Definition of Public Key Cryptography in the Network Encyclopedia.
What is Public Key Cryptography?
Public Key Cryptography, also known as asymmetric cryptography, is a popular encryption method developed by Martin Hellman and Whitfield Diffie in 1976 that is used for securing the transmission of data over distrusted networks such as the Internet.
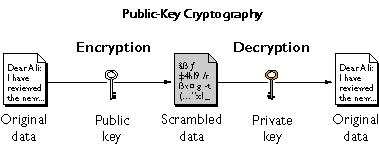
How It Works
Traditional cryptography involves a private or secret key that was shared by the individuals involved in the transmission. The key is a mathematical entity that the sender can use to encrypt a message and the receiver can use it to decrypt it. This traditional form of cryptography is known as secret key cryptography or symmetric cryptography. The main problem with this form of cryptography is the question of how the owner of the key can securely transmit the key. In other words, the main problem is one of key management – how to create, store, and transmit the key to those who will need it to decrypt messages sent to them.
Public key cryptography solves this problem by creating a set of two different keys for anyone needing to transmit encrypted information. A precise mathematical relationship exists between the two keys, which together are called a key pair. Both keys are produced at the same time using a mathematical algorithm such as RSA. As a result, when either one of the two keys is used to encrypt a message, the other can be used to decrypt it.
»» To read next: Knowing the difference between port 443 and port 80!
The two keys in a key pair are as follows:
- The private key: Held privately by the owner of the key pair and kept secret from anyone else. The responsibility for safe storage of the private key rests entirely with the key pair owner, who has no need to transmit the private key to others.
- The public key: Made available by the key pair owner to anyone who requests it. Because the public and private keys are related mathematically, in principle someone could take another person’s public key, perform complex mathematical calculations on it, and extract the corresponding private key. The solution is to use keys sufficiently long and with a sufficiently complex mathematical relationship so that it is all but impossible to extract the private key from the public one.
Once a key pair is generated for someone, that person can use it to encrypt messages and to digitally sign messages so that the recipient can be sure of the identity of the sender.
Of course, the whole public key cryptography system is ultimately founded on trust. All persons who are issued key pairs must trust the third-party authority who provided the key pairs. This trusted authority is called a certificate authority (CA). Someone who wants to obtain a key pair from a CA must contact the CA and present proof of identity. This could involve a face-to-face meeting, examination of a driver’s license with a photograph, or some other method of establishing a user’s identity.
Microsoft Certificate Server
Network administrators can use Microsoft Certificate Server, which is included in the Microsoft Windows NT 4 Option Pack, to establish their own CAs. Users can then transmit encrypted and digitally-signed e-mail messages by using the Microsoft Exchange Server or establish secure Web sites that use the Secure Sockets Layer (SSL) protocol with Internet Information Services (IIS).