Category: Letter Z
-

Zigbee: The Unsung Hero of Smart Devices
This article will delve into the nuts and bolts of the Zigbee protocol, decoding its magic and how it powers the hidden conversations of our smart homes. From its architecture to its real-world applications, prepare to uncover the invisible network that could be inside your very own living room.
-

Unpacking the Core: The Principles of Zero Trust Security
Through a detailed exploration of its foundational principles, we will uncover how Zero Trust operates not just as a technology, but as a comprehensive strategy reshaping security frameworks across industries.
-
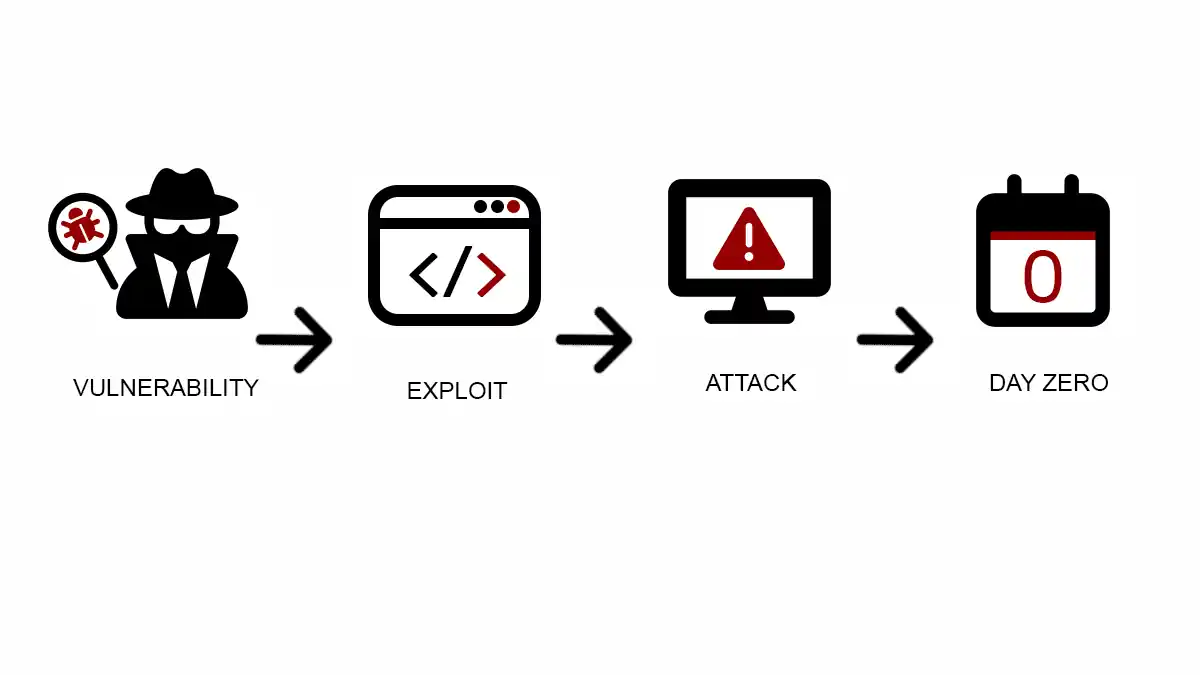
Zero-Day Vulnerabilities: Surviving the Unknown
Delve into the intricate world of zero-day vulnerabilities—what they are, how they’re exploited, and what you can do to protect against them. Your comprehensive guide to understanding zero-days.
-

Unleashing Nostalgia: The ZX Spectrum
Welcome to the extraordinary story of the ZX Spectrum, a revolutionary machine that defined an era and captured the hearts of countless enthusiasts.
-
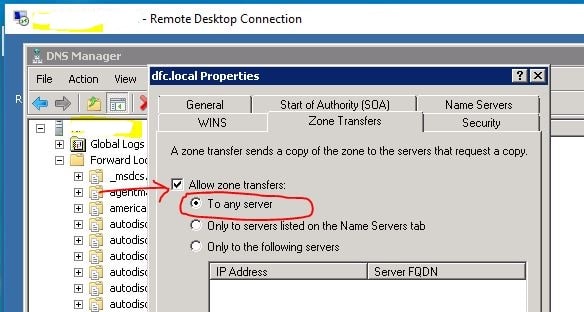
Zone Transfer
Zone Transfer (in a DNS Server) is the process of transferring information in the zone file on a primary name server to a secondary name server.
-
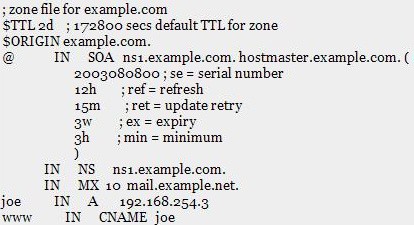
Zone File (DNS)
Zone File is a file on a name server that contains information that defines the zone that the name server manages.
-
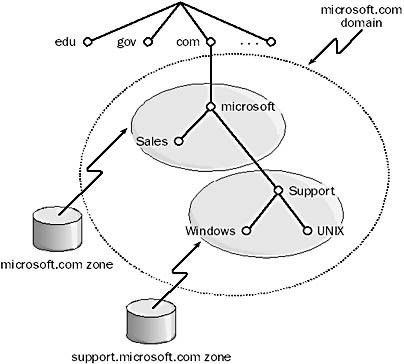
DNS Zone
DNS Zone also called a zone of authority, is a subset of the Domain Name System (DNS) namespace that is managed by a name server.
-

Zero Administration Kit (ZAK)
ZAK (Zero Administration Kit) is a tool collection, methodologies, and guidelines for Microsoft Windows NT Workstation 4 that network administrators can use to implement policy-based management of Windows NT–based networks.