In the realm of Internet Information Services (IIS), managing anonymous access is a pivotal aspect of configuring your web server for optimal security and performance. The IUSR account, also historically known as IUSR_COMPUTERNAME or IUSR_MACHINENAME, plays a crucial role in this process.
This article aims to demystify the IUSR account, guiding you through its configuration, permissions management, and security best practices.
Table of Contents:
- What is the IUSR Account?
- Configuring Anonymous Access in IIS
- Managing IUSR Permissions
- IUSR vs. NETWORK SERVICE
- Security Best Practices
- Conclusion
- References
1. What is the IUSR Account?
The IUSR account represents a fundamental security feature within Microsoft’s Internet Information Services (IIS), designed explicitly for handling anonymous access to web servers. This built-in account is a legacy of Windows NT’s IUSR_COMPUTERNAME and has evolved into a default account in later versions of Windows and IIS, streamlining the process for granting anonymous users access to public parts of websites without compromising the overall security of the server.
Originally, each IIS installation generated a unique IUSR account named IUSR_COMPUTERNAME, where COMPUTERNAME was the actual name of the host machine. This practice allowed for a separation of permissions and security contexts between different services and applications running on the same server. In more recent versions of Windows, this has been simplified to a single predefined account named ‘IUSR’. This change was part of a broader effort to standardize security practices across different installations and reduce administrative overhead.
The IUSR account is automatically created during the installation of IIS and does not have a password that an administrator needs to manage. Instead, it’s a service account specifically for the IIS service to control anonymous access. Its primary role is to enable users to view web pages and download content without authenticating themselves to the web server.
2. Configuring Anonymous Access in IIS
Configuring anonymous access in IIS allows users to access your website without prompting for username and password credentials. This configuration is essential for serving public content over the internet.
Practical Examples
- Enabling Anonymous Authentication for a Website:
- Open IIS Manager.
- In the Connections pane, expand the server node and select the site you wish to configure.
- In the Features View, double-click “Authentication.”
- Right-click “Anonymous Authentication” and select “Enable.”
- Customizing the Anonymous User Identity: Sometimes, you might want to use a different account than the default IUSR for anonymous access, especially when dealing with specific security requirements or when accessing network resources.
- Follow the steps above to navigate to the “Anonymous Authentication” feature.
- Right-click “Anonymous Authentication” and select “Edit…”
- In the dialog, select “Application pool identity” for using the application pool’s identity or “Specific user” to specify another account. If choosing “Specific user,” click “Set” and enter the username and password for the account you wish to use.
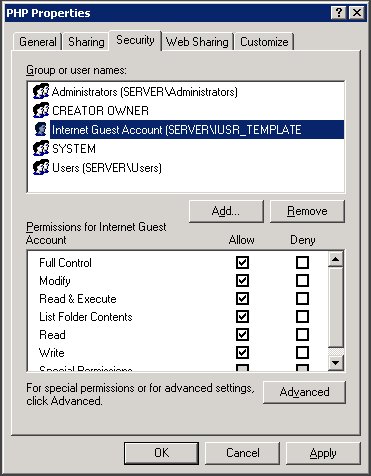
3. Managing IUSR Permissions
Managing the permissions of the IUSR account is crucial for maintaining the security and functionality of your IIS server. The account needs sufficient permissions to serve content without exposing your server to unnecessary risks.
Setting File System Permissions
- For Static Content (HTML, CSS, Images):
- Navigate to the root folder of your website in File Explorer.
- Right-click the folder and select “Properties.”
- Go to the “Security” tab and click “Edit” to change permissions.
- Click “Add,” type “IUSR” in the object names box, and click “Check Names” before pressing OK.
- With “IUSR” selected, check the boxes for “Read & execute,” “List folder contents,” and “Read.”
- Click “Apply” and then “OK” to save changes.
- For Applications (ASP.NET, PHP):
- Follow the same steps to access the “Security” tab of the application folder.
- Ensure the IUSR account has “Read & execute” permission. Additionally, if your application writes to a file or folder, such as a log file, grant “Write” permission specifically to that file or folder.
Best Practices
- Principle of Least Privilege: Always assign the minimum permissions necessary for the IUSR account to operate your website. Avoid granting “Full control” or “Modify” permissions to your entire website directory.
- Regular Audits: Periodically review the permissions assigned to the IUSR account to ensure they are still aligned with the current needs and security policies of your organization.
- Use Application Pool Identities for Isolation: Where possible, use application pool identities instead of the IUSR account for running applications. This method provides better isolation and security, especially in a hosting environment with multiple sites or applications.
By thoroughly understanding the IUSR account, configuring anonymous access appropriately, and managing permissions carefully, you can ensure that your IIS web server is secure, efficient, and accessible to your intended audience.
4. IUSR vs. NETWORK SERVICE
The distinction between the IUSR and NETWORK SERVICE accounts is crucial for Windows administrators to understand, as each serves different purposes within the context of security and access control in Internet Information Services (IIS) and other Windows services.
IUSR Account
The IUSR account is specifically designed for anonymous authentication in IIS. When a web client requests resources from an IIS server without providing explicit credentials, IIS uses the IUSR account to process the request. This account is created automatically when IIS is installed and is dedicated to managing anonymous access to web applications. The key characteristics of the IUSR account include:
- Purpose: Tailored for anonymous web access in IIS.
- Scope: Limited to IIS and web-related services.
- Security Context: Operates with minimal privileges necessary for serving static content and executing web applications that don’t require personalized user identity.
NETWORK SERVICE Account
The NETWORK SERVICE account, on the other hand, is a predefined local account used by the service control manager. It has more extensive capabilities compared to IUSR, allowing services running as NETWORK SERVICE to interact across the network under the computer’s identity. Key aspects of the NETWORK SERVICE account include:
- Purpose: Designed for services that require network access and interaction.
- Scope: Used by various Windows services beyond just IIS.
- Security Context: Has the ability to access network resources as the machine account but with constrained permissions to limit potential damage if compromised.
Key Differences
- Use Case: IUSR is optimized for anonymous web access, making it ideal for serving public content. NETWORK SERVICE is suited for services that need to communicate across a network securely.
- Security Permissions: IUSR is confined to what’s necessary for web services, minimizing its access to system resources. NETWORK SERVICE has broader permissions, especially for network interactions, but still operates under the principle of least privilege.
- Account Management: The IUSR account is managed within IIS, whereas NETWORK SERVICE is a system account managed by the Windows operating system.
5. Security Best Practices
Ensuring the security of the IUSR and NETWORK SERVICE accounts, as well as the overall security posture of your IIS server, involves adhering to a set of best practices:
Principle of Least Privilege
- Apply Strict Permissions: Grant only the necessary permissions for the IUSR and NETWORK SERVICE accounts to fulfill their roles. Avoid giving full control unless absolutely necessary.
Regular Security Audits
- Conduct Periodic Reviews: Regularly audit the permissions and roles of these accounts to ensure they align with current security policies and the principle of least privilege.
Isolation of Services
- Separate Services: Use separate accounts for different services to limit the potential impact of a security breach. Isolating services ensures that the compromise of one service does not automatically lead to the compromise of others.
Secure Configuration
- Configure Authentication: Ensure that anonymous authentication (IUSR) is enabled only for resources that require it. For services needing network access (NETWORK SERVICE), confirm that they are configured with the minimal network permissions necessary.
- Use Application Pool Identities: Where possible, use unique application pool identities instead of the NETWORK SERVICE account for running IIS applications. This approach provides better isolation and reduces the risk of cross-application breaches.
Monitoring and Logging
- Implement Logging: Enable detailed logging for access and transactions involving the IUSR and NETWORK SERVICE accounts. Regularly review logs for unusual activities that could indicate a security issue.
- Alerts for Suspicious Activities: Set up alerts for abnormal access patterns or unauthorized attempts to use these accounts, facilitating prompt detection and response to potential threats.
By understanding the differences between the IUSR and NETWORK SERVICE accounts and implementing these security best practices, administrators can significantly enhance the security of their Windows servers and protect against unauthorized access and potential breaches.
6. Conclusion
The IUSR account is a vital component of the IIS ecosystem, enabling anonymous access while maintaining security. By carefully configuring this account, managing its permissions diligently, and adhering to security best practices, you can ensure that your IIS web server provides both seamless access and robust protection.
7. References
- Microsoft Documentation on IIS
- “Professional Microsoft IIS 8” by Kenneth Schaefer, Jeff Cochran, Scott Forsyth, Dennis Glendenning, and Benjamin Perkins