Category: Letter L
-

Unraveling LTE: Your Ticket to High-Speed Mobile Communication
In this article, we’ll embark on a journey through the world of LTE. We’ll decode how it works, why it’s a game-changer in mobile communications, and how it manages to deliver that crisp, clear video call quality even as you roam around.
-

Exploring Light Emitting Diodes (LEDs) in Modern Displays
Light Emitting Diodes (LEDs) are more than just indicators on your gadgets; they are at the heart of a lighting revolution that spans across numerous technologies.
-

Loopback Testing: Ensuring Network Reliability and Performance
Loopback testing stands as a cornerstone in maintaining and ensuring the reliability and performance of telecommunications and network infrastructures.
-

Understanding Large Language Models: Behind the Magic
Explore the intricate world of Large Language Models (LLMs), as we demystify how they’re revolutionizing technology and shaping the future of AI.
-

Layer 2 Tunneling Protocol (L2TP)
Layer 2 Tunneling Protocol is an Internet Engineering Task Force (IETF) standard tunneling protocol that is used to encapsulate Point-to-Point Protocol (PPP) frames for transmission over TCP/IP.
-

Layer 2 Switch
This article describes Layer 2 Switch, a form of Ethernet switch. How it operates and when to use it.
-
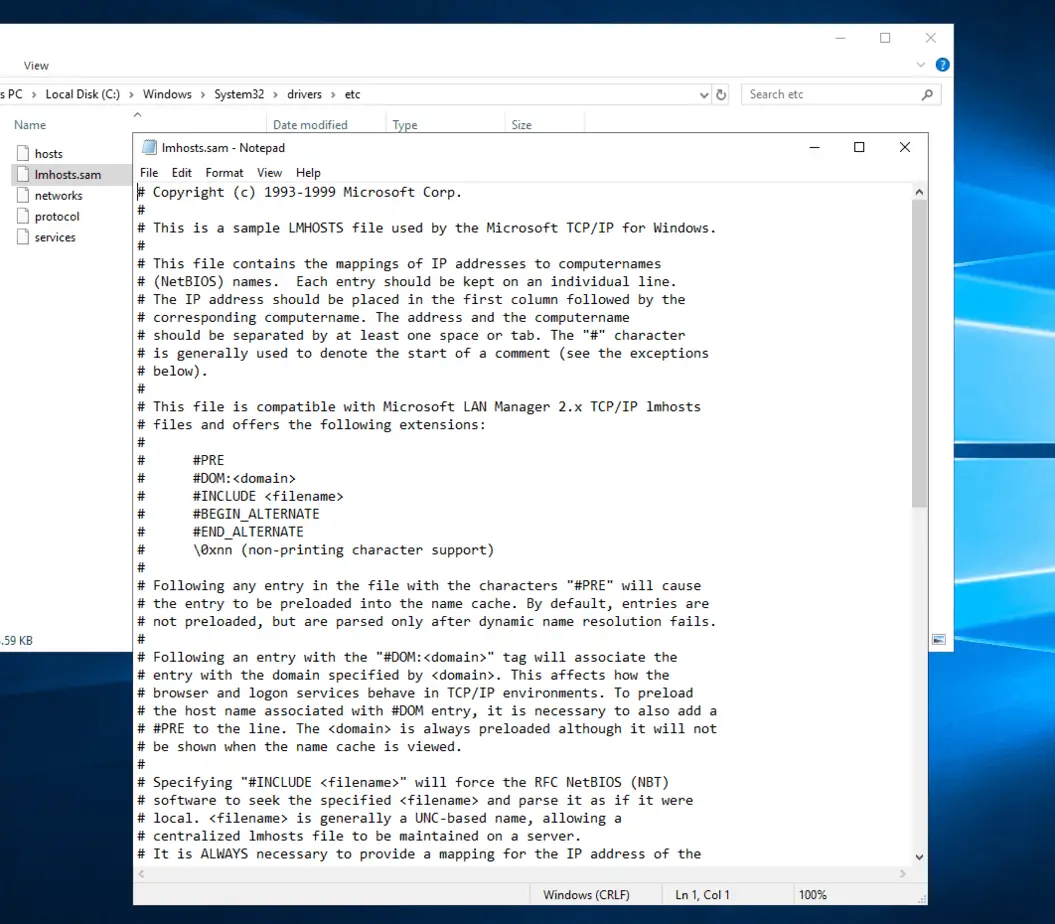
LMHOSTS file (Windows OS)
What is Lmhosts? What is it for? LMHOSTS is an ASCII file used to enable Domain Name Resolution under Windows Operating Systems when other methods, such as WINS, fail. Lmhosts stands for LAN (Local Area Network) Manager Hosts. After installing Windows, a file called Lmhosts.sam is created in C:\Windows\system32\drivers\etc. This file is just a sample…
-

Layer 4 Switch
An in-depth look at layer 4 switches, exploring their sophisticated architecture and functions. Uncover how these essential devices shape the core of modern network communication.
-
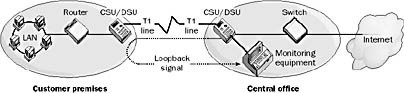
Loopback
Loopback is a testing procedure in telecommunications in which a test signal is sent from a service provider’s central office (CO) to the customer premises and is returned or echoed by the customer premises equipment (CPE) back to the service provider. Loopback tests are used to check line integrity and the proper functioning of customer…
-

Understanding the Loopback Address
A loopback address, in computer networking, is a virtual network interface primarily used for testing and network diagnostics. Technically, it refers to an IP address that routes the data back to the same device, bypassing external physical network interfaces.
-
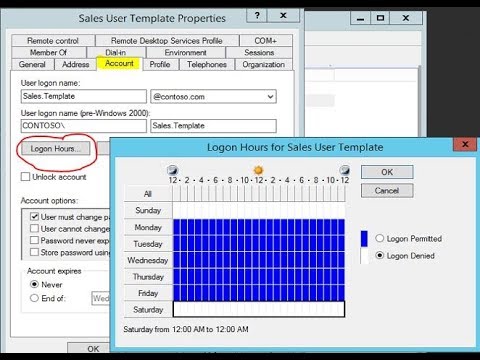
Logon Hours Restriction in Windows Server: Enhancing Security
Discover the power of logon hour restrictions in Windows Server with Active Directory. Dive into its significance, benefits, and step-by-step setup to enhance system security and operational efficiency.
