Definition of FIREWALL in Network Encyclopedia.
What is a Firewall?
We call a Firewall to any system or device that allows safe network traffic to pass while restricting or denying unsafe traffic. Firewalls are usually dedicated machines running at the gateway point between your local network and the outside world, and are used to control who has access to your private corporate network from the outside – for example, over the Internet. More generally, a firewall is any system that controls communication between two networks.
In today’s networking environment in which corporate networks are connected to the Internet – inviting hackers to attempt unauthorized access to valuable business information – a corporate firewall is essential.
How does Firewall work?
In its simplest form, a firewall is essentially a kind of router or computer with two network interface cards that filters incoming network packets. This device is often called a packet-filtering router.
By comparing the source addresses of these packets with an access list specifying the firewall’s security policy, the router determines whether to forward the packets to their intended destinations or stop them.
The firewall can simply examine the IP address or domain name from which the packet was sent and determine whether to allow or deny the traffic. However, packet-filtering routers cannot be used to grant or deny access to networks on the basis of a user’s credentials.
Packet-filtering routers can also be configured to block certain kinds of traffic while permitting others. Usually, this is done by disabling or enabling different TCP/IP ports on the firewall system. For example, port 25 is usually left open to permit Simple Mail Transfer Protocol (SMTP) mail to travel between the private corporate network and the Internet, while other ports (such as port 23 for Telnet) might be disabled to prevent Internet users from accessing other services on corporate network servers.
The difficulty with this approach is that the size of the access list for the firewall can become huge if a large number of domains or ports are blocked and a large number of exceptions are configured. Some ports are randomly assigned to certain services (such as remote procedure call services) on startup; it is more difficult to configure firewalls to control access to these ports.
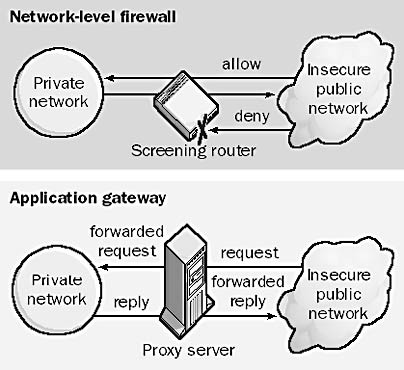
Network-level firewall
The simple firewall just described is sometimes called a network-level firewall because it operates at the lower levels of the Open Systems Interconnection (OSI) reference model for networking. Network-level firewalls are transparent to users and use routing technology to determine which packets are allowed to pass and which will be denied access to the private network. Network-level firewalls implemented solely on stand-alone routers are called packet-filtering routers or screening routers.
Learn what Edge Traversal is!
Circuit-level Gateway
Another type of firewall is a circuit-level gateway, which is usually a component of a proxy server. Circuit-level gateways essentially operate at a higher level of the OSI model protocol stack than network-level firewalls do. With a circuit-level firewall, connections with the private network are hidden from the remote user. The remote user connects with the firewall, and the firewall forms a separate connection with the network resource being accessed after changing the IP address of the packets being transmitted in either direction through the firewall. The result is a sort of virtual circuit between the remote user and the network resource. This is a safer configuration than a packet-filtering router because the external user never sees the IP address of the internal network in the packets he or she receives, only the IP address of the firewall. A popular protocol for circuit-level gateways is the SOCKS v5 protocol. (Check Circuit-level gateway article)
Application-level firewall
Another more advanced type of firewall is the application-level firewall (or application gateway), which is also usually a component of a proxy server. Application gateways do not allow any packets to pass directly between the two networks they connect. Instead, proxy applications running on the firewall computer forward requests to services on the private network, and then forward responses to the originators on the unsecured public network. Application gateways generally authenticate the credentials of a user before allowing access to the network, and they use auditing and logging mechanisms as part of their security policy.
Application gateways generally require some configuration on the part of users to enable their client machines to function properly, but they are more atomic in their configurability than network-level firewalls. For example, if a File Transfer Protocol (FTP) proxy is configured on an application gateway, it can be configured to allow some FTP commands but deny others. You could also configure an SMTP proxy on an application gateway that would accept mail from the outside (without revealing internal e-mail addresses), and then forward the mail to the internal mail server. However, because of the additional processing overhead, application gateways have greater hardware requirements and are generally slower than network-level firewalls.
NOTE
Microsoft Proxy Server includes the functions of network-level firewalls, circuit-level firewalls, and application gateways, enabling businesses to protect their sensitive corporate networks from attack over the Internet.
Configuring a packet-filtering firewall
The best way to begin configuring a packet-filtering firewall is to block all packets at first and then start allowing access to the internal network on a case-by-case basis. Make sure that internal network addresses do not cross the firewall to the outside world and do not store sensitive data on the machine running the firewall software itself. Treat your firewall machine as expendable – the worst possibility should be a hacker’s damage to the firewall; this would simply leave your private network securely disconnected from the outside world. You can disable all unnecessary network services on your firewall machine to protect the firewall itself from attack.
If you are concerned only about controlling outgoing access from your network, and in addition, your users do not need to be able to remotely access your network over the Internet, a packet-filtering router or circuit-level gateway type of firewall is probably sufficient. For users who frequently need to remotely access your network, however, an application gateway is generally best.
Check out our very extended article about Firewalls called Why does my company need a firewall right away!