The term “Attribute Marker” can carry multiple meanings depending on the context in which it’s used within computer science. Most commonly, it’s a feature in file systems like FAT and NTFS that governs file properties. However, attribute markers are also relevant in programming, database management, and network protocols. In this comprehensive guide, we’ll explore the various facets of attribute markers and understand how they function in different areas of computer science.
Table of Contents
- What are Attribute Markers?
- Attribute Markers in File Systems
- Read-Only
- Hidden
- System
- Archived
- Attribute Markers in Programming
- Attribute Markers in Database Management
- Attribute Markers in Network Protocols
- FAQs
- Conclusion
- References
1. What are Attribute Markers?
Attribute markers are a kind of metadata that describes specific characteristics or permissions of a file, object, or data entry. In essence, they’re tags that tell the system how to treat a particular piece of data. They can be as straightforward as indicating if a file should be read-only or as complex as specifying encryption algorithms for a database entry.
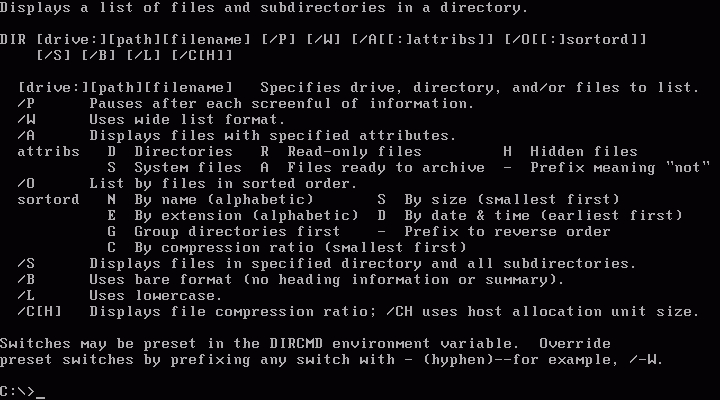
Attribute Marker is a type of marker that can be set or cleared for files stored on the file allocation table (FAT) or NTFS file system.
2. Attribute Markers in File Systems
Read-Only
The read-only attribute restricts modifications to a file. When set, the file becomes immutable; you can read it, but you cannot alter its content without changing its attribute first.
Hidden
Files with the hidden attribute will not display when the parent directory is listed, usually via command-line operations. This feature helps in preventing accidental deletion or modification of important files.
System
A system attribute marks a file as a critical operating system component. Tampering with such files could lead to system instability, and therefore, they are usually hidden and locked.
Archived
The archived attribute is a marker that tells backup software that the file needs to be archived. Once it’s backed up, the attribute is cleared until the file is modified again.
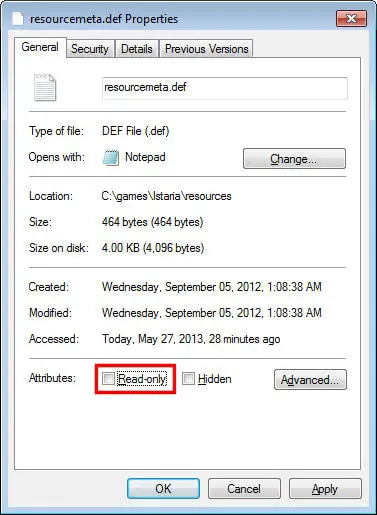
Attribute Marker in FAT and NTFS
The above attributes can be set or cleared for files on both FAT and NTFS partitions. In addition, files on an NTFS volume can be marked as compressed. NTFS uses a number of other extended attributes internally. The term “attribute” can also refer generally to other file system information, such as time stamps, file size, link counts, and so on.
This chapter sets the stage for understanding attribute markers within the realm of file systems. But their utility isn’t confined just to managing files. Let’s look at how attribute markers find applications in programming next.
3. Attribute Markers in Programming
In programming, attribute markers function as metadata for classes, methods, properties, and more. These attributes can alter the behavior of code or give the compiler special instructions. For instance, in C#, you might encounter attribute markers like [Obsolete], which indicate that a method is deprecated, or [DllImport] to specify a dynamic link library (DLL) containing an external method.
Code Annotations
One common use of attribute markers in programming is code annotation. These annotations can specify behavior like thread safety, nullability, or immutability, guiding both the developer and the compiler.
Reflection
Attribute markers are often used in tandem with reflection, a mechanism to inspect metadata at runtime. This allows programmers to modify behavior or setup configurations dynamically, based on the attribute markers.
4. Attribute Markers in Database Management
In database management, attribute markers can define a multitude of characteristics, from field types to access permissions. For instance, in a SQL database, attribute markers can specify whether a field is a primary key, its data type, or if it should auto-increment.
Indexing and Optimization
Attribute markers can also have performance implications. Fields marked for indexing can substantially speed up query performance at the expense of additional storage.
Constraints and Validation
Adding attribute markers can impose constraints like “not null,” “unique,” or even complex validations, ensuring data integrity and consistency.
5. Attribute Markers in Network Protocols
In the context of networking, attribute markers can specify how packets should be handled, routed, or processed. These markers can be found in the header of the data packet and can include information like Quality of Service (QoS) levels, encryption algorithms, or even routing paths.
Security Protocols
Attribute markers can indicate the security requirements for a packet, specifying whether it should be encrypted or if it requires certain authentication procedures before being processed.
Traffic Shaping
Network routers can use attribute markers to perform traffic shaping, prioritizing certain types of packets over others to ensure optimal network utilization.
6. Frequently Asked Questions
Q: Can attribute markers be changed?
A: Yes, depending on the context. For example, file attributes can be changed using system utilities or commands, while attribute markers in code generally require recompilation for changes to take effect.
Q: Are attribute markers the same in all programming languages?
A: No, the syntax and capabilities can vary. For example, attributes in C# are not the same as decorators in Python, although they serve similar purposes.
Q: Do all databases use attribute markers?
A: Most relational databases do, but NoSQL databases like MongoDB may not have traditional attribute markers, relying instead on schema-less architectures.
7. Conclusion
Finally, attribute markers are a critical part of modern computing, enabling nuanced control and behavior across a variety of fields. From programming languages to databases to networking protocols, attribute markers offer a way to encode additional information, thereby extending capabilities and ensuring correct behavior. In sum, understanding how and when to use these markers can make your projects more robust, efficient, and secure.
8. References
- Tanenbaum, Andrew S., and Maarten Van Steen. “Distributed Systems.” Pearson, 2007.
- “C# Programming Guide: Attributes.” Microsoft Docs. Link
- Kurose, James F., and Keith W. Ross. “Computer Networking: A Top-Down Approach.” Pearson, 2020.
- “SQL Constraints.” W3Schools. Link
- “RFC 2474 – Definition of the Differentiated Services Field (DS Field) in the IPv4 and IPv6 Headers.” IETF. Link
