Microsoft Cybersecurity Reference Architectures (MCRA) is a set of documents and resources provided by Microsoft that outline recommended approaches for designing and implementing secure systems and networks.
The MCRA includes guidance on how to secure different types of systems, including cloud-based systems, on-premises systems, and hybrid systems that combine both types. It covers a wide range of topics, including identity and access management, data protection, network security, and incident response.
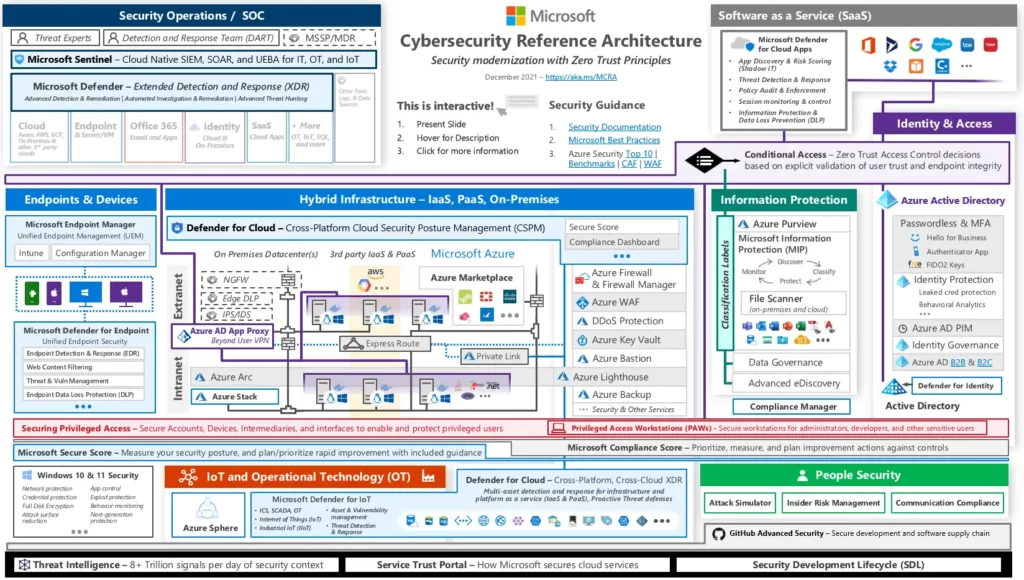
The Microsoft Cybersecurity Reference Architectures is intended to help organizations of all sizes design and implement secure systems that meet their specific needs and requirements. It is intended to be used as a reference resource, rather than a step-by-step guide, and organizations are encouraged to customize and adapt the recommendations to fit their specific needs and environments.
Check out this article: Common Security Threats in Computer Networks.
Capabilities
The Microsoft Cybersecurity Reference Architectures (MCRA) covers a wide range of capabilities related to the design and implementation of secure systems and networks.
Some of the key capabilities that are addressed in the MCRA include:
Identity and access management
This capability covers the processes and technologies used to manage and secure user identities and access to systems and resources. It includes recommendations for implementing multi-factor authentication, access control, and identity federation.
Data protection
This capability covers the processes and technologies used to protect data from unauthorized access or tampering. It includes recommendations for implementing data encryption, data masking, and data classification.
Network security
This capability covers the processes and technologies used to secure networks and protect against external threats, such as cyberattacks. It includes recommendations for implementing firewalls, intrusion detection and prevention systems, and network segmentation.
Incident response
This capability covers the processes and technologies used to respond to and recover from security incidents, such as data breaches or malware attacks. It includes recommendations for implementing incident response plans, incident response teams, and incident response tools.
Governance, risk, and compliance
This capability covers the processes and technologies used to ensure that an organization’s systems and networks are compliant with relevant regulations and standards. It includes recommendations for implementing policies, procedures, and controls to support governance, risk management, and compliance.
Security operations
This capability covers the processes and technologies used to monitor and maintain the security of systems and networks on an ongoing basis. It includes recommendations for implementing security monitoring, vulnerability management, and patch management.
People
The Microsoft Cybersecurity Reference Architectures (MCRA) recognize that people are an important aspect of any cybersecurity strategy. In the MCRA, people are referred to as one of the three pillars of cybersecurity, along with process and technology.
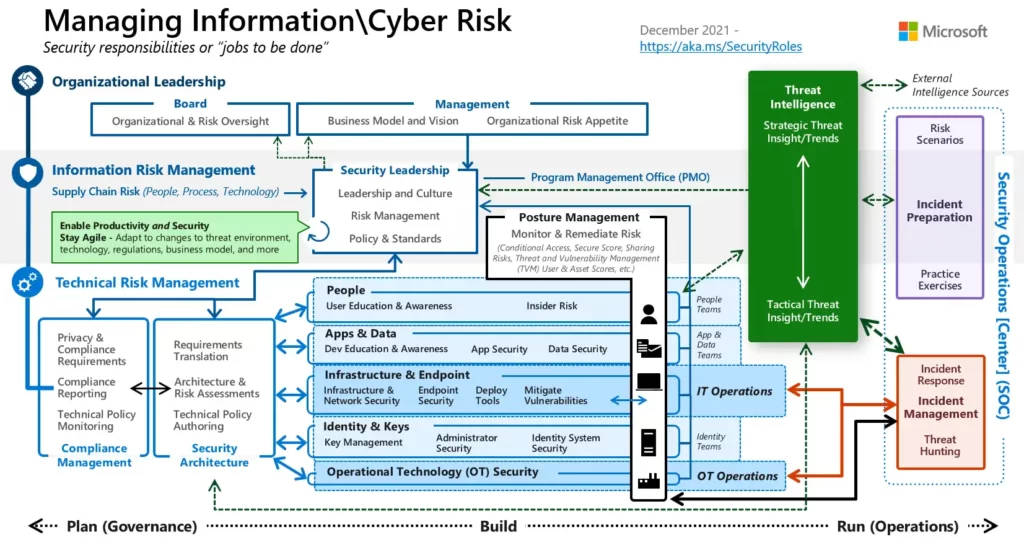
The MCRA recommends that organizations invest in training and education programs to ensure that their employees are knowledgeable about cybersecurity best practices and can identify and mitigate potential threats. It also recommends implementing policies and procedures to ensure that employees follow best practices and report any security incidents or concerns to the appropriate authorities.
In addition to employees, the MCRA also recognizes the importance of engaging with external partners and stakeholders, such as suppliers, customers, and regulators, to ensure that cybersecurity is integrated into all aspects of the organization’s operations. This includes establishing clear communication channels, developing partnerships and agreements, and implementing processes for managing third-party risk.
Overall, the MCRA emphasizes the importance of people in building and maintaining a secure organization, and recommends that organizations invest in the training, education, and engagement of their employees and stakeholders to support their cybersecurity efforts.
Zero Trust User Access
Zero Trust User Access is a security model that is based on the principle of “never trust, always verify.” In this model, all users, regardless of their location or device, are treated as potential threats and must be authenticated and authorized before they can access any resources or systems. This is in contrast to traditional security models, which often rely on trust relationships between users, systems, and networks.
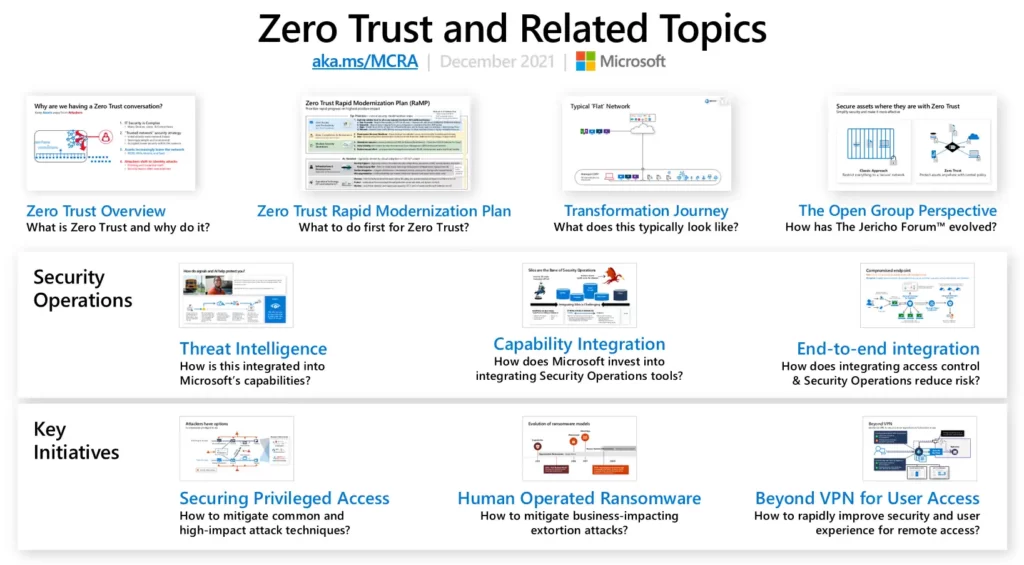
The Microsoft Cybersecurity Reference Architectures (MCRA) recommends implementing a Zero Trust User Access model as a means of reducing the risk of unauthorized access to systems and resources. To support this model, the MCRA recommends implementing the following capabilities:
- Multi-factor authentication: This involves requiring users to provide multiple forms of authentication, such as a password and a security token, to confirm their identity before they can access systems and resources.
- Access control: This involves implementing policies and controls to determine which users are authorized to access which systems and resources, and under what conditions.
- Identity federation: This involves integrating different identity systems and allowing users to access systems and resources using a single set of credentials.
- Device management: This involves implementing policies and controls to ensure that only trusted devices are allowed to access systems and resources, and that all devices are compliant with security standards.
Overall, the goal of a Zero Trust User Access model is to reduce the risk of unauthorized access to systems and resources by verifying the identity and trustworthiness of all users before granting them access.
Security Roles and Responsibilities
In the Microsoft Cybersecurity Reference Architectures (MCRA), “Security Roles and Responsibilities” refers to the assignment of specific tasks and responsibilities related to the security of an organization’s systems and networks to specific individuals or groups. This includes defining the roles and responsibilities of different teams or departments within the organization, as well as the roles and responsibilities of external partners and stakeholders.
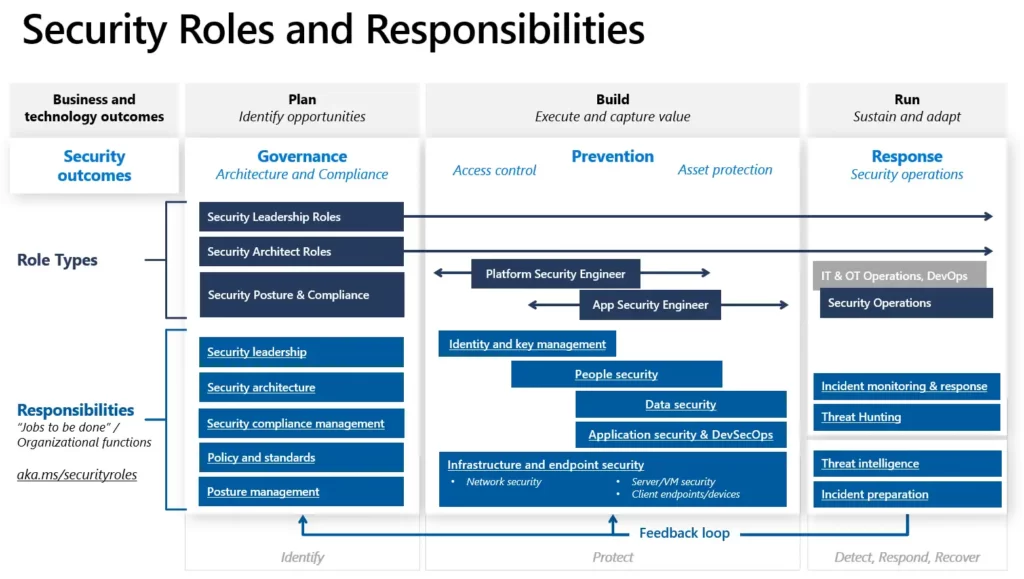
The MCRA recommends that organizations establish clear roles and responsibilities for their security teams and other relevant groups to ensure that all necessary tasks are being carried out effectively. This includes defining roles such as security architects, security engineers, security analysts, and security administrators, and assigning specific tasks and responsibilities to each role.
The MCRA also recommends establishing clear lines of communication and collaboration between security teams and other groups within the organization, such as IT, operations, and business units. This helps to ensure that security is integrated into all aspects of the organization’s operations and that all relevant parties are aware of their roles and responsibilities in supporting the organization’s security efforts.
Overall, establishing clear roles and responsibilities is an important aspect of building a strong and effective cybersecurity strategy, as it helps to ensure that all necessary tasks are being carried out in a coordinated and efficient manner.
You may also want to read this article: Importance of Cyber Security in the Digital Era.
Why use the MCRA?
We have seen these diagrams used for several purposes including
Starting template for a security architecture – The most common use case we see is that organizations use the document to help define a target state for cybersecurity capabilities. Organizations find this architecture useful because it covers capabilities across the modern enterprise estate that now spans on-premise, mobile devices, multiple clouds, and IoT / Operational Technology.
Comparison reference for security capabilities – Some organizations use this to compare Microsoft’s recommendations with what they already own and have implemented. Many organizations find that they already own quite a bit of this technology already and weren’t aware of it.
Learn about Microsoft capabilities – We have also seen this used as a learning tool. Note that in presentation mode, each capability has a “ScreenTip” with a short description of each capability + a link to the documentation to learn more.
Learn about Microsoft’s integration investments – The architecture helps architects and technical teams identify how to take advantage of integration points within Microsoft capabilities and with existing security capabilities.
Learn about Cybersecurity – Some folks, particularly those new to cybersecurity, use this as a learning tool as they prepare for their first career or a career change.
External references
Microsoft Cybersecurity Reference Architectures (Microsoft Learn)