Definition of Kerberos v5 Security Protocol in Network Encyclopedia.
What is Kerberos v5 security protocol?
Kerberos Protocol is a method of securely authenticating users’ requests for access to services on a network. It was developed by the Massachusetts Institute of Technology (MIT), which based it on the Data Encryption Standard (DES).
Kerberos is the primary security protocol for Microsoft Windows 2000 domains and is used by domain controllers to verify the identity of the user and the integrity of data during a session. Kerberos has also been implemented on several UNIX platforms including OpenBSD.
How It Works
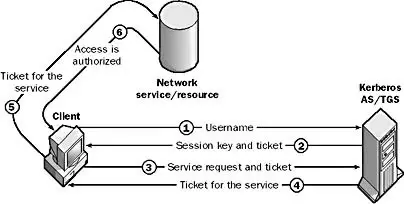
Kerberos uses a ticket-based method for granting a user access to a network service. When a Kerberos-enabled client wants to request a network service (such as network logon) from a Kerberos-enabled server, the client must first contact an authentication server (AS) to receive a ticket and an encryption key.
The encryption key, called the session key, is used to unlock communication between the client and the server and thereby authenticate that communication. The initial ticket, often called the ticket-granting ticket (TGT), contains a copy of the session key and an identity, which is a randomly generated number. The AS passes the TGT and the identity back to the client, which stores the ticket in its ticket cache. When the client wants to access a particular service, it sends the ticket to a ticket-granting server (TGS). (The TGS and AS are usually the same machine.)
The TGS gives the client a ticket that securely identifies the client to the service it is requesting. Finally, the client presents the ticket to the network service it is trying to access and is granted access to the resource as many times as desired until the ticket expires. When the client sends a ticket, the ticket is always accompanied by an authenticator message that is encrypted with the session key. This authenticator includes a time stamp, which is used to ensure that the ticket is legitimate.
In the Windows 2000 implementation of Kerberos, each domain controller has the Kerberos v5 services running on it, and a Kerberos client is built into each server and workstation running Windows 2000. The Kerberos services maintain encrypted user passwords and identities in Active Directory. When a user logs on to a domain controller, the initial Kerberos authentication enables the user to access available resources anywhere in the enterprise because authentication credentials issued by the Kerberos services of one domain are accepted by all domains within a domain tree or a domain forest.
The Kerberos service issues an initial ticket for the logon domain when a user logs on to a Windows 2000 workstation. Any server running Windows 2000 can then validate the client’s ticket without having to contact the domain Kerberos service. It can do this because servers running Windows 2000 share the encryption key that the Kerberos service uses to encrypt tickets. This encryption key is called the server key.
If a Windows 2000 client in one domain requests access to a resource in a remote domain that is part of the same domain tree or forest, the Kerberos service in the local domain issues a referral ticket that the client presents to the Kerberos service in the remote domain. The Kerberos service in the remote domain then issues an initial ticket that is valid for its own domain and identifies the domain. Using this ticket, the client can then access resources in the remote domain.
The implementation of Kerberos in Windows 2000 is an industry-standard version that is compliant with Request for Comments (RFC) 1510.
Some of the benefits of Kerberos authentication include the following:
- Two-way transitive trusts between domains
- Mutual authentication of both client and server during an authentication session
- Delegated authentication for multitier client/server interactions