Welcome to our special corner featuring articles that have undergone a significant update. In this fast-paced world of technology and business management, information quickly becomes obsolete. We believe in delivering not just current but also accurate and in-depth content.
Here, you will find updated articles that have been carefully revisited, revised, and enriched by our expert team to make them even more informative, accurate, and relevant for you. Browse through these gems, and you’ll find new insights added to what you may already know.
The articles are sorted from the most recently updated to the oldest. Dive in, refresh your knowledge, and keep up with the latest information without having to sift through new articles.
Updated Articles
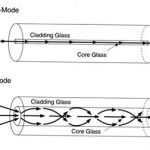
Single-Mode Fiber-Optic Cabling:
Updated on: April 23, 2024
Imagine a highway so efficient that only one type of vehicle could drive on it — one that’s incredibly fast and never gets caught in traffic. Now, replace that vehicle with a beam of light, and you have the essence of single-mode fiber-optic cabling. In this article, we’re going to explore the fascinating world of […]

Introduction to BitLocker: The Digital Vaultkeeper
Updated on: April 23, 2024
Unlock the secrets of BitLocker, Microsoft’s fortress for digital data. Discover how this powerful encryption tool locks down your information, ensuring that only you hold the key to your digital kingdom. From basic setup to in-depth security strategies, learn how BitLocker can protect your data from prying eyes and sneaky cyber thieves.

Introduction to the Sandbox: Your Digital Playground
Updated on: April 22, 2024
Dive into the digital playground of sandboxes where safety and innovation play nice together. Explore how sandboxes create secure environments for testing and development, their various types, and their pivotal role in enhancing security across technologies. Discover the future trends of sandboxing in this comprehensive guide.

Ethics in Machine Learning: Navigating the New Frontier
Updated on: April 20, 2024
Dive into “Ethics in Machine Learning: Navigating the New Frontier,” a manual exploring the ethical challenges of AI. From bias and privacy to accountability, learn to harness AI’s power responsibly. Perfect for pioneers eager to ensure technology enhances humanity without crossing dark borders.

Computer Networks: A Starter Exploration
Updated on: April 19, 2024
Dive into the essentials of computer networks with this authoritative guide, crafted to demystify the complex interactions and technologies that connect computers globally.

Understanding Dynamic Adaptive Streaming over HTTP (DASH)
Updated on: April 19, 2024
Explore the essentials of Dynamic Adaptive Streaming over HTTP (DASH), the technology revolutionizing media delivery online.

The Modern Role of Tape Backup in Data Storage
Updated on: April 18, 2024
Tape Backup is a general term for a class of devices for backing up data to a magnetic tape for disaster recovery planning and archiving purposes. A number of technologies with incompatible tape formats have been implemented in these devices.

Phishing Exposed: Understanding Digital Deception
Updated on: April 18, 2024
Delve deep into the dark world of Phishing, as we unravel the mechanics of this notorious cyber menace, empowering you to navigate the digital realm securely

Client-Server Model
Updated on: April 18, 2024
Explore the intricacies of the Client-Server Model with our comprehensive guide. Learn its history, advantages, future trends, and how it drives modern computing.