Welcome to this comprehensive guide on Kernel Mode in Windows operating systems. If you’ve ever wondered how your computer maintains a tight grip on security while executing lightning-fast operations, you’re about to dive into the answer: Kernel Mode.
This article aims to shed light on this core aspect of Windows OS, from its fundamental principles to the stark differences between Kernel Mode and User Mode. Whether you’re a tech-savvy professional or just curious about the inner workings of your computer, this guide has something for you.
In this article:
- What is Kernel Mode?
- Components Operating in Kernel Mode
- Security Aspects of Kernel Mode
- Performance Implications
- Difference between Kernel Mode and User Mode
- Transitioning Between Modes
- Case Studies and Real-world Examples
- Conclusion
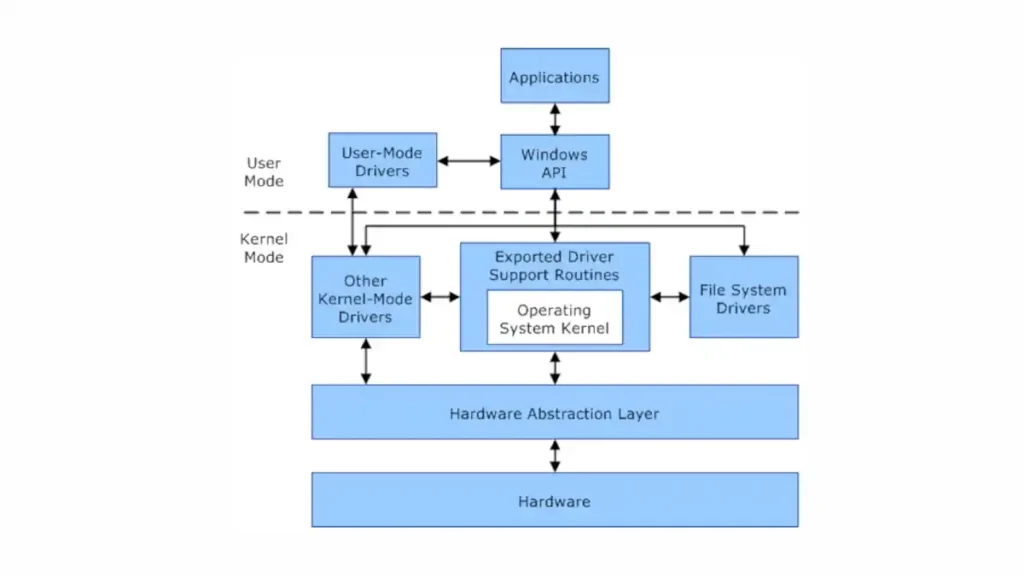
1. What is Kernel Mode?
Definition and Overview
Kernel Mode is a specialized operational state in a computer’s operating system that grants software components full control over the entire hardware. Unlike User Mode, where applications run with limited system access, Kernel Mode offers unrestricted access to system memory and external devices. In essence, it is the domain where the core parts of the operating system and essential drivers operate.
The Role of Kernel Mode in Windows OS
In the context of Windows operating systems, Kernel Mode is the linchpin that holds system stability and performance. It is responsible for tasks that require low-level access to hardware components, such as managing memory, file systems, and device drivers. When your computer boots up, the Windows Kernel takes charge, initializing hardware, loading drivers, and setting up system services—all in Kernel Mode.
Transitioning between Kernel Mode and User Mode is a fundamental operation in Windows. Applications typically operate in User Mode, making system calls to request services that only the “higher mode” can provide. The Windows Kernel, acting as a gatekeeper, handles these calls safely and efficiently, preventing unauthorized or malicious instructions from wreaking havoc on the system.
Importance in System Architecture
Kernel Mode is not merely a component but a cornerstone in system architecture. It acts as the administrative authority within the CPU, directing operations and ensuring that everything runs smoothly. The Kernel Mode’s ability to interact directly with hardware makes it a high-risk, high-reward entity. A single error could crash the system, but its functionalities are essential for robust performance, security, and hardware compatibility.
In a nutshell, Kernel Mode is the backstage manager, ensuring that the user-facing applications and services can perform at their best without compromising the system’s integrity. Its role in system architecture is so vital that understanding its operations is a must for anyone deeply involved in system design, security, or optimization.
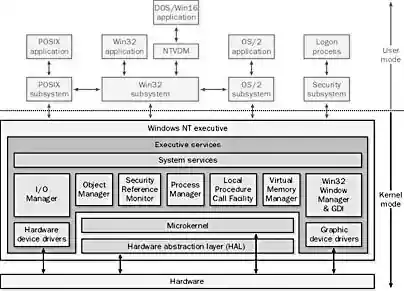
Kernel Mode on Windows 2000 (and NT)
Its processes include components of the operating system that directly manage resources on the computer, such as the following:
- Windows NT executive, which contains operating system modules that manage objects, processes, security, memory, and devices
- The kernel, which manages core operating system services
- The hardware abstraction layer (HAL), which isolates operating system code from hardware differences
2. Components Operating in Kernel Mode
Device Drivers
First on our list are device drivers, specialized software components that serve as middlemen between the operating system and hardware devices like printers, graphics cards, or network adapters. When operating in Kernel Mode, these drivers can directly access hardware, execute privileged CPU instructions, and perform operations that would be otherwise restricted in User Mode. The pivotal role of device drivers in Kernel Mode ensures seamless hardware integration but also poses risks. A poorly-written driver can cause system crashes, underscoring the importance of driver integrity and security.
System Services
Next up are system services, background processes running in Windows to manage critical tasks like networking, file systems, and security protocols. Unlike standard applications, these services have the privilege to operate in Kernel Mode when required. For example, the Windows File System Driver, responsible for reading and writing data to disk, runs in Kernel Mode to efficiently interact with hardware. Other examples include the TCP/IP stack for networking and various security services for user authentication. Operating in Kernel Mode allows these services to be both swift and secure, providing essential functionalities with reduced overhead.
Windows Kernel
Lastly, we come to the cornerstone: the Windows Kernel itself. This core component of the Windows operating system is the epitome of Kernel Mode operations. It manages essential system resources like CPU time and memory, arbitrates between conflicting hardware and software demands, and oversees system calls from User Mode applications. The Windows Kernel is what allows your system to multitask, maintain security, and deliver high performance. It works tirelessly behind the scenes, coordinating the symphony of operations that manifest as the Windows experience.
In conclusion, Kernel Mode is a complex, high-stakes arena where the essential components of the Windows operating system operate. Device drivers, system services, and the Windows Kernel itself are the key players in this realm. Understanding their roles provides insights into the underlying architecture that makes modern computing both powerful and intricate.
3. Security Aspects
Privilege Levels
First and foremost, let’s talk about privilege levels. In the realm of Kernel Mode, privilege isn’t just a theoretical concept; it’s a technical reality with profound implications. Components operating in Kernel Mode have elevated privileges that grant them unfettered access to system resources. This makes tasks like memory allocation and hardware interaction efficient, but it also calls for rigorous security measures to keep potential threats at bay.
Isolation and Gatekeeping
Next, we delve into isolation and gatekeeping. A key feature of Kernel Mode is its isolation from User Mode, which acts as a security barrier. Think of this as an exclusive club with stringent entry requirements. User Mode applications must go through a system of gates, known as system calls, to request services from the Super Mode (Kernel). These system calls are meticulously checked and filtered, allowing only valid and secure operations to pass through. This isolation mechanism plays a fundamental role in maintaining system integrity and thwarting unauthorized access.
Vulnerabilities and Risks of Kernel Mode
The privilege and power of Kernel Mode are a double-edged sword. On one hand, they enable high-speed, low-latency operations critical for system performance. On the other hand, any flaws or vulnerabilities in Kernel Mode components can wreak havoc. A compromised device driver or a bug in the kernel can lead to a full system compromise, data breaches, or even the dreaded Blue Screen of Death. Therefore, securing Kernel Mode components is not an option; it’s a necessity.
In summary, this high-stakes environment offers the advantages of speed and efficiency but also comes with potential security hazards. The intricate balance of privilege levels, stringent isolation mechanisms, and the omnipresent risk of vulnerabilities make this critical segment of the operating system a subject of ongoing scrutiny and innovation. Being aware of these aspects not only enriches our understanding of Windows architecture but also underscores the vital role that safeguarding plays in modern computing.
4. Performance Implications
Speed and Efficiency
Let’s kick things off with speed and efficiency. Operating in Kernel Mode is akin to driving in the fast lane. Here, the system components have direct access to hardware resources. No detours, no unnecessary stops. This direct route speeds up data processing and allows for more efficient use of the system’s horsepower. The result? Enhanced system performance that users can actually feel.
Context Switching
Moving on, we hit the topic of context switching. This term refers to the CPU’s ability to switch between tasks. In User Mode, the overhead for context switching is considerable. However, in Kernel Mode, the cost diminishes significantly. Why? Because the system avoids the extra steps involved in privilege elevation and security checks. So, while User Mode gets bogged down with red tape, Kernel Mode cuts through it, saving both time and computational power.
Interaction with Hardware
Lastly, we can’t overlook interaction with hardware. The components operating in Kernel Mode don’t just “talk” to hardware; they command it. Device drivers in Kernel Mode send direct instructions to hardware components. No middleman, no lag. The CPU, memory, and peripherals respond almost instantly. This instantaneous communication is pivotal for time-sensitive tasks, such as real-time data processing or high-definition video streaming.
In conclusion, Kernel Mode is a performance powerhouse. It elevates speed, curtails the costs of context switching, and streamlines hardware interaction. However, this performance comes with its own set of responsibilities and risks, which we’ve explored in previous chapters. But make no mistake: the sheer speed and its efficiency are integral to delivering a seamless user experience.
5. Difference between Kernel Mode and User Mode
Privilege Levels
First up, let’s discuss privilege levels. Kernel Mode operates with full system privileges. In contrast, User Mode functions with restricted access. Think of Kernel Mode as the VIP section, where all doors open effortlessly. User Mode, on the other hand, faces a bouncer and sometimes a locked door.
Access to Resources
Next, we turn to resource access. Kernel Mode enjoys unrestricted access to system memory and hardware. It’s like having an all-access pass at a concert. User Mode, however, has limitations. It needs permissions and, often, a go-between to interact with hardware. So, it’s more like being in general admission with a view, but not the full experience.
Error Handling
Let’s pivot to error handling. A fault in Kernel Mode can bring down the entire system. High stakes, indeed. In User Mode, errors generally impact only the offending application. The system isolates the failure, minimizing collateral damage. In simple terms, Kernel Mode errors are a house of cards; one wrong move and everything collapses. User Mode is more like a Jenga tower; remove one piece and the structure may still stand.
Speed and Efficiency
Speed also differentiates the two. Kernel Mode is a sprinter; it runs full tilt with optimized performance. User Mode is more of a distance runner; it’s concerned with pacing and security checks. While Kernel Mode zips through tasks, User Mode proceeds with caution, balancing speed with safety.
System Calls
Finally, we should consider system calls. User Mode needs to make a formal request to Kernel Mode to access system resources. It’s a bit like asking for permission to leave the room. Kernel Mode doesn’t ask; it just goes. It’s as autonomous as they come.
In summary, Kernel Mode and User Mode serve distinct roles within the Windows OS. Kernel Mode is all about speed, power, and direct access. User Mode focuses on safety, checks, and controlled access. Both are indispensable, but understanding their differences is key to grasping the complexities of system architecture.
6. Transitioning Between Modes
System Calls
Firstly, let’s tackle system calls. These are the bridges that User Mode crosses to reach Kernel Mode. Imagine it as dialing a hotline that connects you to the power center of the system.
Privilege Escalation
Now, onto privilege escalation. This is how a User Mode process gains Kernel Mode capabilities. Picture it like getting a temporary VIP pass to enter the exclusive Kernel Mode club.
Traps and Interrupts
Lastly, in this chapter, we delve into traps and interrupts. These are the system’s way of redirecting or halting processes for various reasons, such as errors or high-priority tasks. Think of them as alarm bells that alert Kernel Mode when something requires immediate attention.
7. Case Studies and Real-world Examples
Windows Kernel Attacks
First, we discuss Windows Kernel Attacks. These exploit vulnerabilities in Kernel Mode to hijack a system. It’s the equivalent of breaching the fortress’s inner sanctum.
Driver Signing Enforcement
Next up, driver signing enforcement. This is Windows’ security measure to ensure only verified device drivers operate in Kernel Mode. Picture it as a bouncer checking IDs at the club door.
Successful Utilization in Performance-Critical Applications
Lastly, let’s look at performance-critical applications. These are programs like real-time systems that benefit immensely from Kernel Mode’s speed. It’s like using a sports car instead of a bike when you need to get somewhere quickly.
Conclusion
To sum up, Kernel Mode is the brain and muscle of the Windows operating system. It’s where the real action takes place, from accessing hardware to executing instructions at lightning speed.
Even as technology evolves, its remains critical. Just like the backbone of a body, it holds everything together and enables functionality.
Future Outlook
Finally, looking ahead, Kernel Mode will continue to adapt and evolve. As security concerns and performance needs grow, so will its capabilities. In essence, it’s a dynamic entity, never static, always moving with the times.
That wraps up our comprehensive dive into the intricate world of Kernel Mode in the Windows operating system. Whether you’re a seasoned developer or a curious tech enthusiast, understanding its complexities is invaluable in today’s digital age.