The term “Root” weaves through the fabric of computer science and technology with varied and significant meanings. At its core, Root embodies the concept of origin or base—whether referring to the highest-level directory in a filesystem, the most powerful user account on a Unix/Linux system, the foundational object in directory services like Active Directory, or even specialized frameworks in scientific research. This article delves into these diverse interpretations, elucidating their functionalities, implications, and the interconnectedness within the technological realm. Aimed at computer science students and professionals, we embark on a comprehensive exploration to demystify the multifaceted concept of Root, ensuring clarity and insight into its pivotal roles.
In this article:
- Root in Hierarchical File Systems
- Root as the Superuser in Unix/Linux
- Root in Directory Services (e.g., Active Directory’s RootDSE)
- ROOT Framework at CERN
- Other Occurrences of Root in Computer Science
- Conclusion
1. Root in Hierarchical File Systems
Definition and Significance
In the hierarchical structure of file systems used by most operating systems (OS), the root directory stands as the foundational layer from which all other directories branch. This apex of the file system hierarchy is denoted by a forward slash (“/”) in Unix-like systems, including Linux and macOS, and a drive letter followed by a backslash (“C:”) in Windows. The root directory’s primary significance lies in its role as the singular starting point for the entire file system. From here, all files and subdirectories find their organizational structure, making it the conceptual and literal base of the digital storage landscape.
Role in Various Operating Systems
- Unix/Linux: In these systems, the root directory is the absolute beginning of the file system. It contains essential system directories such as
/bin(binary executables),/etc(configuration files), and/home(user directories), among others. The root directory’s structure is standardized to some extent across Unix-like systems, ensuring consistency and predictability in software development and system administration. - Windows: Windows operating systems conceptualize the root differently, assigning it to the base of each drive (e.g., C:, D:). The root directory of the system drive (usually C:) contains critical system folders like
Windows,Program Files, andUsers, serving a similar organizational purpose as in Unix/Linux systems but within a drive-based framework. - macOS: Following the Unix tradition, macOS uses a single root directory as the file system’s starting point. However, it presents a user-friendly face through the Finder application, which abstracts the file system’s complexity, integrating seamlessly with Unix underpinnings to provide both simplicity for users and power for developers.
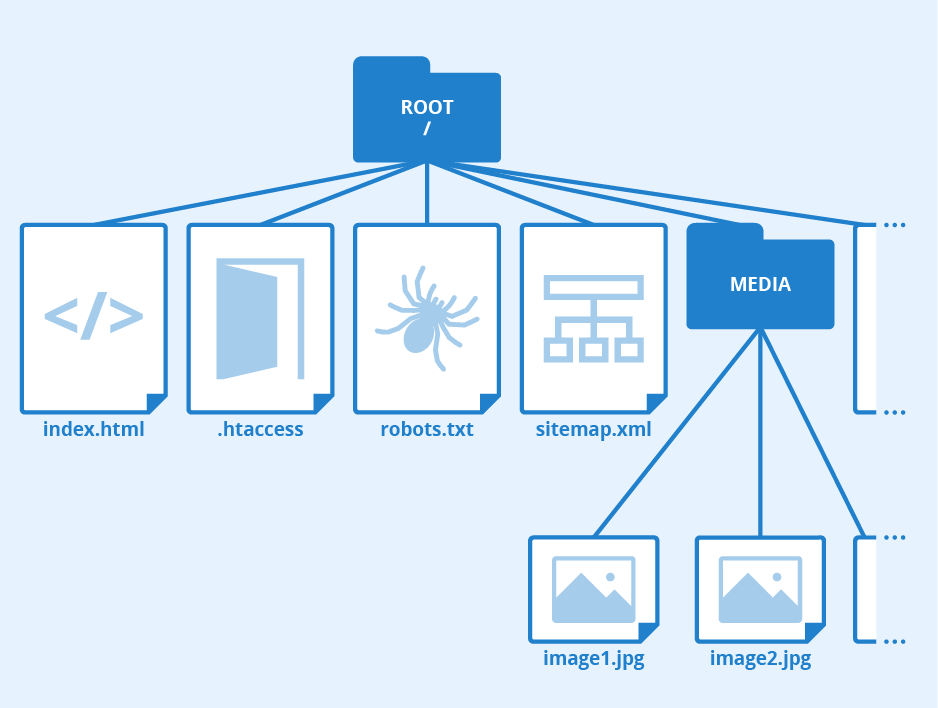
The root directory contains the tree of directories and files that make up the file system.
The symbol used to represent this directory depends on whether the file system is on a Microsoft Windows platform or a UNIX platform. Windows designates the root with a backslash (\), and UNIX uses a forward slash (/). The root directory is the first element in the absolute path of a file or directory on the file system.
2. Root as the Superuser in Unix/Linux
Origins and Implications of Root Privileges
The concept of the root user in Unix and Linux operating systems emanates from the need for a supervisory role that has unrestricted access to all commands and files within the OS. Originating from the early days of Unix, this superuser account, known simply as “root,” is endowed with the authority to perform any action, ranging from system configuration changes to the deletion of critical system files. The implications of such extensive privileges are profound, as the root account can be used to maintain, modify, or even compromise the system’s integrity and security.
Security Considerations and Best Practices
Given the power inherent to the root account, stringent security considerations are a must to prevent its misuse, whether inadvertently by the system administrator or maliciously by attackers.
- Use Sudo for Privilege Escalation: Instead of logging in as root, it’s advisable to use regular user accounts and escalate privileges using
sudofor specific tasks. This method provides an audit trail of commands executed with root privileges and limits the window of opportunity for inadvertent or malicious modifications to the system. - Disable Root SSH Login: Direct root login via SSH should be disabled in the SSH daemon configuration to prevent remote access attempts to the root account. Users should log in with their accounts and use
sudofor tasks requiring elevated privileges. - Implement Strong Authentication Measures: For accounts with the ability to escalate to root, enforce strong password policies and, where possible, two-factor authentication to enhance security.
- Regularly Review Root Access Logs and Activities: Monitoring and auditing root access and activities can help in identifying unauthorized access attempts or non-compliant actions, enabling timely responses to potential security incidents.
3. Root in Directory Services (e.g., Active Directory’s RootDSE)
Explanation of RootDSE
In the context of directory services, such as Microsoft’s Active Directory (AD), the RootDSE (Root Directory Service Entry) plays a critical role as a reference point to the directory service’s root. It acts as an access point to the configuration, schema, and naming contexts of the AD forest, without being part of the directory’s data set itself. Essentially, RootDSE provides a gateway to query and discover the directory service’s capabilities, configurations, and the structure of the directory tree, making it indispensable for administration and application integration.
Importance in Directory Architecture
The RootDSE object’s significance in directory architecture cannot be overstated. It serves several vital functions:
- Schema Discovery: Allows applications to dynamically discover and adapt to the directory schema, ensuring compatibility and leveraging the directory’s capabilities.
- Configuration Retrieval: Provides access to configuration settings of the directory service, facilitating optimized interactions and integrations.
- Namespace Navigation: Enables the determination of the directory’s naming contexts, guiding LDAP (Lightweight Directory Access Protocol) queries to the appropriate parts of the directory tree for efficient data access and manipulation.
- Service Advertisement: RootDSE can advertise supported features and services of the directory, such as LDAP version compatibility or available authentication mechanisms, allowing clients to adjust their interactions accordingly.
In essence, RootDSE underpins the adaptability and extensibility of directory services, ensuring that applications and services can effectively utilize and integrate with the directory infrastructure.
4. ROOT Framework at CERN
Overview of the ROOT Framework
The ROOT framework, developed at CERN (the European Organization for Nuclear Research), is an open-source data analysis framework used predominantly in high-energy physics. It provides a comprehensive suite of software tools designed for data processing, statistical analysis, visualization, and storage. ROOT is built on C++, leveraging its object-oriented capabilities to offer a flexible and efficient environment for dealing with the vast and complex data sets typically encountered in particle physics research.
Application in High-Energy Physics and Data Analysis
ROOT’s application in high-energy physics is extensive and multifaceted:
- Data Processing: It excels at processing and analyzing the petabytes of data generated by particle accelerators and detectors, facilitating the extraction of meaningful physics results from raw data.
- Simulation: ROOT is instrumental in simulating the interactions of particles, playing a crucial role in experimental planning and the interpretation of experimental results.
- Visualization: Its powerful visualization tools allow scientists to graphically represent data and simulation results, aiding in the comprehension and presentation of complex phenomena.
- Statistical Analysis: ROOT includes sophisticated statistical analysis capabilities, enabling precise measurement and hypothesis testing critical for validating theoretical models.
The ROOT framework’s importance extends beyond the realm of high-energy physics, finding applications in a broad range of scientific research areas that require robust data analysis and visualization tools. Its development at CERN underscores the collaborative nature of scientific inquiry, as ROOT is continuously enhanced by contributions from a global community of researchers and developers.
See: ROOT – Data Analysis Framework
5. Other Occurrences of Root in Computer Science
Root Certificates in Digital Security
Root certificates are the cornerstone of the internet’s security model, acting as trusted authorities in the digital certification hierarchy. A root certificate is a self-signed certificate that identifies the Root Certificate Authority (CA). These certificates are pre-installed in web browsers and operating systems, enabling them to trust certificates issued by these authorities for secure communications over HTTPS. The integrity and trustworthiness of root certificates are paramount, as they underpin the security of web transactions, email encryption, and more, making the management and protection of these certificates a critical security priority.
Rooting in the Context of Android Devices
Rooting refers to the process of obtaining root access on Android devices, allowing users to override manufacturer-imposed limitations and gain complete control over the device’s operating system. This process enables the installation of unapproved apps, updates, and customizations, offering enhanced functionality and personalization at the risk of potential security vulnerabilities and voiding warranties. Rooting exemplifies the users’ desire for autonomy and customization in their technological devices, reflecting the broader theme of root as a gateway to deeper system access and control.
The Mathematical Root in Algorithms and Data Structures
In computer science, the concept of the mathematical root extends beyond arithmetic, influencing algorithms and data structures. For example, the root node in a tree data structure serves as the topmost node, from which all other nodes descend. The significance of the root node lies in its role as the entry point for traversals and operations within the tree, affecting efficiency and performance in computing tasks ranging from database indexing to hierarchical data representation and processing.
6. Conclusion
The Unifying Essence of Root Across Disciplines
The exploration of Root in its various incarnations within computer science reveals a unifying essence: Root consistently symbolizes a fundamental starting point, a source of control, or a foundation from which systems and concepts grow and evolve. Whether discussing the base of a filesystem, the all-powerful superuser, the backbone of security models, or the foundational node in data structures, Root stands as a testament to the importance of foundational elements in structuring, securing, and navigating complex systems.
Its Impact on Technology and Science
The impact of Root on technology and science is profound and far-reaching. By providing a basis for organization, control, and security, Root enables the complex, hierarchical structures that underpin modern computing, from the operating systems that power our devices to the frameworks that drive scientific discovery. As technology continues to advance, the principles encapsulated by the concept of Root will remain central to the development of new systems, architectures, and innovations, underscoring the timeless relevance of foundational principles in the pursuit of knowledge and the advancement of technology.