Brute-force attacks are among the oldest yet most effective types of cyber threats lurking in the digital landscape. This article aims to enlighten you on what a brute-force attack is, how it works, and most importantly, how to shield yourself from becoming a victim. We will dig deep into technical explanations while keeping it digestible for anyone who wants to amp up their cybersecurity know-how.
In this article:
- What is a Brute-Force Attack?
- History of Brute-Force Attacks
- Brute-Force Attacks Examples
- The Technical Anatomy of a Brute-Force Attack
- How to Protect Against This Threat
- Monitoring and Detection
- Brute-Force Attacks and Legal Ramifications
- Conclusion and Final Thoughts
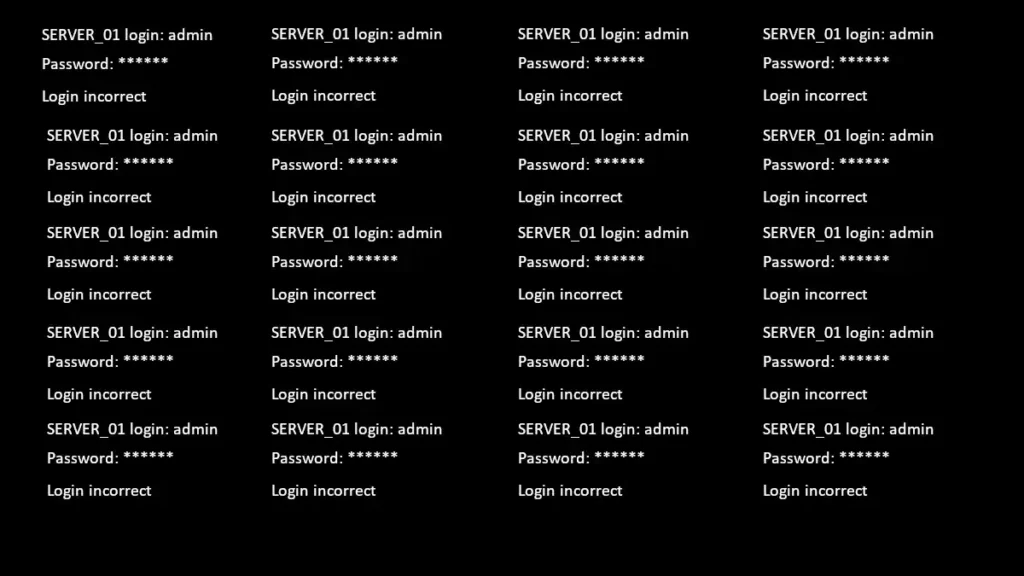
1. What is a Brute-Force Attack?
Definition and Mechanics
A brute-force attack is essentially a trial-and-error method employed by attackers to gain unauthorized access to a system. In layman’s terms, it’s like trying every possible key in a lock until you find the one that works. Technically, the attacker attempts to ‘crack’ the security measures—usually passwords—by systematically checking all possible combinations until the correct one is found.
The concept is simple but don’t underestimate its efficacy. With the computational power available today, a brute-force attack can try thousands—or even millions—of combinations in just seconds. So, if your password is “1234,” you’re practically rolling out the welcome mat for these invaders.
Now, let’s move onto the gears that drive a brute-force attack. They usually involve automated software or scripts that generate and try different character sequences. Additionally, these attacks may exploit vulnerabilities in a system’s security protocols, making it easier to perform the attack without detection.
Types of Brute-Force Attacks
Brute-force attacks are not one-size-fits-all; they come in different flavors. Knowing the different types can help you better understand your vulnerabilities. Here they are:
- Simple Brute-Force Attack: The most straightforward type where an attacker tries all possible combinations. No finesse, just raw computational power.
- Dictionary Attack: Instead of trying all possible combinations, the attacker uses a precompiled list of likely passwords. This list is known as a ‘dictionary,’ hence the name.
- Hybrid Brute-Force Attack: A combination of the dictionary and simple brute-force methods. The attacker starts with a dictionary attack and then moves on to a more comprehensive brute-force attack if unsuccessful.
- Rainbow Table Attack: A more sophisticated approach where the attacker uses precomputed tables to find password hashes, significantly speeding up the cracking process.
- Credential Stuffing: While not a brute-force attack in the traditional sense, it uses previously breached username-password combinations on multiple sites, banking on the fact that people often reuse passwords.
- Reverse Brute-Force Attack: Here, the attacker knows the password but tries to find out the username. This is less common but still a viable method.
- Distributed Brute-Force Attack: This involves using multiple machines to attack a single target, thus significantly increasing the rate of attempts and decreasing the time to crack the password.
In summary, a brute-force attack can be as simple as a sledgehammer or as nuanced as a lockpick set. Regardless of the method, the outcome remains the same—unauthorized access that can wreak havoc on personal and organizational levels. Now that you’re up to speed on what a brute-force attack is and the types that exist, we’ll delve into real-world examples and protective measures in subsequent chapters. Stay tuned!
2. History of Brute-Force Attacks
Origin and Evolution
The concept of brute-force attacks dates back to the dawn of computer systems and networked environments. In the early days, these attacks were rudimentary and usually conducted manually, often requiring physical access to a system. In essence, the idea of systematically checking combinations to bypass security isn’t new; it’s as old as the concept of locks and keys.
However, the landscape shifted dramatically with the advent of the internet and advancements in computing power. What used to take years—or even decades—to crack could now be solved in a matter of days, hours, or even seconds. Algorithms got smarter, tools became more sophisticated, and the power of parallel processing enabled attackers to perform large-scale attacks more efficiently.
These attacks have also evolved in response to security measures. For instance, as hashing algorithms improved, rainbow table attacks came into being. Similarly, as more people began using the same passwords across platforms, credential stuffing attacks saw a rise. The point is, as long as there are locks, there will be locksmiths—ethical or otherwise.
Famous Instances
While brute-force attacks are often not publicized to avoid giving hackers undue attention, some instances have gained notoriety due to their scale or the importance of the target. Let’s examine a few:
- The TJX Companies Incident (2007): Though not purely a brute-force attack, the largest-ever theft of customer data at the time involved weak WEP encryption that was brute-forced to gain access to 45.7 million credit and debit card numbers.
- RockYou (2009): This attack led to the exposure of 32 million passwords, stored in plain text. A brute-force attack subsequently helped decode many of these, revealing an alarming frequency of easily guessable passwords.
- The iCloud Breach (2014): Known colloquially as “The Fappening,” hackers used a brute-force script to guess iCloud passwords, leading to the leak of private celebrity photos.
- RSA Security Breach (2011): In a complex attack involving social engineering and spear-phishing, a brute-force element was used to crack password-protected files, eventually leading to the compromise of secure tokens used by millions.
- Bitcoin Wallets: As cryptocurrencies gained in value, so did attempts to brute-force private keys for Bitcoin wallets. Some have been successful, resulting in the theft of substantial sums.
- Mirai Botnet: Used in distributed denial-of-service (DDoS) attacks, the Mirai botnet also employs brute-force techniques to infect poorly secured IoT devices.

To recap, brute-force attacks have a long history that parallels the evolution of cybersecurity measures. They’ve impacted millions and led to significant financial losses and erosion of trust. But understanding their history and mechanics is the first step in guarding against them, a subject we will tackle in the following chapters. Stay vigilant and keep reading!
3. Brute-Force Attacks Examples
Attacks on Websites
Web servers are frequent targets of brute-force attacks, primarily due to the vast amount of data they hold. For instance, content management systems like WordPress can be vulnerable if not properly secured. Attackers often use brute-force tactics to guess the administrator password, thereby gaining access to the entire website. Upon successful entry, they can manipulate content, steal sensitive data, or inject malicious code. The infamous “admin/admin” default login credentials are a gateway for such exploits. Thus, website owners must implement stringent password policies, CAPTCHA, and rate limiting to fend off these intruders.
Attacks on Social Media
In the realm of social media, brute-force attacks aim to gain unauthorized access to personal accounts. Once inside, attackers can misuse the account for various purposes—ranging from identity theft to the dissemination of spam and malicious links. The Twitter hack of 2020 serves as a stark example, where high-profile accounts were hijacked to promote a Bitcoin scam. Automated bots can carry out these attacks at an alarming speed, making use of precompiled lists of common passwords. Two-factor authentication (2FA) has been effective in adding an extra layer of security against these kinds of breaches.
Attacks on Financial Institutions
Perhaps the most damaging in terms of immediate financial loss are brute-force attacks on banks and other financial institutions. Such attacks are meticulously planned and often involve both brute-forcing login credentials and defeating security questions. Automated software can run permutations of account numbers, PINs, and passwords until the correct combination is found. The 2016 Tesco Bank incident in the UK is an illustrative case. Hackers used a brute-force attack to guess account numbers, subsequently siphoning off money from thousands of accounts. Financial institutions are thus forced to continually update their security protocols to protect against these evolving threats.
In summary, no sector is immune to the risks posed by brute-force attacks. From your personal social media account to a multinational bank, the breadth of targets is as wide as it is concerning. However, by understanding the types of attacks and their implications, one can better prepare and implement security measures, a topic we will delve into in the following chapters. So, keep reading to fortify your cyber defenses.
4. The Technical Anatomy of a Brute-Force Attack
Algorithms Involved
Brute-force attacks aren’t sophisticated in terms of the algorithms they use, but the devil is in the persistence and computational power behind them. The most basic form of a brute-force algorithm sequentially checks all possible combinations until the correct one is found. However, slight variations can optimize this process. For example, a dictionary attack uses a pre-defined list of likely passwords, while a “mask” attack applies patterns or masks to predict possible password combinations. Additionally, time-memory trade-off algorithms like rainbow tables may also be used to expedite the password-cracking process.
Algorithms like “Bcrypt” and “Argon2” are commonly used on the defensive side to slow down brute-force attacks. These are called “adaptive hashing algorithms” and they are designed to use more computational power, making each password guess slower and more resource-intensive.
Tools Commonly Used
Several tools are available that automate the brute-force process, each with its own set of capabilities and methods. Here are some commonly used ones:
- John the Ripper: Initially developed for Unix systems, this open-source software is versatile enough to work on multiple platforms and can crack a variety of encryption algorithms.
- Hashcat: Touted as the world’s fastest password cracker, Hashcat supports five unique modes of attack, allowing it to tackle various types of encryption algorithms.
- Hydra: This is a parallelized login cracker that supports numerous protocols to attack, making it useful for various forms of brute-force attacks.
- Medusa: Similar to Hydra but considered lighter and faster, Medusa is famed for its speed in executing dictionary-based attacks.
- Brutus: One of the earliest tools for Windows systems, Brutus is great for online password cracking but hasn’t been updated in several years, rendering it less effective against modern security measures.
Whether it’s a simple tool used by a lone hacker or a more complex system deployed by an organized crime syndicate, the objective remains the same: to break through security barriers by exhausting all possible combinations. This highlights the importance of employing strong, unique passwords and leveraging additional security measures like multi-factor authentication.
Understanding the technical intricacies of how brute-force attacks operate enables us to appreciate the countermeasures that can be taken. We’ll explore these protective mechanisms in the coming chapter, so stay tuned for actionable insights.
5. How to Protect Against This Threat
Password Policies
A strong password policy is your first line of defense against brute-force attacks. Use a combination of upper-case letters, lower-case letters, numbers, and special characters to create complex passwords. Implement minimum length requirements, and regularly update passwords. The more complex and unpredictable a password is, the longer it will take for a brute-force attack to crack it.
Multi-Factor Authentication (MFA)
MFA adds an additional layer of security by requiring two or more forms of verification before granting access. Typically, this involves something you know (a password) and something you have (a mobile device to receive a code, for example). By enabling MFA, you significantly reduce the likelihood of unauthorized access, even if a password is compromised.
Rate Limiting and Lockout Policies
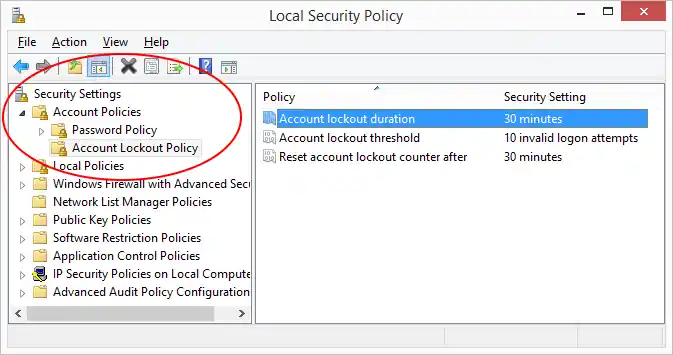
Rate limiting restricts the number of login attempts from a single IP address during a specified time period. Lockout policies take this a step further by temporarily or permanently disabling an account after a certain number of failed login attempts. Both of these measures can effectively thwart brute-force attacks by making them time-consuming and resource-intensive.
6. Monitoring and Detection
Logs and Alerts
Monitoring system logs can provide early detection of a brute-force attack. Configure logs to alert administrators when multiple failed login attempts occur within a short time frame from the same IP address. Being proactive in your monitoring can allow you to take immediate action, such as blocking the suspicious IP address.
Intrusion Detection Systems (IDS)
An Intrusion Detection System serves as a digital “watchtower,” continually monitoring network traffic for suspicious activities or known attack patterns. An IDS can identify multiple failed login attempts and either alert administrators or take automated actions like blocking the offending IP.
In conclusion, while brute-force attacks are relatively simple in concept, they can be highly effective if proper security measures are not in place. Strengthening your passwords, enabling MFA, implementing rate limiting and lockout policies, and vigilantly monitoring logs and alerts are crucial steps in mitigating the risks associated with brute-force attacks. By integrating these strategies, you not only protect individual accounts but also contribute to the overall security of your network ecosystem.
7. Brute-Force Attacks and Legal Ramifications
Laws and Regulations
Brute-force attacks are illegal under various cybercrime laws, such as the Computer Fraud and Abuse Act in the United States. These laws make unauthorized access to computer systems a criminal offense with severe penalties, which can include fines and imprisonment. Laws vary by jurisdiction, but the common thread is that unauthorized intrusion is a prosecutable offense.
Cases and Penalties
Several high-profile cases serve as cautionary tales. Offenders have received sentences ranging from heavy fines to years in prison, depending on the scale and impact of the attack. It’s important to note that laws are becoming increasingly stringent, and penalties more severe, as cybercrime evolves.
8. Conclusion and Final Thoughts
Summary of Key Takeaways
Brute-force attacks are one of the oldest yet most effective types of cyberattacks. They are simplistic in nature but can have devastating effects if successful. While there’s no one-size-fits-all solution to security, a multi-layered approach involving strong passwords, multi-factor authentication, and vigilant monitoring is the best strategy to thwart these types of attacks.
Stay Alert, Stay Protected
Vigilance is your strongest ally in the fight against brute-force attacks. Continually update your security protocols and educate your network users about the risks involved. Keep abreast of the latest security developments and invest in systems that help you monitor and defend against these persistent threats. In the evolving landscape of cyber threats, staying informed is staying protected.
By taking a proactive stance, you not only safeguard your personal information but also contribute to the broader fight against cybercrime. Remember, security is not a product but a process; it requires ongoing effort and awareness. Make it a priority, and you’ll build a more resilient defense against brute-force attacks and other cyber threats.