In the vast expanse of digital security, names and jargons emerge like stars, blinking in and out of relevance as technology evolves. Yet, some linger, shining brighter with every passing year due to their robustness, speed, and elegance. In this celestial scape, ChaCha20 gleams prominently.
In this article:
- What is ChaCha20?
- ChaCha20 vs. AES: Comparing Performance and Security
- The Role of Poly1305: Understanding ChaCha20-Poly1305 Authentication
- Dancing with Numbers: The Mathematics behind ChaCha20
- Conclusion
If you’ve ever wondered how data remains secure as it pirouettes across networks, or how we maintain privacy in an age teeming with cyber threats, then you’ve chanced upon the right article. Let’s delve into the world of ChaCha20 and uncover the magic behind this cryptographic star.
What is ChaCha20?
ChaCha20 is not a new dance move, though its name might suggest so. It’s a stream cipher—a means of encrypting data—that came into the limelight as a faster and, in many respects, more secure alternative to prevailing cryptographic standards.
Designed in 2008 by the renowned cryptographer Daniel J. Bernstein, ChaCha20 is a modification of the Salsa20 cipher, another creation of Bernstein. With its 20-round structure, ChaCha20 makes for an enticing blend of security and performance. Unlike block ciphers, which encrypt data in chunks or blocks, stream ciphers generate a keystream, a sequence of random bits that are combined (typically XORed) with plaintext bits to produce the ciphertext.
The strength of ChaCha20 doesn’t merely lie in its efficiency but also in its simplicity. Its design is straightforward, making it less prone to vulnerabilities that may arise from complex structures. Furthermore, ChaCha20 boasts of robust resistance against various types of attacks, making it a preferred choice for many security protocols, including TLS and certain VPNs.
ChaCha20 vs. AES: Comparing Performance and Security
While AES (Advanced Encryption Standard) has been the gold standard for encryption for many years, ChaCha20’s emergence brought forth an intriguing counterpart in the realm of secure data encryption. How do the two stack up against each other?
Performance
- AES: Its performance is intrinsically tied to hardware. In systems equipped with AES hardware acceleration (like the AES-NI instruction set in many modern processors), AES can be blazingly fast. However, in systems lacking this hardware support, its performance can falter.
- ChaCha20: One of ChaCha20’s primary design goals was efficiency across platforms. It offers consistently high performance, whether on high-end servers, older hardware, or even mobile devices. This cross-platform consistency makes ChaCha20 particularly appealing for diverse applications.
Security
- AES: Over the years, while certain theoretical vulnerabilities have been identified in AES (especially with reduced-round variants), its full version remains secure against known cryptanalytic attack vectors. Its longevity in the field and extensive analysis by cryptographers worldwide affirm its robust security profile.
- ChaCha20: Designed as an improvement over Salsa20, ChaCha20 has proven resilient against various cryptographic attacks. Its 20-round structure offers a robust security margin. Moreover, its straightforward design minimizes the surface for potential vulnerabilities.
In summary, while AES remains an industry stalwart, ChaCha20 presents a formidable alternative, especially in scenarios where hardware support for AES is absent or inconsistent. Its blend of consistent performance and proven security makes it an enticing choice in modern cryptographic applications.
The Role of Poly1305: Understanding ChaCha20-Poly1305 Authentication
Encryption is only half the battle when securing data. Ensuring the integrity and authenticity of information is equally crucial. This is where authentication tags, like Poly1305, play a pivotal role.
Poly1305 – What is it?
Poly1305 is a cryptographic message authentication code (MAC). In layman’s terms, it’s like a seal, verifying that the data hasn’t been tampered with during transit. Designed by the same mind behind ChaCha20, Daniel J. Bernstein, Poly1305 provides a high-speed, high-security authentication mechanism.
ChaCha20-Poly1305 – An Harmonious Duo
When combined, ChaCha20 for encryption and Poly1305 for authentication, the result is a powerful authenticated encryption with associated data (AEAD) scheme. This combined approach ensures that data is not only encrypted (kept secret) but also authenticated (verified for integrity).
Why Combine Them?
The amalgamation of ChaCha20 and Poly1305 offers several benefits:
- Efficiency: Both algorithms are designed for high-speed operations, ensuring quick encryption and authentication.
- Security: While ChaCha20 ensures data confidentiality, Poly1305 confirms that the data received is exactly what was sent, with no alterations.
- Simplicity: The combined approach reduces the need for multiple protocols or tools, streamlining cryptographic implementations.
In many modern protocols, including TLS 1.3, ChaCha20-Poly1305 is increasingly favored, especially in environments where consistent performance and robust security are paramount. As we continue our journey into the realm of encryption and authentication, understanding this harmonious duo’s synergy becomes instrumental in appreciating the layered intricacies of data security.
Dancing with Numbers: The Mathematics behind ChaCha20
Encryption, at its heart, is an intricate ballet of mathematics. ChaCha20, with its evocative name, invites us into a mesmerizing dance, intricately weaving numbers, algorithms, and logic.
The Quarterround Function:
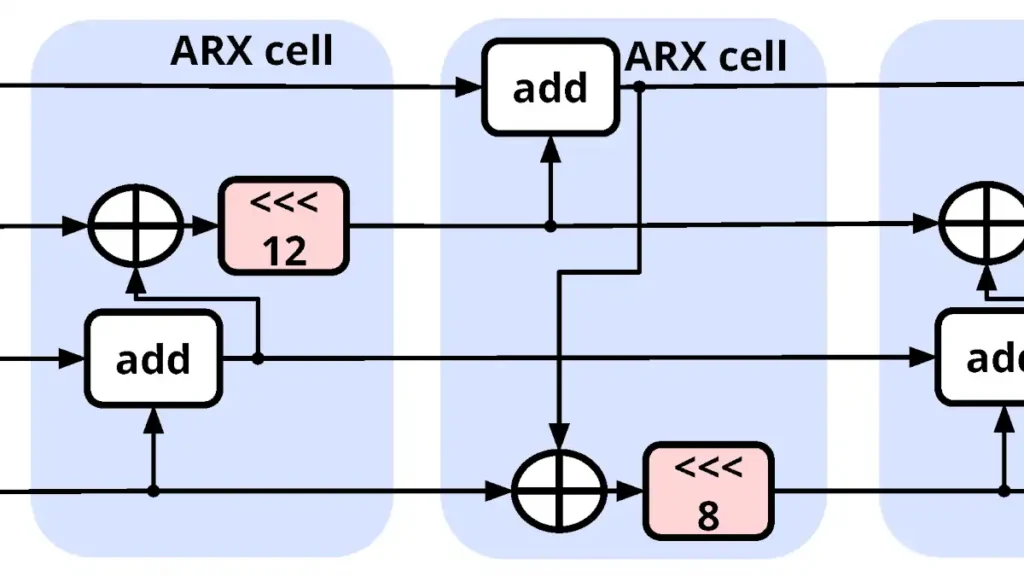
The cornerstone of ChaCha20’s encryption process is its quarterround function. In essence, this function shuffles and transforms input values, ensuring the encrypted output appears random. Without delving too deeply into bitwise operations, this function primarily involves additions, bitwise rotations, and XOR operations. A series of these quarterround operations across 20 rounds gives ChaCha20 its name and potency.
The Matrix:
ChaCha20 starts by arranging its key, nonce, and certain constants into a 4×4 matrix of 32-bit words. This matrix then undergoes numerous transformations, guided by the quarterround function, to produce a keystream.
The Keystream:
The resulting matrix post-transformation is added to the original, creating a sequence of numbers—the keystream. This keystream is what dances with our plaintext data, performing a bitwise XOR to create the encrypted ciphertext.
Security Implications:
The mathematics of ChaCha20 ensures that, even if attackers know parts of the keystream or the plaintext, discerning the original key or predicting subsequent parts of the keystream remains computationally infeasible. This guarantees the confidentiality of the data and the robustness of the cipher against cryptanalytic attacks.
ChaCha20’s beauty lies not just in its efficiency but also in its mathematical elegance. Each round, each operation, is a calculated step in a dance choreographed for security, rendering the plaintext data unrecognizable and keeping prying eyes forever in the dark.
» To read next: What is SHA-256?
Conclusion
ChaCha20 stands as a testament to the idea that security need not come at the expense of efficiency or simplicity. In a digital age teeming with threats and the ever-present need for faster data transmissions, this encryption algorithm offers a balanced, robust solution. Its dance—a blend of mathematics and design—ensures that our data remains both secure and accessible, meeting the demands of modern applications and networks.
As we peer into the future of cryptography, it’s evident that algorithms like ChaCha20 will continue to play a pivotal role, guiding us securely through the evolving landscape of the digital realm.