In the realm of relational databases, keys play a fundamental role in maintaining data integrity and optimizing database design. They are crucial for establishing relationships between different tables, ensuring data uniqueness, and enhancing search performance.
This article delves into what keys are, the various types of keys in relational databases, and their significance in database management systems (DBMS). Whether you’re a student, professional, or enthusiast in computer engineering, understanding keys is essential for mastering database concepts.
Table of Contents:
- What is a Key in a Relational Database?
- Types of Keys in Relational Databases
- Primary Keys
- Foreign Keys
- Unique Keys
- Composite Keys
- Candidate Keys
- Surrogate Keys
- The Role of Keys in Database Integrity and Performance
- Best Practices for Choosing and Implementing Keys
- Conclusion
- References

1. What is a Key in a relational database?
A key in a relational database is a field (or a combination of fields) used to uniquely identify a record within a table. In other words, it is a column (attribute) or group of columns (attributes) used to uniquely identify records in a table of a relational database such as those created and managed by Microsoft SQL Server.
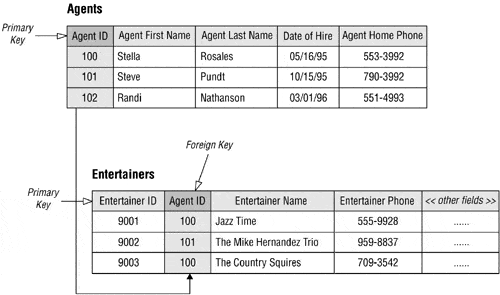
It can also establish and enforce relationships between tables, facilitating data management and retrieval processes. Keys are crucial for ensuring that each record in a database is unique, thereby preventing data duplication and maintaining data integrity.
2. Types of Keys in Relational Databases
There are two main types of database keys:
- Primary keys, which uniquely identify the rows of a table. Each row has a unique value in the primary key column or columns. Each table in a relational database should have one and only one primary key, and primary keys cannot allow nulls (NN), duplicates (ND), or no changes (NC).
- Foreign keys, are columns or groups of columns within a table that match the primary key of a different table. Foreign keys are used to define relationships between tables and to enforce referential integrity in a database by ensuring that each value in the foreign key column is actually a valid entry in the primary key column of another table.
- Unique Keys, Similar to primary keys, unique keys ensure that all values in the column are unique. However, unlike primary keys, they can accept null values.
- Composite Keys, A composite key is made up of two or more columns in a table that can be used to uniquely identify a record. The individual columns may not be unique, but their combination always produces a unique value.
- Candidate Keys: Candidate keys are columns in a table that qualify as being a primary key. A table can have multiple candidate keys, but only one can become the primary key.
- Surrogate Keys: A surrogate key is a unique identifier in a table that is not derived from application data. They are typically used when a natural primary key is either not available or not practical.
3. The Role of Keys in Database Integrity and Performance
Keys are pivotal in maintaining the structural integrity of a relational database. They ensure that each piece of data is accurately represented, easily accessible, and securely maintained through various operations such as data insertion, deletion, and updating.
- Enforcing Uniqueness and Integrity: Primary and unique keys guarantee that each record in a database is unique, preventing duplicate entries that can lead to data inconsistencies. Foreign keys maintain referential integrity by ensuring that relationships between tables remain consistent, preventing orphan records and ensuring that related data across tables is valid.
- Optimizing Data Retrieval: Keys significantly enhance the performance of data retrieval operations. Database management systems use keys, especially primary keys, to index data, making search operations faster and more efficient. This indexing is crucial for large databases where time efficiency is a key concern.
- Facilitating Relationships Between Tables: In a relational database, the association between tables is essential for complex queries and data analysis. Keys, particularly foreign keys, play a critical role in defining these relationships, allowing for the joining of tables and enabling more comprehensive data retrieval and analysis.
4. Best Practices for Choosing and Implementing Keys
Selecting the right keys and implementing them effectively is crucial for optimizing database functionality and integrity. Here are some best practices:
- Choose Primary Keys Carefully: Select primary keys that are guaranteed to be unique and stable over time. Avoid using volatile data that might change as a primary key, such as a person’s name or email address.
- Use Surrogate Keys When Necessary: When natural keys are cumbersome or do not exist, surrogate keys can be an effective alternative. These are especially useful for large, complex databases where natural primary keys are not practical.
- Normalize Data to Reduce Redundancy: Proper database normalization helps in identifying appropriate keys by eliminating data redundancy. This process can help in distinguishing candidate, primary, and foreign keys more effectively.
- Maintain Referential Integrity: Ensure that foreign keys correctly reference primary keys in related tables. This practice is crucial for maintaining the relational aspect of the database and ensuring data consistency.
- Consider the Use of Unique and Composite Keys: Unique keys are useful for ensuring uniqueness in columns that are not primary keys. Composite keys, on the other hand, can be used when a single column is insufficient to uniquely identify a record.
5. Conclusion
Keys in a relational database are more than just columns or sets of columns; they are the foundation upon which database integrity, efficiency, and relationality are built. Understanding the different types of keys and their specific roles within the database structure is crucial for anyone involved in designing, managing, or optimizing databases. By adhering to best practices in key selection and implementation, one can ensure robust data integrity, efficient data retrieval, and a well-structured relational database design.
6. References
- Date, C. J. (2003). An Introduction to Database Systems (8th ed.). Addison-Wesley.
- Elmasri, R., & Navathe, S. B. (2016). Fundamentals of Database Systems (7th ed.). Pearson.
- Silberschatz, A., Korth, H. F., & Sudarshan, S. (2010). Database System Concepts (6th ed.). McGraw-Hill Higher Education.