Category: Letter S
-

Introduction to the Sandbox: Your Digital Playground
Dive into the digital playground of sandboxes where safety and innovation play nice together. Explore how sandboxes create secure environments for testing and development, their various types, and their pivotal role in enhancing security across technologies. Discover the future trends of sandboxing in this comprehensive guide.
-

Software 2.0: The Evolution of Coding as We Know It
In this article, we’ll dive deep into the intricacies of Software 2.0, exploring how it’s reshaping the landscape of technology by automating the decision-making processes in software applications.
-

Submarine Communication Cables: Secrets of the Ocean Depths
Join us as we dive deeper into the dynamic saga of submarine communication cables, exploring their pivotal role in our interconnected era and the continuous efforts to safeguard this hidden infrastructure.
-

SPF Records: Ensuring Your Emails Land Where They Should
Discover how to craft, validate, and implement SPF records to protect your domain, prevent email spoofing, and ensure your messages reach their intended destinations. With practical insights and expert advice, this article is an indispensable resource for anyone looking to bolster their email security and deliverability.
-
Exploring the Session Layer in the OSI Model
Delve into the Session Layer of the OSI Model: understand its functions, protocols, and impact on network communication in this detailed exploration.
-
SPAM: Unmasking the Digital Nuisance Clogging Our Inboxes
Discover the intricacies of SPAM—its history, types, impact on cybersecurity, and ways to combat it. Your comprehensive guide to this digital menace.
-
What Are Symbolic Links? And How Do They Relate to Relative Paths?
Discover what Symbolic Links are and how they intertwine with the concept of Relative Paths. Master file navigation and system organization efficiently.
-
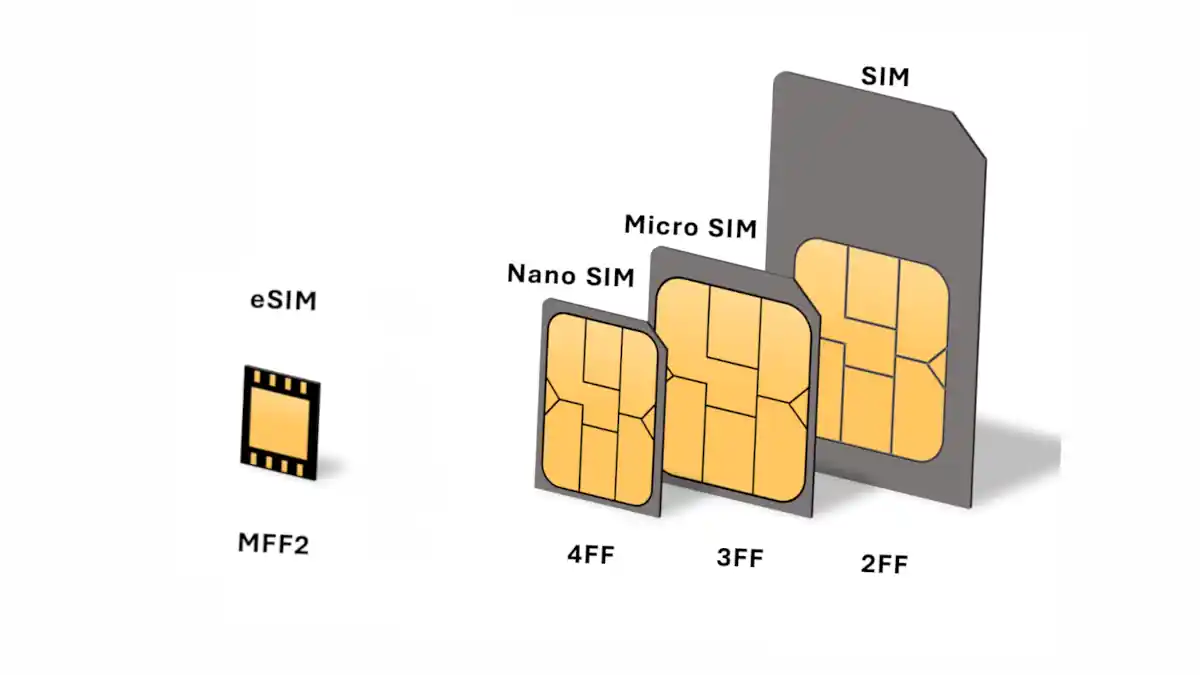
Subscriber Identity Module (SIM): A Comprehensive Guide
Discover the inner workings of SIM cards—the cornerstone of mobile connectivity. From technology to security, this guide covers it all.
-

Demystifying SQL Injection Types: Threats and Safeguards
Explore SQL injection types, the stealthy exploits threatening databases. Learn how to safeguard your systems against these cunning attacks.
-

Security Devices in Computer Networks Unveiled
Dive into the essentials of security devices safeguarding computer networks. Explore their roles, types, and why they’re pivotal for digital safety.
-

Computer System Analyst: Demystifying the Role
Dive deep into the dynamic role of a computer system analyst. Explore tasks, skills, and the bridge between tech & business.
-
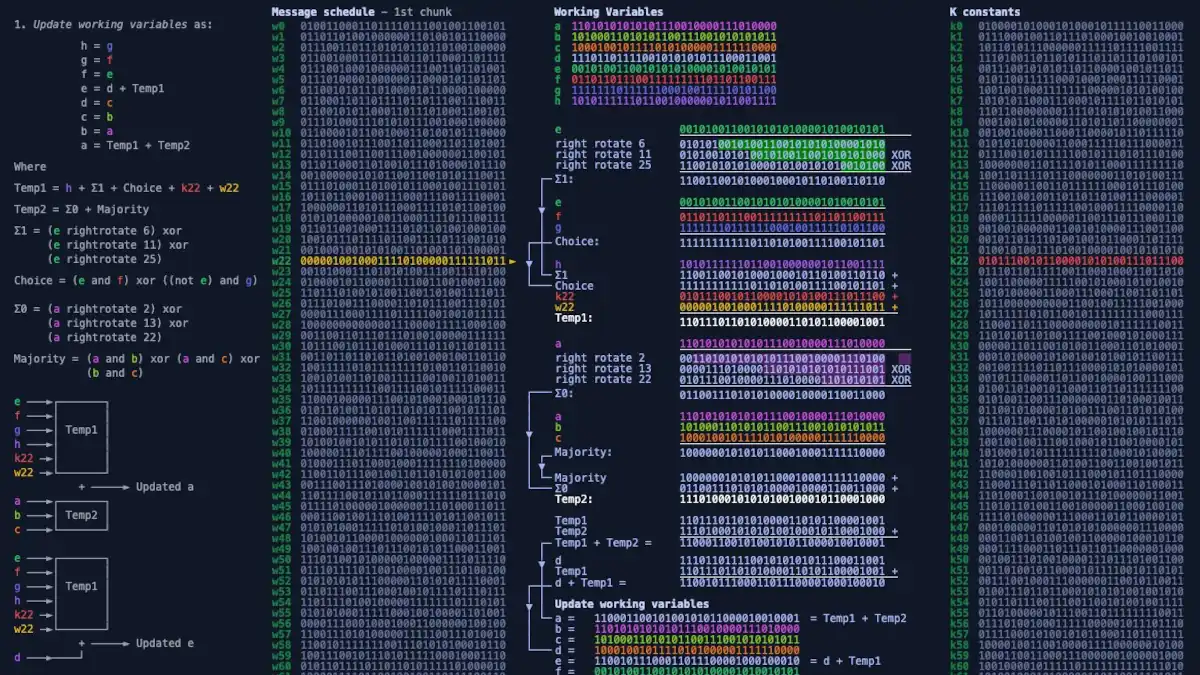
SHA-256 Unmasked: Deciphering Cryptographic Hash Functions
Unveil the world of cryptographic hash functions as we break down SHA-256. Understand its vital role in ensuring data integrity and security in the digital realm.