In the complex orchestration of networked systems, time is not merely a ticking clock; it’s a crucial variable that affects performance, synchronization, and security. In the age of global networks and distributed systems, maintaining time consistency across all nodes becomes paramount. How do we ensure that each component of a system is perfectly synchronized in time? Enter Network Time Protocol (NTP), the unsung hero of network synchronization.
Table of Contents:
- What is Network Time Protocol (NTP)?
- Mechanisms of NTP
- The NTP Packet
- How to Configure an NTP Server
- Security Aspects of NTP
- NTP vs. Other Time-keeping Protocols
- Troubleshooting Common NTP Issues
- Case Studies
- Further Reading and Resources
This comprehensive guide aims to unravel the complex web of NTP, shedding light on its mechanisms, applications, and pivotal role in contemporary computing.

What is Network Time Protocol (NTP)?
Transitioning from a high-level overview, let’s delve into the foundational elements. Network Time Protocol (NTP) is a networking protocol devised to synchronize the clocks of computers over a data network. Originally developed by David L. Mills in 1985, NTP operates over the User Datagram Protocol (UDP) and aims for high accuracy and fault-tolerant timekeeping. While NTP might appear like a simple task of ‘setting the clock,’ in reality, it addresses numerous challenges—from variable network delays to jitter, to even taking into account the relativistic time dilation effects.
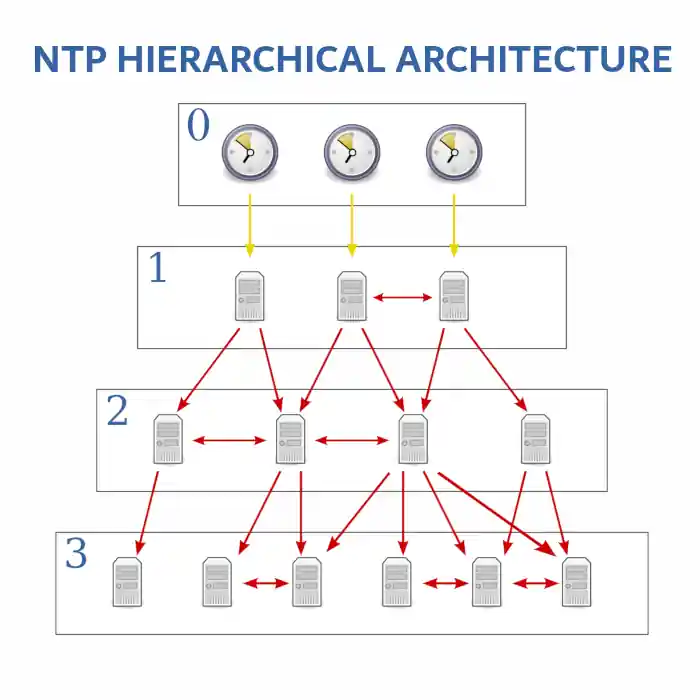
NTP employs a hierarchical, semi-layered architecture of time sources. At the top sits the stratum 0 devices—highly accurate atomic clocks. These feed time to stratum 1 servers, which in turn synchronize stratum 2 servers, and the hierarchy cascades down. This architecture not only provides robustness but also optimizes accuracy by mitigating the compounded errors that can occur in multi-step synchronization processes.
Mechanisms of NTP
Embarking on our exploratory journey through Network Time Protocol (NTP), it is imperative to delve into the core mechanisms that make NTP such a precise and reliable protocol. This chapter aims to demystify the inner workings of NTP, including its clock stratum, poll intervals, and algorithms. Such an understanding will serve as a pivotal foundation for anyone interested in network synchronization, be it students, system administrators, or seasoned tech professionals.
Clock Stratum
To begin, let’s address the hierarchical system of time sources known as the ‘clock stratum.’ In NTP, devices are categorized into different strata based on their proximity to an authoritative time source. Stratum 0 devices are high-precision timekeeping systems—like atomic clocks or GPS clocks—that act as primary references. Subsequently, Stratum 1 servers synchronize directly with these Stratum 0 devices. Stratum 2 servers synchronize with Stratum 1 servers, and the hierarchy continues in a cascading fashion. This tiered system ensures accuracy and minimizes network congestion by controlling the flow of synchronization traffic.
Poll Intervals
Shifting gears to another crucial component, let’s consider the ‘poll interval.’ The poll interval is the duration between successive synchronization messages sent by an NTP client to its server. A smaller poll interval will result in higher accuracy but will also consume more network bandwidth. NTP dynamically adjusts the poll interval based on network conditions, clock stability, and other variables, thus maintaining an optimal balance between accuracy and resource consumption.
Algorithms: Marzullo’s Algorithm and Others
Delving deeper, algorithms are the cornerstone of NTP’s operational excellence. One of the primary algorithms used by NTP for clock synchronization is Marzullo’s Algorithm. Designed to find a time range that is consistent with the largest number of server clocks, it minimizes the impact of outlier clocks that may be significantly off. Moreover, NTP employs other techniques like the ‘clock filter algorithm’ and the ‘Cristian’s algorithm’ to filter out noise from measurements and to estimate the most probable true time.
Other Mechanisms: Jitter and Drift Compensation
Beyond these key components, NTP also addresses challenges like network jitter and clock drift. NTP’s time synchronization messages contain timestamp information that accounts for transmission delay, enabling it to filter out ‘jitter,’ or variations in time due to network congestion. Additionally, NTP employs a local clock algorithm that adjusts the system clock in small increments to avoid abrupt changes, thereby compensating for the drift.
In summary, NTP’s effectiveness stems from its meticulously crafted mechanisms, each designed to solve specific challenges in time synchronization. As we progress through subsequent chapters, these foundational concepts will serve as essential building blocks for a more nuanced understanding of NTP.
The NTP Packet
As we continue our in-depth exploration of the Network Time Protocol (NTP), it’s essential to focus on the NTP packet. This crucial data structure facilitates the entire time synchronization process, serving as the vehicle that conveys timing information across network devices. Understanding the anatomy of an NTP packet provides valuable insights into how NTP achieves its objectives of accuracy and reliability. This chapter will dissect the structure, fields, and significance of an NTP packet, further equipping students, system administrators, and tech aficionados with the knowledge to grasp NTP’s inner workings.
Packet Structure
Let’s first delve into the basic structure. An NTP packet typically consists of a 48-byte data structure, divided into various fields that carry different types of information. The packet begins with a 4-byte header, followed by various optional fields and timestamps.
Header Fields
Transitioning to the header fields, these are vital for the control and management of the packet. The header comprises several components:
- Leap Indicator (LI): 2 bits to notify of an impending leap second to be inserted or deleted in the last minute of the current month.
- Version Number (VN): 3 bits specifying the NTP version in use.
- Mode: 3 bits indicating the mode (client, server, etc.).
- Stratum: 8 bits representing the stratum level of the local clock.
- Poll: 8 bits specifying the maximum interval between successive messages.
- Precision: 8 bits describing the precision of the local clock.
- Root Delay and Root Dispersion: These 32-bit fields provide information about the round-trip delay and dispersion to the primary reference source.
Timestamps
Shifting gears to perhaps the most critical part of the NTP packet, the timestamps. Four timestamps are used:
- Reference Timestamp: Records the time when the system clock was last set.
- Originate Timestamp: Records the time when the request departed the client for the server.
- Receive Timestamp: Marks the time when the request was received by the server.
- Transmit Timestamp: Marks the time when the reply departed the server for the client.
The timestamps enable the calculation of round-trip delay and clock offset, two key metrics essential for synchronization.
Optional Fields
While optional, additional fields can be included for authentication and extensions. These fields are used primarily for securing NTP against various types of attacks and for adding extensibility to the protocol.
In sum, each field within an NTP packet serves a specific and crucial function in the grand symphony of network time synchronization. The careful orchestration of these fields ensures that NTP remains a robust, accurate, and adaptable protocol, capable of meeting the stringent demands of modern networks. As we navigate further into the world of NTP, this foundational understanding of the NTP packet will be invaluable.
How to Configure an NTP Server
Pivoting from the theory and structure of NTP, it’s time to dive into practical applications. Specifically, we’ll focus on setting up an NTP server—a crucial step for system administrators aiming to maintain network-wide time synchronization. This chapter provides a hands-on, step-by-step guide to help you get an NTP server up and running.
1. Choosing an OS and NTP Software
First off, you need to select an operating system and NTP software. Linux is often the go-to choice for its robustness and flexibility. NTPd and Chrony are popular software packages for Linux. Install your chosen software using package management tools like apt for Ubuntu or yum for CentOS.
2. Configuration File
After installation, head over to the configuration file, usually located at /etc/ntp.conf or /etc/chrony/chrony.conf, depending on your software. Open the file with a text editor. Here, you define the NTP servers your system will synchronize with. Use reputable, preferably geographically close, Stratum 1 or Stratum 2 servers.
3. Firewall Rules
Don’t forget about firewall settings. Open the NTP port (usually UDP 123) to allow incoming and outgoing NTP traffic. Update your firewall rules accordingly.
4. Test and Monitor
Finally, start the NTP service using service management commands like systemctl. Monitor the synchronization process with commands like ntpq -p or chronyc tracking. Ensure everything works as expected.
To recap, setting up an NTP server involves a few straightforward steps: selecting an OS and software, editing the configuration file, adjusting firewall rules, and monitoring the service. Following this guide ensures that you won’t miss any critical components in the setup process.
Security Aspects of NTP
Switching gears to a subject of increasing importance, let’s delve into the security aspects of NTP. In a world where cyber threats are ever-present, securing your NTP server isn’t just optional—it’s essential. This chapter will walk you through the key security features and best practices to keep your NTP implementation secure.
Authentication
First and foremost is authentication. NTP supports symmetric key authentication, wherein both the client and server share a secret key. To set this up, include the key and trustedkey directives in your NTP configuration file. This ensures that rogue servers can’t manipulate your system time.
Rate Limiting and Throttling
Next up, consider rate limiting and request throttling. These practices safeguard your server against denial-of-service attacks. Use the discard and restrict directives in your configuration file to set limitations on incoming requests.
Monitoring and Logging
Another vital component is monitoring and logging. Keep an eye on server logs and set up alerts for unusual activities. Monitoring tools can help you quickly identify and act upon any security threats.
Secure Versions and Patches
Lastly, always use secure and updated versions of NTP software. Security vulnerabilities get discovered over time, and keeping your software up-to-date protects you from known threats.
In summary, a secure NTP implementation hinges on multiple pillars: robust authentication, effective rate limiting, vigilant monitoring, and timely updates. By meticulously implementing these measures, you not only secure your NTP server but also contribute to the overall security of your network.
NTP vs. Other Time-keeping Protocols
Having illuminated the technical and security facets of NTP, it’s now opportune to contrast it with other time-keeping protocols. This comparison will elucidate why NTP often emerges as the go-to solution for a vast array of applications. We’ll chiefly discuss Simple Network Time Protocol (SNTP) and Precision Time Protocol (PTP).
Simple Network Time Protocol (SNTP)
Firstly, let’s examine SNTP. Essentially a simplified version of NTP, SNTP is easier to implement but offers less accuracy. For small networks or less mission-critical applications, SNTP might suffice. However, it lacks advanced features like clock stratum, making it less ideal for more complex setups.
Precision Time Protocol (PTP)
Moving on to PTP, this protocol aims for extremely high accuracy, often within the nanosecond range. Commonly found in financial and scientific computing environments, PTP employs specialized hardware and is consequently more expensive to implement than NTP.
Key Differences
To sum it up, SNTP is simpler but less accurate, PTP is highly accurate but more costly, and NTP strikes a balance, offering robust features and good accuracy without requiring specialized hardware.
Troubleshooting Common NTP Issues
In the final chapter of our comprehensive guide, we pivot to the inevitable challenges: troubleshooting common NTP issues. Understanding how to diagnose and rectify issues is pivotal for anyone responsible for maintaining a network’s time synchronization. Let’s delve into some of the common problems you might encounter.
Time Drift Issues
First on our list is time drift. If you notice that your system time is constantly out of sync, check for high system load or software that might interfere with NTP. Use the ntpq or chronyc commands to analyze drift and make adjustments as necessary.
Connectivity Issues
Secondly, connectivity problems. Ensure that the NTP server is reachable and that your firewall allows traffic on the NTP port (usually UDP 123). Use ping or traceroute commands for basic network diagnostics.
Configuration Errors
Next, let’s tackle configuration errors. These often manifest as synchronization failures. Review your ntp.conf or chrony.conf file to ensure that all server addresses and options are correctly set.
Version Mismatch
Lastly, you might run into version mismatches between your NTP software and the servers you are trying to synchronize with. Always ensure you are running a compatible version, and consider updating if necessary.
In conclusion, troubleshooting NTP issues requires a systematic approach. Armed with these tips and tools, you’re well-equipped to tackle most common issues head-on, ensuring the smooth operation of your NTP service.
Case Studies
After dissecting the mechanics, configurations, and troubleshooting steps of NTP, it’s valuable to see how it operates in the real world. In this chapter, we take an analytical approach to a couple of case studies that demonstrate NTP’s practical implications.
Case Study 1: Financial Services
First up, the financial sector. Precision in timekeeping is vital for transaction logging and fraud detection. In this domain, NTP servers often sync with atomic clocks to attain accuracy within milliseconds. Any deviation can result in severe financial repercussions, making NTP a cornerstone of the industry’s IT infrastructure.
Case Study 2: Telecommunications
Next, let’s focus on the telecommunications sector. Accurate time synchronization is crucial for network operations, especially in mobile networks. When connecting a call or transmitting data packets, timing needs to be impeccably synchronized across various nodes. Here, NTP provides the backbone for accurate data exchange and service delivery.
These case studies show the broad scope and utility of NTP, from safeguarding financial transactions to ensuring the efficacy of telecommunications services.
Further Reading and Resources
As we reach the end of this comprehensive guide, let’s pivot towards the avenues where you can deepen your understanding of NTP. Knowledge is ever-evolving, and staying updated is key to adapting to new challenges in time synchronization.
Books
- “Computer Networking: A Top-Down Approach” by James F. Kurose and Keith W. Ross – Covers NTP in the context of network protocols.
- “UNIX System Administration Handbook” by Evi Nemeth et al. – Contains a section on NTP and time synchronization in UNIX systems.
Online Resources
- NTP official website – For documentation, FAQs, and latest updates.
- NIST Time and Frequency Division – Offers articles and research on time synchronization protocols including NTP.
RFCs
Through these resources, you can deepen your expertise, keeping your skills and systems up-to-date in this critical area of network management.
With this, we conclude our in-depth exploration of Network Time Protocol. Armed with this knowledge, you are not just a passive user but a competent administrator or professional who can set up, secure, and troubleshoot an NTP service. Stay curious and keep learning!