Category: Network Security
-

What To Do When Your Firewall Fails
Learn actionable steps for crisis management in cybersecurity. This guide helps you prepare for and respond to firewall failures effectively.
-

Transport Layer Security (TLS): Beyond the Basics
Unlock the secrets of Transport Layer Security (TLS) to ensure optimal data security. This comprehensive guide explores TLS protocols, encryption, myths, and more.
-

Disposable Virtual Numbers: Your Ultimate Guide to Digital Privacy
Unlock the power of digital privacy with disposable virtual numbers. Learn how they work, their benefits, and how to procure them for ultimate online safety.
-
Windows Kernel Attacks: Unveiling the Shadowy Underbelly
Explore the hidden dangers lurking in the Windows Kernel. This article dives deep into various types of attacks, famous examples, and how to defend against them.
-

Demystifying SQL Injection Types: Threats and Safeguards
Explore SQL injection types, the stealthy exploits threatening databases. Learn how to safeguard your systems against these cunning attacks.
-

Why Encrypted Passwords Are Non-Negotiable
Discover why encrypted passwords are crucial for safeguarding data. Learn about encryption methods, vulnerabilities, and best practices in this comprehensive guide.
-

Securing Your Website: A Guide to HTTP Header Vulnerabilities
Learn about the common security risks associated with HTTP headers. This guide explores vulnerabilities that every website owner should be aware of, and how to secure your website against them.
-

Security Devices in Computer Networks Unveiled
Dive into the essentials of security devices safeguarding computer networks. Explore their roles, types, and why they’re pivotal for digital safety.
-
The Role of SSL in Today’s Cybersecurity Landscape
Explore the indispensable role of SSL in cybersecurity, ensuring secure data transfer and bolstering trust in the digital ecosystem.
-
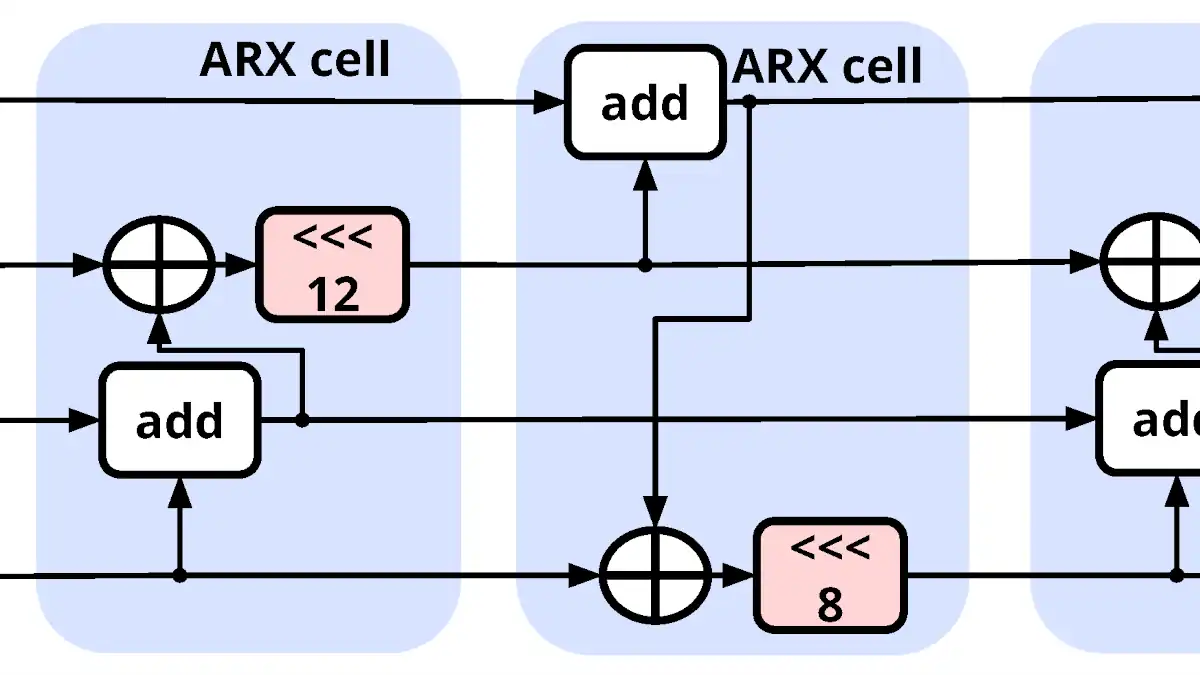
ChaCha20: The Dance of Cryptography
Dive deep into ChaCha20’s intricate dance of encryption. Explore the mathematics and design that make this cryptographic algorithm both potent and elegant.
-

Phishing Exposed: Understanding Digital Deception
Delve deep into the dark world of Phishing, as we unravel the mechanics of this notorious cyber menace, empowering you to navigate the digital realm securely
-
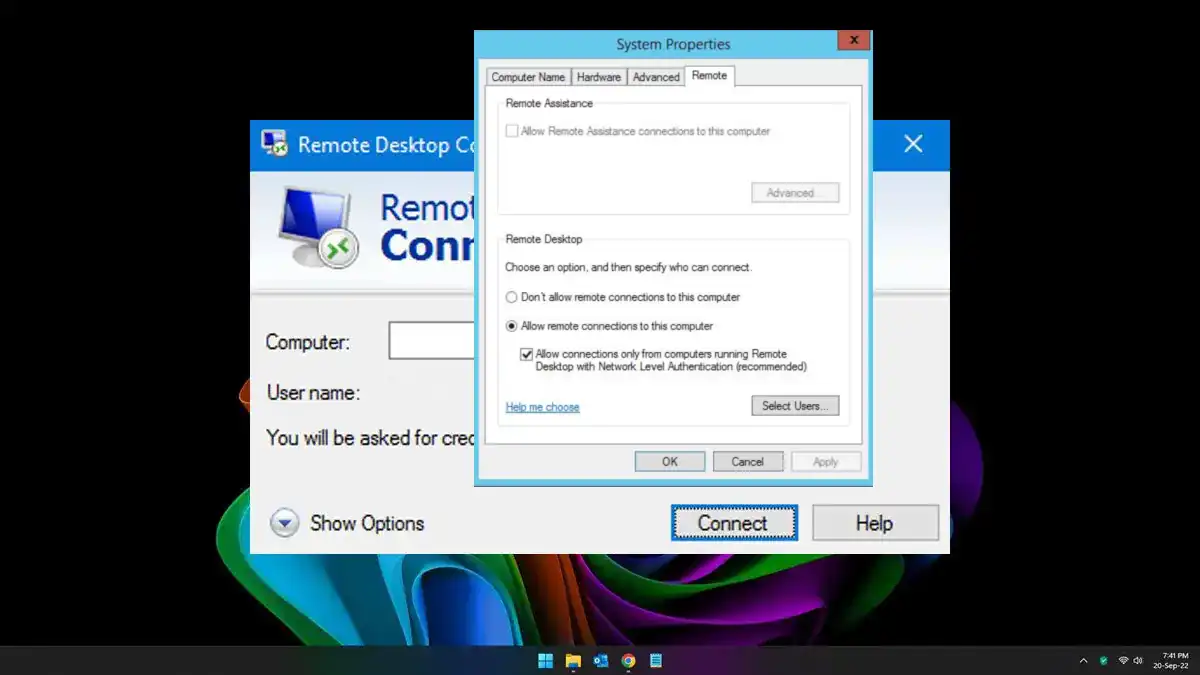
Network Level Authentication (NLA): Securing Connections
Don’t miss this beginner-friendly guide to understanding the mechanism of Network Level Authentication (NLA).