In the intricate world of Windows Operating System (OS), built-in user accounts play a pivotal role right from the system’s installation. These accounts, automatically created during the installation process, are fundamental for both system management and security. They form the backbone of Windows OS, providing essential functionalities and access controls required for efficient system operation. This article delves into the nature of built-in user accounts in Windows, examining their types, management practices, and the critical role they play in maintaining the security and integrity of the system.
In this article:
- What is a Built-in User Account?
- Types of Built-in Accounts in Windows
- Managing Built-in Accounts: Best Practices
- Security Implications of Built-in Accounts
- Customization and Limitations
- Conclusion
- References
1. What is a Built-in User Account?
A built-in user account in Windows refers to a user account that is automatically created during the installation of the operating system. These accounts are an integral part of the Windows OS, designed to facilitate essential system functions and administration. They come pre-configured with specific permissions and roles, which are critical for the maintenance and security of the system.
Distinction from Other User Accounts
Built-in accounts differ significantly from other user accounts:
- Pre-Configured vs. Custom: Unlike custom user accounts created by the system administrator or users, built-in accounts are pre-configured with specific roles and cannot be deleted.
- System-Level Access: Built-in accounts often have more extensive system-level access compared to regular user accounts, designed to perform system-critical tasks.
- Security Restrictions: These accounts usually have security restrictions and configurations that are inherent to the OS, aimed at minimizing security risks.
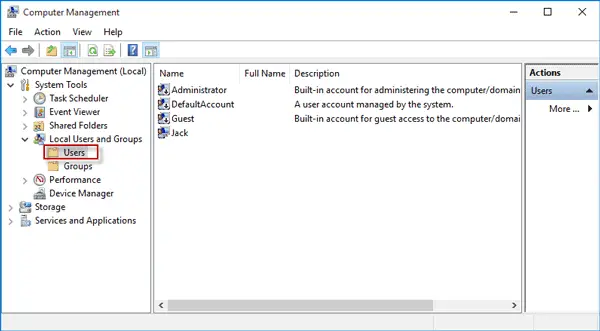
2. Types of Built-in Accounts in Windows
Different Built-in Accounts
Windows includes several key built-in accounts, each serving distinct purposes:
- Administrator Account:
- Function: This account has full control over the system and can make any changes, including system settings, software installation, and user management.
- Purpose: It is used for system administration and should be used sparingly due to its extensive access rights.
- Guest Account:
- Function: The Guest account allows temporary access to the system with limited privileges and no password protection.
- Purpose: It is designed for users who need temporary access to the computer without the ability to change system settings or access private files.
- System Account:
- Function: This account is used by the Windows OS to manage system services and processes. It has extensive privileges similar to the Administrator account but is not intended for general user access.
- Purpose: The System account is crucial for running system-critical services and tasks that require high-level access to the computer’s resources.
Each of these accounts plays a vital role in the functionality and security of the Windows OS. Understanding their functions and purposes is essential for effective system management and maintaining robust security protocols.
3. Managing Built-in Accounts: Best Practices
Guidelines for Effective Management
Effectively managing built-in accounts in Windows OS is crucial for both system stability and security. Here are some best practices:
- Secure the Administrator Account: Always use a strong password for the Administrator account. Consider renaming it to make it less susceptible to brute-force attacks.
- Limit Use of Administrator Account: Use the Administrator account only when necessary. For everyday tasks, use a standard user account to minimize potential risks.
- Disable the Guest Account: If not in use, disable the Guest account to prevent unauthorized access. If needed, ensure it has limited access rights.
- Regular Auditing: Conduct regular audits of built-in accounts to check for any unauthorized changes or usage.
Security Considerations and Recommendations
- Implement Principle of Least Privilege: Grant the minimum level of access required for users to perform their tasks. This reduces the risk of accidental or malicious system changes.
- Monitor Account Activity: Use security tools to monitor and log activities performed by built-in accounts, especially the Administrator account, for any unusual behavior.
- Apply Security Updates: Regularly update the system to ensure all security patches are applied, reducing vulnerabilities that could be exploited via built-in accounts.
4. Security Implications of Built-in Accounts
Role in System Security
Built-in accounts, especially the Administrator account, are integral to maintaining system security:
- Control and Management: These accounts allow for the control and management of security settings, user permissions, and system configurations, which are crucial for a secure operating system.
Risks and Mitigation
However, built-in accounts come with inherent risks:
- Administrator Account Misuse: The high-level access of the Administrator account can be a significant security risk if misused or compromised.
- Mitigation: Limit its usage and employ strong authentication methods. Regularly monitor the account for any unauthorized access.
- Guest Account Vulnerabilities: The Guest account can be an entry point for unauthorized users if not properly secured.
- Mitigation: Disable the Guest account if it’s not needed. If in use, restrict its access to minimal and monitor its activities.
- System Account Exploitation: While less directly accessible, the System account can be targeted in sophisticated attacks.
- Mitigation: Keep the system updated with the latest security patches and employ advanced security measures like intrusion detection systems.
In summary, while built-in accounts are vital for Windows OS operation and management, they require careful handling to ensure system security. Following best practices for account management and being aware of the potential risks are essential steps in securing a Windows-based system.
5. Customization and Limitations
Customization Options
While built-in accounts in Windows OS come with predefined settings and roles, there are certain customization options available:
- Password Policies: For the Administrator account, you can set strong password policies to enhance security.
- Renaming Accounts: It’s possible to rename the Administrator account for added security.
- Account Disablement: The Guest account can be disabled if not in use. This is a common practice in many security-conscious environments.
- Permission Adjustments: Permissions for these accounts can be adjusted, although this should be done cautiously and typically under expert guidance.
Limitations Inherent to Built-in Accounts
However, these accounts have inherent limitations:
- Fixed Roles: The fundamental roles of these accounts cannot be altered. For example, the System account will always have system-level access.
- Limited Deletion Options: Built-in accounts cannot be deleted from the system, ensuring the essential administrative functions they serve are always available.
Scenarios for Customization
Customization of built-in accounts is particularly beneficial in scenarios such as:
- Enhanced Security: In high-security environments, tweaking the settings of built-in accounts, especially the Administrator account, can significantly reduce security risks.
- Compliance Requirements: Certain industry regulations may require specific security configurations for built-in accounts.
6. Conclusion
Built-in user accounts in Windows OS are fundamental components that serve critical roles in system management and security. Understanding these accounts, their management best practices, and security implications is essential for any system administrator or IT professional.
While customization options do exist, they come with inherent limitations and should be approached with caution. Properly managing these accounts is key to maintaining a secure and efficient Windows environment.
7. References
- “Windows Operating System Security” by Microsoft.
- “Guide to Securing Microsoft Windows Accounts” by the National Institute of Standards and Technology (NIST).
- “Windows System Administration Handbook” by Nick Wells.