Category: Letter C
-

Coding Standards: A Symphony of Syntax
In this article, we’ll dissect these standards piece by piece, not only to understand what they are but also to learn how to effectively teach them to the next generation of web maestros – our junior web developers.
-

Unraveling CAPTCHA: The Gatekeeper of Modern Websites
CAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart) is designed to prevent automated software from performing actions that could potentially harm websites, ensuring that only humans can access certain functionalities.
-
Unveiling COBOL Programming Language
Explore COBOL, the programming language that shaped business computing, and understand its enduring legacy in technology today.
-
Decoding CISC: The Bedrock of Traditional Computing
CISC processors, built to execute complex tasks efficiently, may find new life in the realms of IoT and edge computing, where their robust instruction sets shine.
-

Common Criteria for Information Technology Security Evaluation (CC): Certifying Computer Security
In this article, we will delve into the significance of the Common Criteria, its global adoption, and the entities that rely on it for securing their digital assets. Additionally, we will touch upon its historical predecessor, the C2 security standard, to highlight the evolution of security evaluations in the IT realm.
-

Client-Server Model
Explore the intricacies of the Client-Server Model with our comprehensive guide. Learn its history, advantages, future trends, and how it drives modern computing.
-
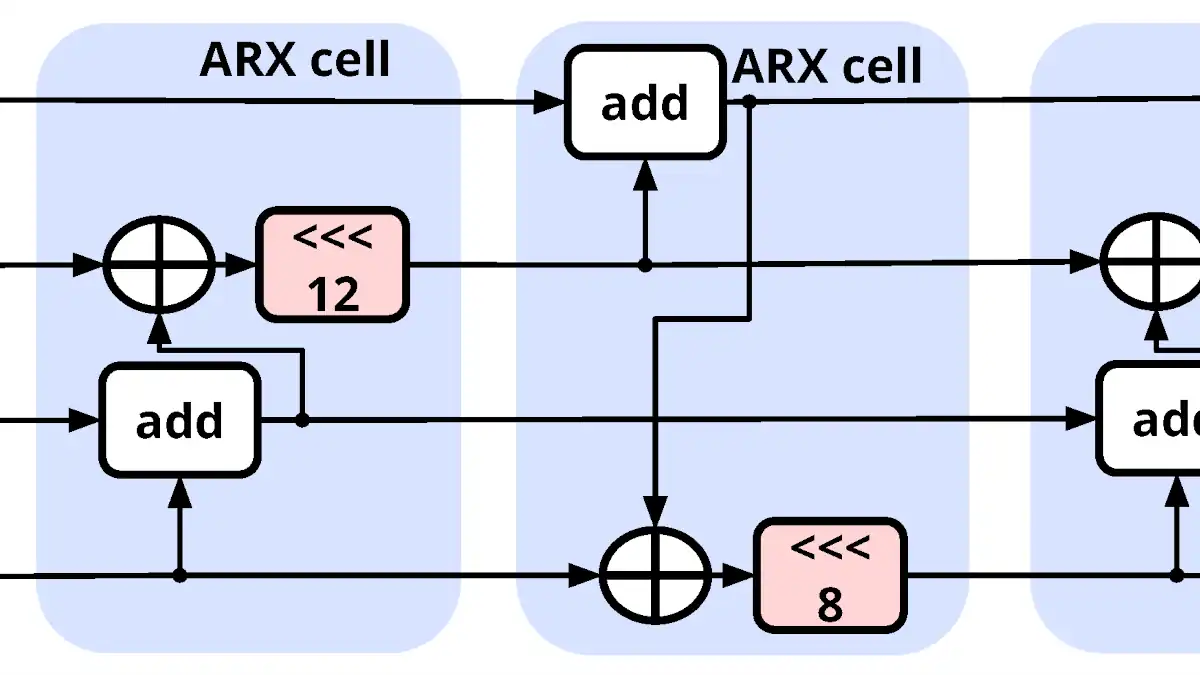
ChaCha20: The Dance of Cryptography
Dive deep into ChaCha20’s intricate dance of encryption. Explore the mathematics and design that make this cryptographic algorithm both potent and elegant.
-
Demystifying ClearType: Microsoft’s Answer to Crisp and Clear Text
Don’t miss this easy-to-understand guide on Microsoft’s ClearType technology for enhanced on-screen text readability.
-

Understanding Critical Data: Essential Aspects Exploration
Critical data refers to the essential information required for the successful operation of a business or organization.
-

Content Delivery Networks: Unleashing The Power of CDNs
In this article we will demystify what a CDN is, discuss its advantages and disadvantages, and delve into examples of some of the most widely used CDNs.
-

Understanding Critical Applications
Do you know what a critical application is? Some applications are more important than others, and these are known as critical applications.
-

Importance of Cyber Security in the Digital Era
Cyber Security in the Digital Era: It is crucial to understand what we are exposed to online and how to protect ourselves from potential attacks.