Imagine a world where processes in a computer system whisper secrets to each other, unseen yet essential. This is the world of named pipes – a fundamental yet often overlooked aspect of inter-process communication (IPC). Named pipes, akin to hidden conduits, allow separate processes to communicate and share data seamlessly, regardless of their origin or destination.
In this article, we delve into the evolution, functionality, and pivotal role of named pipes in both Unix and Windows systems, providing a comprehensive guide that unravels their complexities and showcases their modern-day applications.
Table of Contents:
- Understanding Named Pipes
- Historical Evolution of Named Pipes
- Named Pipes in Unix and Unix-like Systems
- Named Pipes in Windows Environments
- Practical Guide and Best Practices
- Conclusion
- References
1. Understanding Named Pipes
Named pipes, a cornerstone of inter-process communication (IPC), are a sophisticated method for data transfer between processes. Unlike anonymous pipes which are transient and exist only during the lifespan of a process, named pipes are more persistent and can be accessed by unrelated processes. In essence, a named pipe appears as a file in the file system, but instead of storing data permanently, it serves as a conduit for data transfer between processes.
Named pipes support both synchronous and asynchronous communication, and can be configured for one-way or duplex communication. They are particularly useful in scenarios where multiple clients need to communicate with a server process, or when processes are running on different machines.
How Named Pipes Work in IPC
In IPC, named pipes function like a first-in-first-out (FIFO) queue. One process writes data to the pipe, and another process reads from it. If the pipe is empty, the reading process waits (blocks) until data is available. Similarly, if the pipe is full, the writing process must wait until space becomes available.
In Unix-like systems, named pipes are created using commands like mkfifo, and can be accessed using standard file I/O operations. In Windows, named pipes are created and accessed using specific API functions like CreateNamedPipe and OpenFile.
Named pipes facilitate data flow control, allowing processes to send structured data streams. This is particularly important in networked applications or distributed computing, where different components need to communicate reliably and efficiently.
2. Historical Evolution of Named Pipes
Early Days in Unix
The concept of named pipes originated in Unix systems as an extension of the traditional pipe mechanism. The idea was to enable IPC that extended beyond the lifespan of the parent process and could be accessed by different processes, possibly initiated by different users. Named pipes in Unix are files within the file system, and can be created and accessed using standard Unix commands.
Introduction in Windows Systems
Microsoft introduced named pipes in Windows to facilitate IPC, particularly in networked and client-server environments. Windows named pipes extended the functionality by incorporating network communication, allowing pipes to be used over a network, and supporting more complex data flow controls. This feature was crucial for enterprise applications and server-client architectures prevalent in Windows-based environments.
Comparative Evolution
Comparatively, while Unix and Windows share the basic concept of named pipes, their implementations and use-cases diverge significantly. Unix named pipes are simpler and more integrated with the file system, making them ideal for script-based and command-line applications. Windows named pipes, on the other hand, offer more advanced features like remote communication, making them suitable for complex applications, including network services and distributed systems.
The evolution of named pipes in both Unix and Windows reflects the broader development trends in these operating systems. In Unix, the emphasis was on simplicity and compatibility with existing file system paradigms. Windows, with its focus on graphical user interfaces and networked environments, adapted named pipes to suit more complex and varied communication needs.
Through these evolutionary paths, named pipes have remained a vital component in IPC, adapting and evolving to meet the changing demands of computing environments and applications.
3. Named Pipes in Unix and Unix-like Systems
Creation and Usage
In Unix and Unix-like systems, named pipes are created using the mkfifo command or the mknod system call. These commands create a pipe file in the filesystem, which does not contain data in the traditional sense but serves as a communication endpoint between processes.
To use a named pipe, one process writes data into the pipe using standard file writing commands, while another process reads this data using file reading commands. This facilitates a clear, unidirectional flow of data. If required, two pipes can be set up for bidirectional communication.
Real-world Examples
Named pipes are often used in scripting and command-line operations. For instance, in a backup script, a named pipe could be used to create a compressed archive of files without needing a temporary storage space. They are also employed in logging systems where multiple processes need to send log messages to a central logging process.
Another example is in the implementation of client-server models where the server process creates a named pipe and multiple client processes communicate with the server by writing to or reading from this pipe.
Technical Specifications and Commands
- Creation:
mkfifo pipe_nameormknod pipe_name p - Usage: Open the pipe file using standard file open commands (
open,read,write). - Permissions: Named pipes respect Unix file permissions, allowing control over which users can read from or write to the pipe.
4. Named Pipes in Windows Environments
Detailed Functionality
In Windows, named pipes are more complex and offer functionalities like network communication, enabling their use over a LAN or WAN. Windows named pipes can operate in both message mode and byte-stream mode, and they support full-duplex communication, meaning that data can flow in both directions simultaneously.
API and Function Calls
Named pipes in Windows are created and accessed through a set of specific API calls:
- Creation:
CreateNamedPipe()creates an instance of a named pipe. - Connection:
ConnectNamedPipe()is used by the server to wait for a client to connect. - Reading/Writing:
ReadFile()andWriteFile()functions are used to read from and write to the pipe. - Closing:
CloseHandle()is used to close the pipe.
Practical Use Cases
In Windows, named pipes are frequently used in networked and distributed applications. For example, in a database application, clients on different machines can use named pipes to communicate with a central database server.
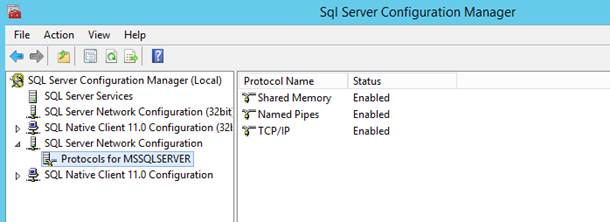
They are also used in enterprise-level applications for inter-process communications, especially in scenarios where processes might be running on different machines across a network. Another application is in debugging and logging frameworks where data needs to be reliably transferred between different components of an application or between different applications.
5. Practical Guide and Best Practices
Step-by-Step Examples
- Creating a Named Pipe in Unix:
- Use
mkfifoto create a pipe:mkfifo /tmp/my_pipe. - Write to the pipe:
echo "Hello" > /tmp/my_pipe. - Read from the pipe in another terminal:
cat /tmp/my_pipe.
- Use
- Setting Up a Named Pipe in Windows:
- Use the
CreateNamedPipeAPI to create a pipe. - Use
ConnectNamedPipeto wait for a client connection. - Implement reading and writing using
ReadFileandWriteFile.
- Use the
Common Pitfalls and How to Avoid Them
- Deadlock: Occurs when both processes wait for each other. Avoid this by ensuring proper synchronization.
- Buffer Overflow: Can happen in byte-stream mode. Implement proper buffer size checks.
- Broken Pipe Errors: Handle these gracefully by implementing error checking in your read/write logic.
Tips for Optimizing Performance
- Use Asynchronous Communication: Especially in networked environments to prevent blocking operations.
- Proper Buffer Management: Use optimal buffer sizes to balance memory usage and performance.
- Close Pipes Properly: Ensure that pipes are closed after communication is done to release resources.
6. Conclusion
The concept of Named pipe stands as a testament to the ingenuity of inter-process communication in computing. It bridges disparate processes, allowing them to communicate seamlessly across different environments, be it within the same system or across a network. Its versatility, from simple script integrations in Unix to complex networked applications in Windows, underscores their enduring relevance. As we continue to evolve in the digital landscape, the principles and functionalities of named pipes remain crucial, reminding us of the power of well-orchestrated process communication.
7. References
- “UNIX Network Programming” by W. Richard Stevens.
- “Windows System Programming” by Johnson M. Hart.
- Named Pipes (Microsoft Docs)
- Named Pipe Client