Category: Letter A
-

AAA Protocol: Your Gateway to Secure Network Access
Dive into the world of AAA Protocol, where network security meets ease of access. Discover how Authentication, Authorization, and Accounting work to keep your network secure.
-

Understanding Dynamic Adaptive Streaming over HTTP (DASH)
Explore the essentials of Dynamic Adaptive Streaming over HTTP (DASH), the technology revolutionizing media delivery online.
-
Assembly Language: Low-Level Programming
Assembly language is a low-level programming language that provides a unique perspective on computer operations, sitting just above machine code in complexity.
-

Ashton-Tate: The dBase Creators
Ashton-Tate was a software company that was best known for developing the popular dBASE database application. It was founded in 1980 by Hal Lashlee and George Tate.
-
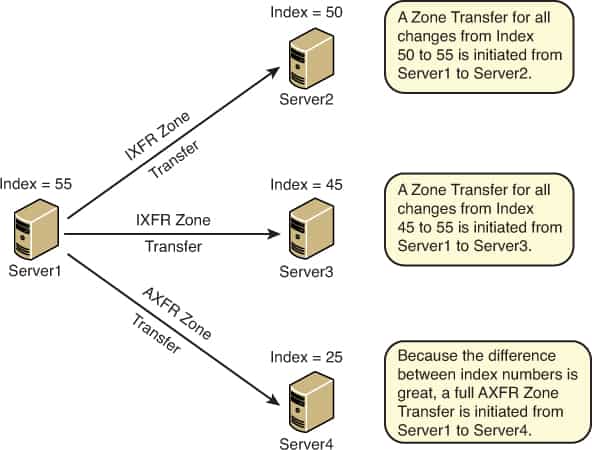
AXFR Request
AXFR Request is a type of Domain Name System (DNS) request in which a secondary DNS server requests the update of information from a master DNS server.
-

Asymmetric Encryption
Asymmetric encryption requires the use of two keys: a private key that is known only by its owner and a public key that is readily available to those who need to use it.
-
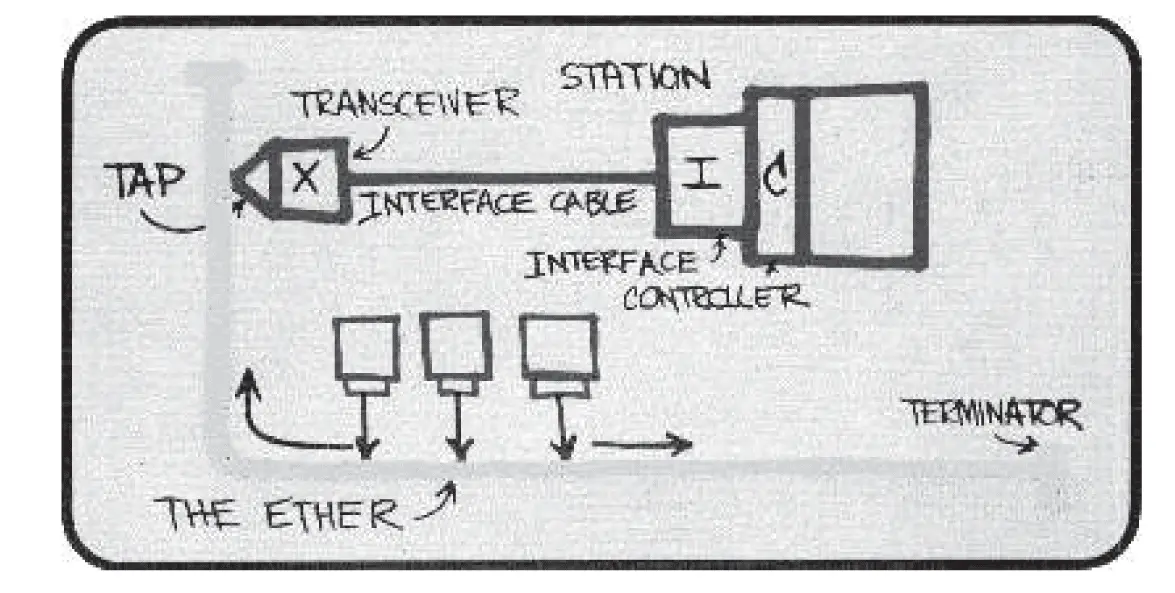
Aloha Network
ALOHA NETWORK, was a networking system developed at the University of Hawaii in the late 1960s. Norman Abramson and his colleagues developed a radio network for communication among the Hawaiian Islands. This system was an early experiment in the development of mechanisms for sharing a common communications channel – in this case, a common radio channel.…
-

Understanding the autochk.exe file
Uncover the essentials of Autochk in Windows: Learn how this key utility maintains system integrity, how to use it, and manage its settings for optimal performance.
-

AWG (American Wire Gauge)
AWG is an acronym for American Wire Gauge, a specification for the diameter of conducting wires. The higher the AWG number, the thinner the wire. Category 5 cabling is usually AWG 24 wire (0.020 inch or 0.511 millimeter in diameter), while thicknet generally uses AWG 12 wire (0.080 inch or 2.050 millimeters in diameter). The…
-
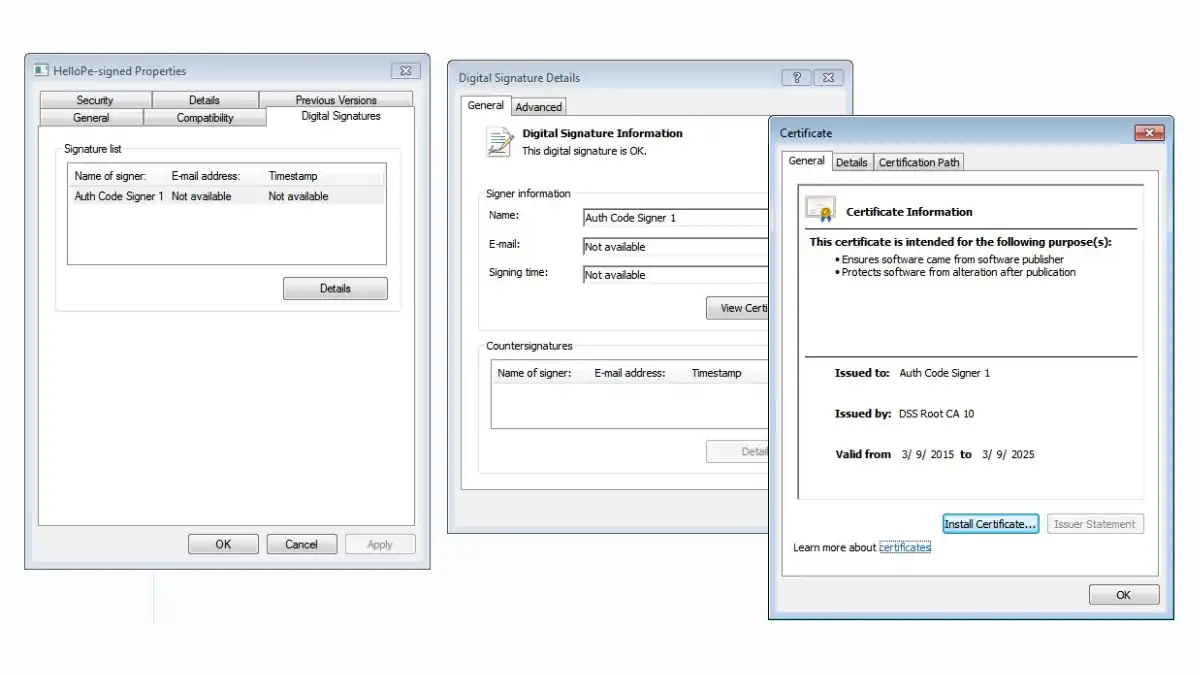
Authenticode
Unlock the secrets of Microsoft’s Authenticode: Verify publishers and safeguard software integrity. Your go-to guide for robust cybersecurity.
-

AUI Connector: Evolution, Legacy, and Modern Relevance
AUI is an acronym for Attachment Unit Interface connector, a standard 15-pin connector device for thicknet or 10Base5 cabling. The AUI connector on the free end of the drop cable attaches to the DB15 connector on the network interface card (NIC). The NIC has an AUI port connector for connecting the drop cable.
