In the world of Windows, certain terminologies and acronyms carry with them a rich history of evolution and significance. NTDS, or the Windows NT Directory Services, is one such term that stands as a testament to Microsoft’s journey in creating robust directory services. Yet, in modern contexts, NTDS is also commonly associated with the NTDS.DIT file, a cornerstone of Active Directory databases. This article seeks to bridge the understanding between these two related, yet distinct, entities, providing a comprehensive look into their roles, functionalities, and importance in the realm of Windows operating systems.
Jump to:
- Historical Overview of Windows NT Directory Services (NTDS)
- How Windows NT Directory Services Worked
- Diving Deep into NTDS.DIT
- The Evolution: From NTDS to NTDS.DIT
- Security Implications and Best Practices
- Future Outlook and Predictions
- Conclusion
- References
1. Historical Overview of Windows NT Directory Services (NTDS)
Birth of Windows NT and the Need for NTDS
Windows NT, debuting in the early 1990s, marked Microsoft’s venture into a new breed of operating systems, targeting both workstations and servers. Designed to be a robust, secure, and scalable platform, there was an intrinsic need for an organized method to manage users, resources, and permissions. Enter NTDS – the Windows NT Directory Services. Designed as an integrated set of services, NTDS was tailored to centrally manage and store information about network resources across a domain.
Core Functionality and Importance of NTDS
At its core, NTDS functioned as a directory for storing and retrieving information in a networked environment. This directory wasn’t just a mere list. It was a hierarchical, structured, and extensible database. NTDS offered the ability to manage a variety of objects, including users, groups, computers, and printers. With NTDS, administrators could enforce policies, implement security, and ensure that resources were efficiently allocated across the network. In essence, NTDS was the backbone, allowing for centralized management in a Windows NT domain.
The Transition: From NTDS to Active Directory
The late 1990s heralded a shift. As the tech landscape evolved, so did the expectations of network management tools. Microsoft recognized this and, with the release of Windows 2000, introduced Active Directory (AD) as a successor to NTDS. Active Directory inherited the foundational principles of NTDS but brought along with it a slew of enhanced capabilities. The hierarchical nature of NTDS was expanded upon, and AD incorporated a multi-master replication model, improved querying capabilities, and a broader scope of object management. The transition from NTDS to Active Directory wasn’t just about renaming but represented a fundamental shift in how directory services were envisioned and executed.
2. How Windows NT Directory Services Worked
This article was completely renovated and expanded in November 2023. It now includes not only an explanation of what NTDS was at its origin but also explores its evolution and describes its current form, NTDS.DIT. The original, older article has been incorporated into this new article in the form of a chapter, this chapter that you are now reading.
Windows NT Directory Services, or NTDS, was the directory services used by Microsoft Windows NT to locate, manage, and organize network resources. Windows NT Directory Services (NTDS) used domains, trusts, and directory synchronization to provide users of enterprise-level Windows NT networks with the following advanced capabilities:
- Single-logon capability: Users can log on anywhere in the enterprise using only one account.
- Centralized administration: Administrators can manage the entire network from a single location.
- Universal resource access: Users can access resources anywhere in the enterprise if they have the appropriate permissions.
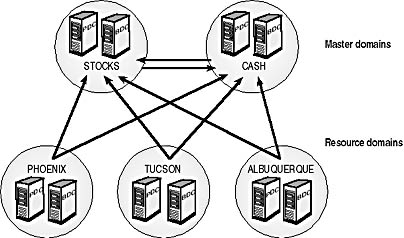
To build effective enterprise-level directory services using Windows NT domains, you should consider the following factors:
- The number of domains needed (the domain model used)
- The number of domain controllers needed to support the number of users
- The placement of backup domain controllers (BDCs) to assure efficient directory synchronization of directory services
- The placement of BDCs to assure effective logon and resource authentication over slow WAN links
2. Diving Deep into NTDS.DIT
Introduction to NTDS.DIT: More than Just a File
The term “NTDS.DIT” might sound like a cryptic file extension at first glance, but its role in the context of Windows systems is profound. Standing for Directory Information Tree, the .DIT file is the physical storage representation of the Active Directory database. Nestled within the heart of a Windows server, it carries the weight of every object and attribute within an Active Directory domain.
Role of NTDS.DIT in Active Directory
Active Directory operates with the primary mandate of managing and authenticating network entities. NTDS.DIT is where all this data resides. From a user’s login credentials to the security permissions of a file, it’s all encapsulated within this file. Every time a user logs in, a group policy is applied, or a new object is added to the domain, NTDS.DIT is accessed. In simpler terms, without NTDS.DIT, Active Directory, as we know it, would be non-functional.
Structure and Components: A Technical Look
Diving into the anatomy of NTDS.DIT, one discovers that it’s meticulously structured. The file comprises two main tables: the data table and the link table. The data table contains the bulk of the information, holding actual AD objects like users, OUs, and groups. The link table, on the other hand, deals with the relationships or links between these objects. Additionally, to ensure data integrity and performance, NTDS.DIT employs a transaction logging mechanism. Every change made is first written to a log file and then committed to the main database. This not only ensures data consistency but also aids in recovery, should there be any system failures.
The understanding of NTDS and NTDS.DIT is vital for anyone looking to grasp the evolution and intricacies of Windows’ directory services. While they originate from different eras of Windows’ storied history, both have left an indelible mark on how network resources are managed and accessed.
3. The Evolution: From NTDS to NTDS.DIT
Timeline of Development: Key Milestones
The journey from NTDS to NTDS.DIT is one that spans several significant developments in the world of Windows server technology. Starting with the introduction of Windows NT in the early 1990s, NTDS became the bedrock of network management, offering a centralized directory service. However, as the 21st century dawned, Windows 2000 brought with it the rise of Active Directory, and consequently, the NTDS.DIT file. This new file format represented the physical database of the entire Active Directory. The evolution continued with successive versions of Windows Server, each enhancing the functionality, performance, and security of NTDS.DIT.
Changes in Functionality and Performance
The shift from NTDS to NTDS.DIT was much more than a mere nomenclature change. Functionality expanded considerably. While NTDS was primarily a directory service, NTDS.DIT encapsulated an entire database of Active Directory objects. Its structure became more intricate, capable of storing and managing a wider range of objects, relationships, and attributes. Performance-wise, NTDS.DIT, backed by Active Directory’s capabilities, offered faster query responses, efficient data replication across domain controllers, and a more resilient system recovery mechanism.
Implications for System Administrators and IT Professionals
For those in the trenches of network management, the evolution brought a mix of challenges and opportunities. With NTDS.DIT and its Active Directory backing, administrators now had a more powerful tool at their disposal. They could implement more granular policies, achieve better scalability, and ensure efficient resource management across larger networks. However, the added complexity demanded a deeper understanding of the system, meticulous planning for deployments, and continuous monitoring to ensure optimal performance.
4. Security Implications and Best Practices
NTDS Security Concerns in Historical Context
Historically, with the rise of NTDS, security was a concern but often limited in scope. The primary focus was on user authentication, permissions, and rudimentary audit trails. As cyber threats were not as advanced or prevalent, the security mechanisms were, by today’s standards, basic. But as technology advanced and threats became more sophisticated, the inherent vulnerabilities of NTDS became more apparent, prompting a need for a more robust system.
Modern Security Measures for NTDS.DIT
With NTDS.DIT housing the entire Active Directory database, its security implications are massive. Modern measures have evolved to address these. There’s now an emphasis on encryption, both for data at rest and in transit. Advanced logging mechanisms record even the minutest of changes, and intrusion detection systems monitor unauthorized access attempts. Furthermore, multi-factor authentication, rigorous password policies, and regular security patch updates have become the norm to protect NTDS.DIT.
Best Practices for Maintenance and Backup
Given the critical nature of NTDS.DIT, its maintenance is paramount. Regular backups, ideally with a mix of full and incremental, should be scheduled. System administrators are advised to periodically test these backups for integrity. Monitoring tools should be deployed to track performance metrics and send alerts for any anomalies. Regular audits, both for performance and security, will ensure that the system remains optimized and secure. Lastly, any changes to NTDS.DIT, be it adding new objects or modifying policies, should be meticulously documented, ensuring a trail of actions for future reference.
Embracing best practices ensures that while leveraging the full potential of NTDS.DIT, risks are mitigated, and the system remains agile, efficient, and secure.
5. Future Outlook and Predictions
Lessons from the Past: NTDS’s Legacy
The story of NTDS, from its inception to the evolution into NTDS.DIT, provides critical lessons about technology and its trajectory. One clear takeaway is the perpetual need for systems to adapt and evolve. NTDS, in its time, revolutionized network management, but as user needs changed and technology advanced, it required an upgrade. This continuous need for adaptation is a lesson every tech enthusiast, developer, and system administrator should internalize. Additionally, the journey underscores the importance of security. As systems become more complex and integral, their vulnerabilities can have amplified consequences, emphasizing the need for robust security measures from the inception of any tech solution.
Predicting the Future: What’s Next for Active Directory and NTDS.DIT?
While predicting the exact trajectory of technology is always challenging, a few educated guesses can be made based on current trends. Active Directory, backed by NTDS.DIT, will likely see more integration with cloud-based solutions. As organizations increasingly adopt hybrid cloud models, ensuring seamless user management across on-premises and cloud infrastructures will become essential. Furthermore, with the rise of AI and machine learning, we can anticipate smarter directory services that can predict needs, automate routine tasks, and flag anomalies in real-time. Cybersecurity will continue to be at the forefront, with advanced encryption techniques and real-time threat intelligence becoming standard features.
Embracing Change While Honoring Legacy
It’s crucial to recognize that while change is inevitable, it doesn’t mean discarding the past. Instead, it’s about building upon it. As we look forward to the future of Active Directory and NTDS.DIT, it’s essential to respect the legacy of NTDS. By understanding its origins, challenges, and achievements, we can ensure that future iterations are not just technologically superior but also grounded in the rich history and learnings from the past.
6. Conclusion
The journey from Windows NT Directory Services to NTDS.DIT serves as a compelling narrative about the evolution of technology, the challenges of adaptation, and the imperatives of security. As we stand on the cusp of yet another technological revolution, it’s vital to look back at our digital roots, understand them, and use that understanding to forge a path forward. While the specifics of NTDS and NTDS.DIT might become obsolete, the lessons they offer will remain relevant, guiding future generations of tech enthusiasts and professionals.
7. References
- Solomon, D., & Russinovich, M. E. (2000). Inside Microsoft Windows 2000. Microsoft Press.
- Gary Nebbett (2002). Windows NT/2000 Native API Reference. SAMS Publishing.
- RFC 2307 – An Approach for Using LDAP as a Network Information Service.
- Stanek, W. R. (2008). Windows Server 2008 Inside Out. Microsoft Press.
- Microsoft Documentation. (n.d.). Active Directory Services Overview. Retrieved from https://docs.microsoft.com/.
- Leland Beck (1997). System Software: An Introduction to Systems Programming. Pearson.