In a world that’s more connected than ever, the Global System for Mobile Communications (GSM) stands as a linchpin of mobile technology. Developed initially for Europe but adopted worldwide, GSM revolutionized how we communicate on the go.
This article aims to provide a deep dive into GSM’s architecture, security protocols, and its role in shaping today’s mobile landscape. Whether you’re a tech enthusiast or a seasoned professional, this comprehensive guide will give you a thorough understanding of what GSM is, why it matters, and where it’s headed.
What is GSM (Global System for Mobile Communications)?
Global System for Mobile Communications, commonly known as GSM, is a standard for digital cellular networks that has revolutionized the landscape of mobile communications. Originating in Europe in the early 1990s, GSM has now become a global phenomenon, with widespread adoption across Europe, Asia, Africa, and many other parts of the world.

SMS and MMS
Not merely limited to voice communication, GSM provides a multi-faceted platform for a broad array of services. It supports voice calls, SMS (Short Message Service), MMS (Multimedia Messaging Service), and even data transmission up to certain speeds. Unlike its predecessor, the analog Advanced Mobile Phone Service (AMPS), GSM offers superior speech quality and the ability to use the same phone and number in multiple countries through its roaming capabilities.
One of the defining features of GSM is its use of a SIM card (Subscriber Identity Module), which stores user information and allows for easier switching between devices. This modular design has influenced subsequent mobile technologies and has become a staple in modern cellular networks.
Packet-switched networks
Furthermore, GSM has the capability to interface with packet-switched networks, providing the foundational technology for 3G and subsequent cellular technologies. This enables seamless integration with internet-based services and applications, making it a cornerstone in the formation of the current mobile ecosystem.
GSM operates on various frequency bands, including but not limited to 850 MHz, 900 MHz, 1800 MHz, and 1900 MHz, allowing it to adapt to different regulatory environments and to provide service in various geographical terrains.
How it works
In its Phase 1 implementation, GSM employs a dual approach for media access control. Firstly, it uses Frequency Division Multiple Access (FDMA) to separate the full-duplex communication. Secondly, it incorporates Time Division Multiple Access (TDMA) for further optimization. These methods work together to provide seamless, full-duplex communication. Importantly, this happens over two specific frequency bands, which fall within the 862-to-960-MHz range. This range is part of the electromagnetic spectrum regulated by the World Association of Radio Communications (WARC). These two frequency bands are
- The 890-to-915-MHz band for mobile-to-base (uplink) communication
- The 935-to-960-MHz band for base-to-mobile (downlink) communication
Carrier signals are spaced 200 kHz apart within these bands to provide 124 pairs of superchannels based on frequency-division multiplexing (FDM), each of which is then subdivided into eight traffic channels using time-division multiplexing (TDM). Each channel carries voice communication at 13 Kbps (or 9.6 Kbps for data transmission). GSM thus provides 992 full-duplex channels for voice communication. Power classes for GSM mobile units range from 0.8 through 2.0 watts transmission power for handsets to 8 through 20 watts for vehicle-mounted units. Approximately half of a GSM transmission consists of overhead for signaling, such as synchronization and error handling. Such high overhead is typical in cellular phone systems, and is necessary – not so much because of external interference of buildings and other structures, but because of internal interference due to crosstalk between channels and across cell boundaries.
Key-based encryption
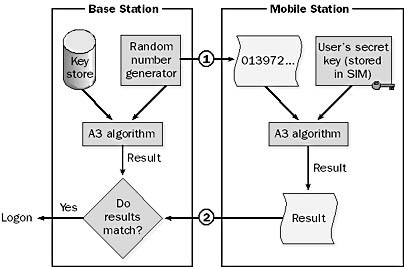
GSM boasts a secure system that hinges on key-based encryption. This is used for both authentication and optional data transfer. Let’s consider what happens when a mobile user initiates a call. First, the user dials a number. Next, the mobile unit reaches out to the base station for authorization. In response, the base station generates a random number. This number is then sent to the mobile unit.
Now, the mobile unit takes action. It combines this random number with a secret key. This key is stored on the phone’s Subscriber Identity Module (SIM) card. It employs an encryption algorithm called A3 for this process. The outcome is then sent back to the base station.
Simultaneously, the base station performs its own calculations. It holds private keys for all its subscribers in a database. It uses the same A3 algorithm to merge the random number with the caller’s private key. Finally, the base station compares its result with the one received from the mobile unit. If they match, the user gains access to the system.
Call Forwarding
GSM Phase 1 supports call forwarding, global roaming, call barring, and other features. On the other hand, GSM Phase 2 adds additional features such as the following:
- Short message service for sending and receiving short text messages using phones
- Call holding, call waiting, and caller ID
- Multiparty calling supporting up to five parties per call
- Mobile fax and data services
GSM Phase 2+ includes support for data transmission at 64 Kbps and higher, packet radio, virtual private networks, enhancements to the SIM card, higher spectral efficiency, integration with satellite links, and even GSM services in the local loop.
Note:
GSM has a sibling technology known as Digital Communication Service (DCS). Essentially, DCS works like GSM but operates on a higher 1.8-GHz frequency band. Moreover, DCS offers a total of 2992 voice channels. One edge DCS has over GSM is its lower power requirements for mobile units, ranging between 0.25 to 1.0 watts.
Moving on to the SIM card, it’s a petite device, roughly stamp-sized. It’s given to users upon subscribing to GSM. This card holds essential data: the user’s phone number, private key, and billing details among others. If users travel to areas with different GSM systems, there’s an easy fix. They can simply switch their SIM card into a rented, compatible phone.
Lastly, let’s talk about encryption. It follows a process similar to authentication, but with a twist. Each transmitted frame gets encrypted using a distinct random number. This multi-layered approach makes GSM messages incredibly secure. In fact, the security is so robust that some countries even bar GSM providers from encrypting user messages.