Definition of Organizational Unit (OU) in Network Encyclopedia.
What is an Organizational Unit (OU)?
Organizational Unit is a type of container object in Active Directory of Microsoft Windows Server that can contain other Active Directory objects.
How It Works
An organizational unit (OU) can contain other OUs, or it can contain specific objects, such as those listed here:
- Users
- Groups
- Computers
- File shares
- Printers
- Security policies
- Applications
OUs make possible the hierarchical structure of Active Directory. Objects in the directory are grouped in tree-like structures for easier administration. OUs are displayed in Windows 2000 administrative consoles as folders, much like the folders in a file system that store individual files. OUs are logical groupings of users and resources in a domain; they simplify management of the domain by delegating administrative tasks to specific people.
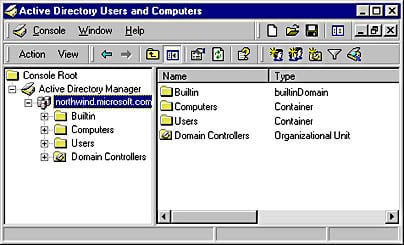
OUs are often used to duplicate the organizational structure of the company within Active Directory. For example, a company might have OUs named Dev, Marketing, and Sales that represent the network resources of these three departments. OUs can also be assigned according to geographical criteria (New York, Los Angeles, and Detroit, for example) or by administrative function (Accounts, Shares, and Printers). When you run the Active Directory Installation Wizard to install Active Directory on a server running Windows 2000 (thus turning the server into a domain controller), a default hierarchy of OUs is created. This default hierarchy helps you begin administering Active Directory. It consists of the following OUs, which you can display by using Active Directory Users and Computers, a snap-in for Microsoft Management Console (MMC):
- Builtin: Includes built-in security groups such as Administrators and Account Operators
- Computers: Includes other computers in the domain
- Users: Includes domain user objects
- Domain Controllers: Includes the domain controllers in the domain
The hierarchical structure of OUs in Active Directory also simplifies the task of querying Active Directory for information about network resources. OUs are useful in facilitating administration of Active Directory and therefore in the administration of resources on the network itself. Administrators use OUs to organize users and resources on the network, and to delegate administrative and other rights and permissions to users and groups. The administrator has full access rights on all objects in the directory and can assign permissions to various subtrees of OUs for appropriate users and groups. For any OU, the administrator can delegate either of the following rights to specific users and groups:
- Complete administrative control: Full control over all objects in the OU
- Limited administrative control: The ability to modify only certain aspects of objects contained in the OU
Access to objects in Active Directory is based on discretionary access control lists (DACLs), which offer a security model similar to that used in the NTFS file system. Because objects with similar security requirements are grouped into an OU, permissions assigned to the OU are inherited by all objects in the OU. You assign permissions to OUs and other objects by using Active Directory Users and Computers.
NOTE
If several domains are connected into a domain tree, each domain can have its own specifically designed hierarchy of OUs. The structures of domains within a domain tree are independent of one another. However, an OU can contain objects only from its own domain, not from any other domain within a domain tree.
OUs are not part of the namespace of a company, which in Windows 2000 is based on the Domain Name System (DNS). In other words, you can identify a Windows 2000 domain by using a DNS name such as northwind.microsoft.com, but you cannot identify OUs within the domain by using DNS names. However, you can specify OUs by using Lightweight Directory Access Protocol (LDAP) names.
You cannot create new OUs within the four default OUs previously listed. These default OUs simply get you started in administering your network.
TIP
To create new OUs in Active Directory, select the desired parent container in Active Directory Users and Computers, and choose Organizational Unit from the New submenu of the Action menu. You can also use the console toolbar. The only information you need to specify when you create a new OU is its name.
When you create an OU, you should consider who will own and manage it and who will be responsible for the following tasks:
- Adding objects to or deleting objects from the OU
- Modifying the values of attributes of objects in the OU
- Managing permissions on the OU and its objects, and delegating the permissions to others
You can create OUs for groups of users who will be assigned similar permissions to network resources. You can also create separate OUs for permanent and temporary employees. You can group shared folders and printers with similar security requirements into OUs.
You should create OUs that are stable and will not change frequently, and you should avoid making the hierarchy of OUs too complicated. In a multidomain scenario with a domain tree, it is usually a good idea to make first-level OUs the same for all domains to provide consistency for the company’s network resources. First-level OUs typically represent the following:
- Different geographical locations, such as countries or continents, or different functional locations, such as headquarters and branch offices. This is usually the best way to define first-level OUs.
- Different types of network resources, such as users, printers, computers, and so on. This simplifies resource administration but might lead to too many first-level OUs.
- Different business units, such as Sales, Support, and Management. Keep it flexible and broad enough so that if your company reorganizes, you won’t have to re-create everything.
- Projects and cost centers.
Keep the entire structure of OUs fairly shallow – no more than two or three levels – to ensure good performance when users query Active Directory. A maximum of 10 levels of OUs is recommended.
You can use OUs in place of resource domains, which are used in Windows NT to simplify and centralize administration of network resources. You can also create domain trees with separate domains for resources. You should create new domains instead of OUs if you want to implement different security policies in different locations or branches of your company or in an extremely large enterprise. Otherwise, it is simpler to create only one domain and organize resources and administrative tasks using OUs within that domain.