The Distributed Component Object Model (DCOM) is a Microsoft technology for software components distributed across multiple network locations. Building upon the Component Object Model (COM), which enables inter-process communication and dynamic object creation, DCOM extends these capabilities over a network, allowing applications to interact across various computers in a network. This article aims to delve deeply into the intricacies of DCOM, illustrating how it facilitates distributed computing and its impact on software development. For a foundational understanding of COM, refer to our main article on COM. Our focus here is to explore DCOM’s architecture, operation, and applications, providing college-level insights into this pivotal technology.
Table of Contents:
1. What is DCOM (Distributed Component Object Model)?
DCOM is a technology for component-based development of software that is network-aware. Using Distributed Component Object Model (DCOM), developers can create network-aware applications using Component Object Model (COM) components. DCOM works under various network transports, including TCP/IP.
DCOM, or Distributed Component Object Model, is a technology that dates back to the late 1990s. It was developed by Microsoft as an extension of COM (Component Object Model) to support distributed computing. While DCOM was a significant advancement in its time, enabling applications to communicate across different machines in a network, it is considered somewhat outdated in modern computing environments.
The use of DCOM has declined over the years for several reasons:
- Complexity: DCOM is known for its complex configuration, especially in terms of security and network settings. This complexity often makes it difficult to manage, particularly in large-scale and diverse network environments.
- Platform Dependency: DCOM is heavily tied to the Windows operating system, which limits its interoperability with other platforms. In today’s multi-platform environments, this is a significant limitation.
- Evolution of Technology: Newer technologies have emerged that offer more flexibility, better security, and easier cross-platform integration. These technologies have largely replaced DCOM in most applications.
2. How it works
DCOM is a client/server protocol that provides distributed network services to COM, allowing DCOM-enabled software components to communicate over a network similarly to the method by which COM components communicate among themselves on a single machine.
DCOM client objects make requests for services from DCOM server objects on different machines on the network using a standard set of interfaces.
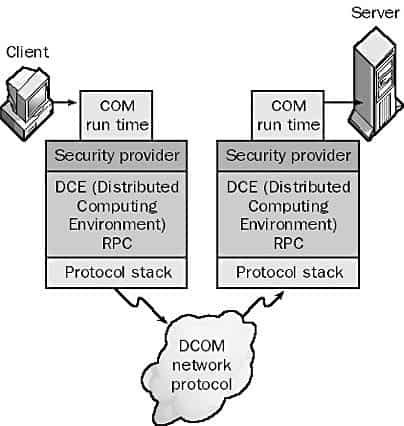
The client object cannot call the server object directly. Instead, the operating system intercepts the DCOM request and uses interprocess communication mechanisms such as remote procedure calls (RPCs) to provide a transparent communication mechanism between the client and server objects. The COM run time provides the necessary object-oriented services to the client and server objects. The COM run time also uses the security provider and RPCs to create network frames that conform to the DCOM standard.
3. DCOM Architecture
3.1 Components and Interfaces
The architecture of DCOM (Distributed Component Object Model) is an extension of COM (Component Object Model), designed to support communication among software components at different locations on a network. DCOM defines a set of interfaces and objects which cooperate to achieve object creation, event handling, and other functionalities over a network. The key components include the client, server, and the DCOM network layer. The client initiates requests for services, the server hosts the objects providing these services, and the network layer manages communication between client and server. Each object in DCOM is identified by a unique identifier, ensuring precise object handling across the network.
3.2 Communication Mechanisms
DCOM uses a combination of remote procedure calls (RPCs) and additional protocols to facilitate communication between distributed components. RPCs allow a program on one machine to execute procedures on a remote machine as if they were local calls. DCOM enhances this with object-oriented methodologies and manages the complexities of network communication, including marshalling and unmarshalling of data, handling network transports, and managing object references across different machines. This ensures that DCOM can efficiently handle the nuances of distributed computing, like network latency and partial failures, while maintaining a seamless interface for developers.
4. Technologies that have supplanted DCOM
Some of the technologies that have supplanted DCOM include:
- Web Services and SOA (Service-Oriented Architecture): Web services, often implemented using protocols such as SOAP (Simple Object Access Protocol) and REST (Representational State Transfer), allow different applications to communicate over the Internet. SOA provides a way to structure applications as a collection of services that can be reused and combined.
- .NET Remoting and WCF (Windows Communication Foundation): For applications within the Microsoft ecosystem, .NET Remoting and later WCF were developed to provide more flexible and secure ways to build distributed applications.
- CORBA (Common Object Request Broker Architecture): In non-Microsoft environments, technologies like CORBA have been used for distributed object-oriented programming.
- Microservices Architecture: More recently, the microservices architectural style has gained popularity, where applications are structured as collections of loosely coupled services.
While DCOM might still be in use in some legacy systems, especially in enterprise settings where older applications are maintained, it’s generally not the technology of choice for new distributed applications. The modern landscape favors technologies that are more adaptable, secure, and platform-agnostic.
5. References
- “Understanding DCOM” by William Rubin and Marshall Brain.
- “Programming Distributed Applications with COM+ and Microsoft Visual Basic” by Ted Pattison.
- “Inside COM+: Base Services” by Guy and Henry Eddon.
- Microsoft’s official documentation on DCOM.