Imagine that you’re sitting at your computer, working on important tasks, and suddenly, you find yourself in need of heightened security. It’s that moment when you press the Ctrl+Alt+Delete keys, and like a magic incantation, a new window appears, the Windows Security dialog box. What just happened here? How does this keystroke combination work, and why is it vital in the world of computing?
In this article, we uncover the mysteries of Secure Attention Sequence (SAS). We’ll delve deep into its inner workings, understand its inception, and explore its significance in modern Windows systems. By the end, you’ll have a comprehensive grasp of SAS, its evolution, and its critical role in safeguarding your digital world.
In this chapter:
- What is Secure Attention Sequence (SAS)?
- The Inception of SAS in Windows NT: A Historical Perspective
- SAS in Modern Windows Systems
- Use Cases and Security Implications
- How to Use SAS Effectively
- References
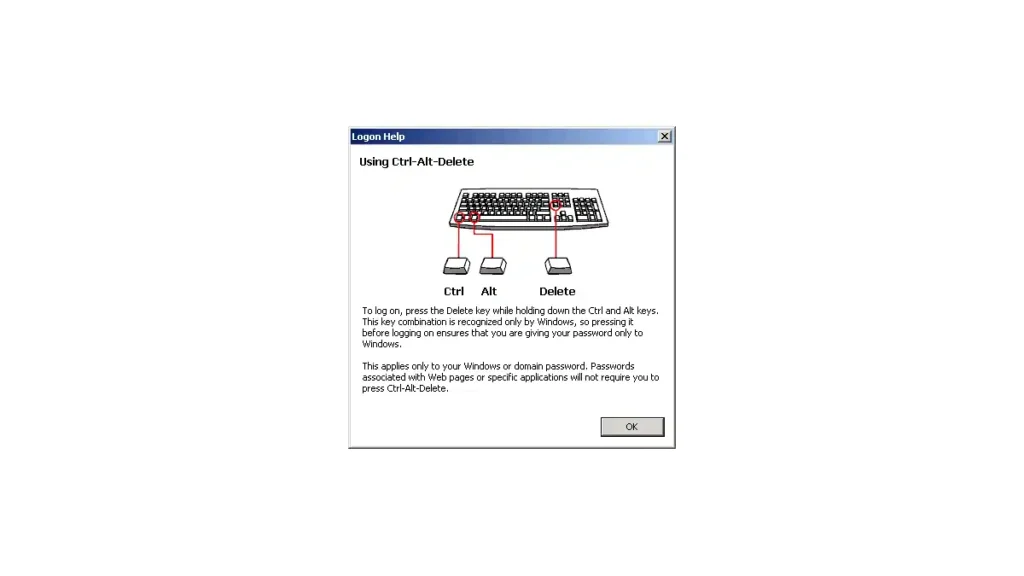
1. What is Secure Attention Sequence?
Secure Attention Sequence, often abbreviated as SAS, is a fundamental component of the Windows operating system’s security architecture. It acts as a digital guardian, ensuring that your interactions with your computer are both secure and legitimate.
At its core, SAS is a keystroke combination – Ctrl+Alt+Delete. When you press these keys simultaneously, you initiate a sequence that demands the highest level of attention from the operating system. It’s a bit like saying, “Hey, computer, stop what you’re doing, I need your full focus right now.”
But why this specific combination? Why not any other set of keys? The choice of Ctrl+Alt+Delete is deliberate and ingenious. It’s a combination that’s hard to accidentally trigger, making it ideal for critical security operations.
When SAS is invoked, it does something crucial: it creates a trusted and isolated environment within your computer, known as the Windows Security dialog box. This environment ensures that any actions you take from this point forward are genuine and secure.

In essence, SAS serves as a checkpoint, preventing malicious software or unauthorized users from intercepting your activities or attempting to deceive your computer into performing harmful actions.
In the next chapter, we’ll journey back in time to explore the origins of SAS in Windows NT, understanding how this essential security feature came into existence and why it remains indispensable in the digital age. So, fasten your seatbelts, and let’s dive deeper into the world of Secure Attention Sequence.
2. The Inception of SAS in Windows NT: A Historical Perspective
To truly appreciate the significance of Secure Attention Sequence (SAS), we must take a step back in time to the birth of this essential security feature. Our journey leads us to the early days of Windows NT, where the concept of SAS first emerged.
Origins of SAS in Windows NT
SAS made its debut in the Windows NT operating system, introduced by Microsoft in the early 1990s. At that time, the computing landscape was evolving rapidly, with networks becoming more prevalent, and the need for robust security measures became apparent.
Microsoft recognized the necessity for a mechanism that could guarantee user authentication and system integrity, especially in networked environments. This recognition paved the way for the birth of SAS.
Initial Purpose and Implementation:
The primary purpose of SAS in Windows NT was to address a critical security concern—how to ensure that the user logging into the system was indeed the legitimate user and not an impostor. The Ctrl+Alt+Delete keystroke combination was chosen for its unique properties. When pressed, it was virtually impossible for malicious software or unauthorized users to mimic accidentally, making it an excellent choice for initiating a secure and trusted environment.
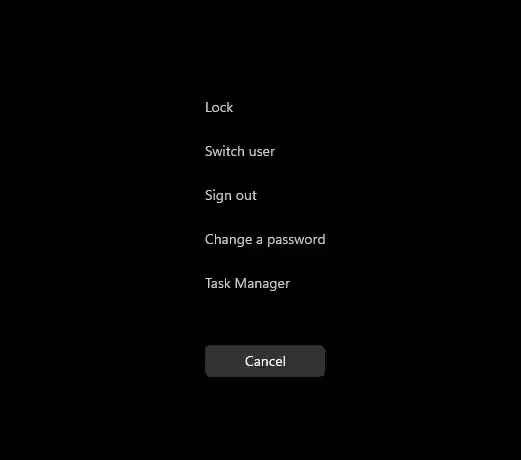
When a user pressed Ctrl+Alt+Delete, Windows NT would respond by interrupting all ongoing processes and presenting the Windows Security dialog box. This dialog box served as the gateway to essential security functions, such as logging in, changing passwords, and launching the Task Manager to monitor and manage running processes. It was essentially a checkpoint that separated legitimate user actions from potential threats.
In this way, SAS acted as the guardian of the Windows NT system, ensuring that any critical security operations were conducted in a controlled and secure environment. Its implementation was a significant milestone in the development of Windows as a secure and reliable operating system.
3. SAS in Modern Windows Systems
As we fast forward to the present day, Secure Attention Sequence (SAS) has not only survived but also evolved to meet the changing demands of modern computing environments. Let’s explore how SAS has transformed over the years and why it remains relevant in contemporary Windows versions like Windows 10 and Windows 11.
Evolution of SAS
Over the decades, SAS has undergone refinements and enhancements to keep pace with the ever-evolving threat landscape. While its core function of initiating a trusted security environment remains intact, the mechanisms behind SAS have become more sophisticated.
Modern SAS implementations include additional security features, such as biometric authentication, smart card integration, and two-factor authentication methods. These advancements make SAS even more robust in ensuring that the user’s identity is verified beyond doubt before granting access to critical system functions.
Relevance in Contemporary Windows
In the world of Windows 10, Windows 11, and beyond, SAS continues to play a pivotal role in system security. It remains the go-to method for accessing essential security functions and ensuring that user interactions with the operating system are genuine and secure.
In the context of contemporary Windows systems, SAS is especially vital in enterprise environments where network security is paramount. It serves as a key component of user authentication and access control, contributing to the overall integrity of the system.
In these modern iterations of Windows, SAS is not only a security feature but also a symbol of trust and reliability. It embodies the commitment of Microsoft to safeguarding user data and maintaining the highest standards of security in an interconnected world.
As we’ve journeyed from the origins of SAS in Windows NT to its role in today’s Windows systems, we’ve witnessed the evolution of a crucial security mechanism. In the next chapters, we’ll delve even deeper into the practical applications and security implications of Secure Attention Sequence, helping you understand its importance in the digital age.
4. Use Cases and Security Implications
In this chapter, we will explore the practical scenarios where Secure Attention Sequence (SAS) is crucial and delve into the security implications of SAS in today’s computing environment.
Practical Scenarios for SAS
- User Authentication: SAS plays a pivotal role in user authentication. When you log into your Windows system, you rely on SAS to ensure that the login credentials you provide are processed securely. It prevents malware or unauthorized applications from intercepting your login information.
- Password Changes: When you need to change your password, SAS is the gateway to this critical operation. It ensures that only you, the legitimate user, can initiate and complete this process, reducing the risk of unauthorized password modifications.
- Task Manager Access: SAS provides access to the Task Manager, a powerful tool for monitoring and managing running processes. This is essential for troubleshooting and terminating unresponsive applications, adding a layer of control to your system.
- Locking Your Computer: When you step away from your computer, pressing Ctrl+Alt+Delete and choosing the “Lock” option ensures that your system remains secure. Anyone attempting to access your computer in your absence will be prompted to enter valid credentials.
Security Implications of SAS
- Mitigating Unauthorized Access: SAS acts as a robust defense against unauthorized access attempts. By interrupting ongoing processes and creating a secure environment, it prevents malicious software from hijacking user sessions or attempting to perform harmful actions.
- Identity Verification: SAS is the first line of defense in verifying the user’s identity. This is crucial in today’s computing environment, where identity theft and cyberattacks are prevalent. It ensures that only authorized users gain access to sensitive data and system functions.
- Enhanced Network Security: In corporate environments, SAS enhances network security. It serves as a gatekeeper to sensitive resources, making it challenging for unauthorized users to compromise critical systems or steal confidential information.
- Protection Against Keyloggers: SAS is resistant to keyloggers, a type of malware that records keystrokes. Since Ctrl+Alt+Delete is a secure, low-level operation, it’s less susceptible to interception by keyloggers, further safeguarding user credentials.
In summary, SAS is a versatile tool with wide-ranging applications in ensuring system security and user authentication. Its security implications are more significant than ever in today’s digital landscape, where cybersecurity threats are constant.
5. How to Use SAS Effectively
Now, let’s explore how users and administrators can make the most of Secure Attention Sequence (SAS) to enhance security and usability.
Tips and Best Practices
- Regularly Lock Your Computer: Get into the habit of using Ctrl+Alt+Delete and selecting “Lock” when stepping away from your computer. This simple action adds an extra layer of security to your workspace.
- Keep Your Password Secure: When changing or entering passwords using SAS, ensure that you do so in a private, secure environment. Protect your login credentials from prying eyes.
- Implement Multi-Factor Authentication (MFA): Consider enabling MFA for your Windows account. This adds an additional layer of security beyond SAS, making it even more challenging for unauthorized users to gain access.
Configuring and Customizing SAS
- Advanced Security Settings: Administrators can configure SAS through advanced security policies. Customize settings such as who can use SAS, when it can be used, and which security features are enabled.
- Biometric Integration: Many modern computers and devices support biometric authentication, such as fingerprint or facial recognition. Administrators can enable and configure these features to work seamlessly with SAS.
- Training and Education: Educate users about the importance of SAS and how to use it effectively. Provide clear instructions on password changes, locking the computer, and responding to security prompts.
By following these tips and leveraging the customization options available, users and administrators can make SAS an even more effective tool in their security arsenal.
6. References
- “Windows NT 4.0 Security, Audit, and Control” by James D. Murray
- “Responsibilities of the GINA” by Microsoft Learn
- “Interactive Authentication“, by Microsoft Learn