment, the L2F protocol relies on the underlying transport protocol to provide encryption and authentication. Originally, L2F did not include native encryption capabilities, which meant that it often worked in conjunction with other protocols like IPsec to ensure the confidentiality and integrity of the data being tunneled.
Support for Multiple Simultaneous Connections
One of the hallmark features of L2F is its ability to support multiple simultaneous connections over a single tunnel. This multiplexing capability allows for efficient use of network resources, as multiple user sessions can be transported over the same tunnel without the need for separate tunnel establishments for each session. This feature is particularly beneficial for service providers offering remote access services to numerous clients.
Ensuring Data Confidentiality and Integrity
While L2F itself does not provide encryption, its design accommodates the use of encryption protocols to safeguard data as it traverses public networks. By integrating with protocols like IPsec, L2F tunnels can securely transport sensitive information, ensuring that data confidentiality and integrity are maintained from end to end.
3. Historical Context and Development by Cisco
Developed in the mid-1990s, the Layer 2 Forwarding (L2F) protocol emerged at a time when the internet was experiencing rapid growth and the demand for remote access solutions was on the rise. Cisco Systems, recognizing the need for a scalable and secure method to provide remote access over the burgeoning public internet, introduced L2F as a solution to bridge this gap.
Addressing the Needs for Secure Remote Access
The advent of the L2F protocol was timely, addressing the critical need for businesses to securely connect remote users to private networks over the internet. Before the widespread adoption of VPN technologies, remote access was often limited to dial-up connections that were not only slow but also lacked robust security measures. L2F’s ability to create secure tunnels over the internet revolutionized remote access, offering a scalable and more secure alternative.
Contribution to the Evolution of VPN Technologies
L2F played a pivotal role in the evolution of VPN technologies. It laid the groundwork for subsequent protocols by demonstrating the feasibility and benefits of Layer 2 tunneling. L2F’s approach to encapsulating and forwarding data packets across diverse networks set the stage for the development of more advanced tunneling protocols, such as Layer 2 Tunneling Protocol (L2TP).
L2TP, which later became an industry standard, was directly influenced by L2F. It combined the best features of L2F and Microsoft’s Point-to-Point Tunneling Protocol (PPTP), offering enhanced security, support for multiple protocols, and greater flexibility in tunneling methods.
Impact on Early Network Security Practices
The introduction of L2F also marked a significant advancement in network security practices. By facilitating secure, remote network access over the public internet, L2F catalyzed a shift towards more holistic approaches to network security. It underscored the importance of data confidentiality and integrity in remote access services, influencing the development of comprehensive security measures that are now standard in VPN technologies.
The historical context and development of L2F by Cisco Systems not only highlight its importance in the early days of VPN technology but also underscore its lasting impact on network security and remote access solutions. Through its pioneering approach to tunneling and emphasis on security, L2F set the foundation for the continuous evolution of VPN technologies, shaping the way secure remote access is implemented today.
4. L2F vs. Other Tunneling Protocols
In the landscape of VPN technologies, L2F was among the first protocols to facilitate secure tunneling over IP networks. However, it is essential to understand how L2F compares to other tunneling protocols, notably the Point-to-Point Tunneling Protocol (PPTP) and the Layer 2 Tunneling Protocol (L2TP), to appreciate its role and application in network engineering.
L2F and PPTP
PPTP, developed by Microsoft, shares a common goal with L2F: to enable VPN services over the internet. While both protocols allow for the creation of virtual private networks, their approaches and features have distinct differences.
- Security: L2F focuses on tunneling mechanisms without native encryption, relying on external protocols like IPsec for data confidentiality and integrity. PPTP, in contrast, incorporates encryption within its protocol, although the strength of its encryption has been scrutinized and found lacking in comparison to more modern standards.
- Compatibility: PPTP’s integration into Windows operating systems provided it with a widespread adoption advantage. L2F’s utility, predominantly in Cisco environments, meant it was less universally adopted but highly effective within its ecosystem.
L2F and L2TP
L2TP emerged as a direct successor to L2F and PPTP, aiming to combine the best features of both protocols. L2TP encapsulates data similarly to L2F but includes enhancements that address some of L2F’s limitations.
- Integration of Features: L2TP supports multi-protocol tunneling like L2F and includes provisions for encryption and authentication, improving upon the security concerns associated with PPTP and L2F’s lack of native encryption.
- Versatility and Support: L2TP’s design, which integrates the strengths of L2F and PPTP, has led to its adoption as a standard protocol, supported across a broader range of devices and operating systems.
Selection Criteria for Tunneling Protocols
Choosing between L2F, PPTP, and L2TP depends on several factors:
- Security Needs: For environments where security is a paramount concern, L2TP, used in conjunction with IPsec, is often preferred due to its robust encryption capabilities.
- Network Environment: L2F may be favored in Cisco-dominated infrastructures, where its integration and support can be fully leveraged.
- Compatibility Requirements: PPTP might be chosen for its broad compatibility, especially in legacy systems where extensive changes to infrastructure are not feasible.
5. The Legacy and Evolution of L2F Protocol
The introduction of L2F by Cisco Systems marked a significant milestone in the evolution of VPN technologies. Its development not only addressed immediate needs for secure, remote network access but also laid the groundwork for future innovations in tunneling protocols.
Pioneering Layer 2 Tunneling
L2F’s pioneering approach to layer 2 tunneling set a precedent for how data could be securely transmitted over public networks. By operating at the data link layer, the L2F protocol offered a versatile solution for tunneling different protocols, a principle that has been carried forward into subsequent tunneling technologies.
Influence on L2TP
Perhaps the most direct legacy of L2F is its influence on the development of L2TP. As a collaborative effort that merged the best aspects of L2F and PPTP, L2TP represented a significant advancement in tunneling protocol technology, incorporating the flexibility of L2F with enhanced security and compatibility features.
Contribution to Network Security
L2F’s emphasis on secure tunneling contributed to the broader acceptance and implementation of VPNs as a standard component of network security strategies. The protocol’s development underscored the importance of secure, remote access capabilities, a need that has only grown with the proliferation of distributed workforces and cloud computing.
6. References
To further explore the technical and historical aspects of L2F and related tunneling protocols, the following resources are recommended:
Books
- “Virtual Private Networks: Technologies and Solutions” by Ruixi Yuan and W. Timothy Strayer
- “Cisco Network Security Troubleshooting Handbook” by Mynul Hoda