What is NIST Cybersecurity Framework?
The National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) is a set of guidelines and best practices for managing cybersecurity risks in an organization. It was developed by NIST, a non-regulatory agency of the U.S. Department of Commerce, in response to Executive Order 13636, “Improving Critical Infrastructure Cybersecurity,” which was issued by President Barack Obama in 2013.
The NIST CSF is a framework, not a standard or a set of specific requirements. It is designed to be flexible and adaptable so that organizations can use it to address their particular cybersecurity risks in a way that makes sense for their business.
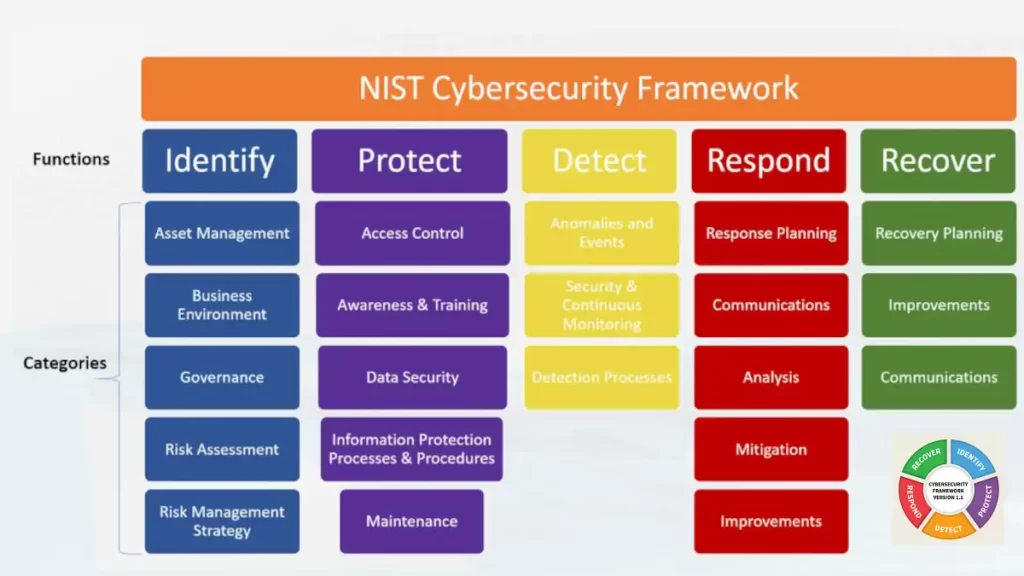
The NIST CSF is organized around five core functions:
These functions provide a structure for understanding, prioritizing, and managing cybersecurity risks, and they can be used to guide the development of an organization’s cybersecurity program.
Organizations widely use the NIST CSF in the public and private sectors, and it is considered to be a leading framework for managing cybersecurity risks. It is designed to be compatible with other standards and best practices, and it can be used in conjunction with other frameworks, such as the ISO 27001 standard for information security management.
Below is a brief overview of the five core functions of the NIST CSF:
Identify
This function involves understanding the organization’s assets, threats, vulnerabilities, and impacts, as well as the organization’s current cybersecurity posture. It also involves identifying the legal, regulatory, and business requirements that the organization must comply with.
Protect
This function involves implementing measures to prevent or mitigate cybersecurity incidents, such as implementing technical controls (e.g., firewalls, intrusion detection systems), physical security measures (e.g., locks, access controls), and training and awareness programs for employees.
Detect
This function involves detecting cybersecurity incidents as they occur or as soon as possible after they occur, and responding appropriately. It involves implementing monitoring and detection systems and establishing processes for detecting and responding to incidents.
Respond
This function involves taking appropriate actions to contain and mitigate the impact of a cybersecurity incident and to restore normal operations as soon as possible. It involves establishing processes for responding to incidents, including incident response plans and procedures.
Recover
This function involves returning the organization to normal operations after a cybersecurity incident. Includes activities such as restoring systems and data and conducting a post-incident review to identify lessons learned and areas for improvement.