In the constantly evolving landscape of the internet, there emerges a plethora of cyber threats that challenge the very fabric of our digital security. Among the myriad of threats, phishing stands out as a notorious behemoth, ensnaring unsuspecting victims daily. This deceptive tactic has seen numerous incarnations and adaptations throughout the years, a testament to the evolving sophistication of cybercriminals. Today, we’ll embark on a journey, cutting through the chaff of myths surrounding phishing, offering insights, and illuminating pathways that safeguard one’s digital presence.
In this article:
- What is Phishing?
- Historical Overview of Phishing: Tracking its Insidious Evolution
- Mechanics of a Phishing Attack: How do Cybercriminals Orchestrate Their Deceptions?
- Common Phishing Techniques: Recognizing Spear Phishing, Whaling, and More
- The Psychology Behind Phishing: Understanding the Human Elements
- Real-life Case Studies: Analysis of High-Profile Phishing Incidents
- Detecting Phishing Attempts: Tools and Techniques for Identification
- External References
Phishing, a term that might sound innocuous, if not a tad playful, bears the weight of billions in stolen assets and has left an indelible mark on the corporate world, as well as individual lives. Beyond the monetary implications, it threatens the core of personal privacy and data sanctity. As the digital age unfolds, understanding phishing is no longer a luxury but an imperative. With this guide, we endeavor to equip our readers, particularly computer science students, with the knowledge and acumen to recognize, combat, and champion the fight against this insidious adversary.

What is Phishing?
Phishing, at its core, is an act of digital deception wherein attackers masquerade as trustworthy entities to steal sensitive data such as usernames, passwords, credit card details, and other personal information. Deriving its name from the word ‘fishing,’ phishing encapsulates the act of casting a baited line into the vast ocean of the internet, hoping for an unsuspecting user to bite.
This nefarious technique typically involves the use of emails, instant messaging, or even phone calls, laced with urgent messages designed to instill panic, curiosity, or a false sense of security. By leveraging elements of social engineering, these communications lead victims to fraudulent websites. These websites are doppelgangers of legitimate sites, designed meticulously to extract sensitive information. Often, the lines between a legitimate website and its fraudulent twin are blurred, and only the discerning eye, empowered with knowledge, can spot the discrepancies.
Historical Overview of Phishing: Tracking its Insidious Evolution
The history of phishing is a riveting tapestry of digital deceit and ingenuity, offering a lens into the world of cybercrime and the perpetual tug-of-war between attackers and defenders. While the term ‘phishing’ and the tactics we associate with it are inherently digital, its conceptual roots can be traced back to much older cons and scams.
Birth of Phishing
The birth of phishing, as we understand it today, finds its origins in the 1990s, a time when the internet was a burgeoning frontier. The earliest recorded instances of phishing involved a group of hackers nicknamed the “warez community.” These digital desperados would exploit the trust of AOL users. They utilized instant messaging, hoodwinking victims into revealing their passwords. Their tactics were primitive, often employing simple messages like “Hi, I work for AOL. Can you please confirm your account details?” Given the novelty of the internet for many users during this era, many fell prey to these early phishing attempts.
Nigerian Prince
However, like all forms of deception, phishing began to evolve in both complexity and sophistication. The turn of the century saw cybercriminals exploiting more than just naivety; they began crafting meticulous and intricate emails that mimicked legitimate corporations, banks, and even governmental agencies. The infamous ‘Nigerian Prince’ scams, a cultural hallmark of early internet folklore, emerged during this period. These emails spun tales of vast fortunes trapped overseas, requiring just a small ‘fee’ to unlock, ensnaring many an unsuspecting individual.
2013 Target breach
As technology progressed, so did the tools at a phisher’s disposal. By the 2010s, phishing had become an enterprise, with cybercriminal rings utilizing vast networks of botnets, crafting phishing kits available for purchase on the dark web, and constantly refining their approach. The sophistication of these attacks culminated in events like the 2013 Target breach, which saw the personal data of over 70 million individuals compromised, all starting with a single phishing email.
Reflecting on this history, we see not just a chronicle of cybercrime but a reflection of human adaptability. Each era of phishing tells a story: the tale of attackers identifying gaps in our collective understanding and exploiting them, and of a society constantly playing catch-up, learning, adapting, and fortifying itself against the next wave of deception. As we move forward in the digital age, the history of phishing serves as both a cautionary tale and a testament to the ever-evolving nature of cyber threats.
This cat-and-mouse game between cybercriminals and netizens underscores the importance of continuous education, vigilance, and adaptation. With the knowledge of where phishing has been, we can better predict and prepare for where it might go next.
» You may also like: Understanding Critical Applications!
Mechanics of a Phishing Attack: How do cybercriminals orchestrate their deceptions?
The underbelly of a phishing attack is a labyrinthine ensemble of strategic planning, precise execution, and an uncanny understanding of human behavior. As we dive into this murky world, we’ll dissect the art and science that fortifies these deceptions, unearthing the strategic orchestrations of cyber criminals.
1. Reconnaissance
Every grand deception begins with meticulous research. In this stage, attackers identify their targets, which could range from individuals to massive corporations. Cybercriminals might employ open-source intelligence techniques (OSINT), scraping public records, social media, and websites to gather information that makes their subsequent phishing emails more convincing.
2. Crafting the Bait
With a wealth of knowledge on their targets, attackers begin crafting their messages. Here, they exploit known human biases, such as urgency (e.g., “Your account will be suspended!”) or authority (e.g., mimicking communication from a CEO). The content is finessed to bypass spam filters, employing tactics like domain spoofing, where they use domains visually similar to legitimate ones (e.g., ‘amaz0n.com’ vs. ‘amazon.com’) or incorporating benign-looking attachments that cloak malicious payloads.
3. Technical Infrastructure
Behind the scenes, the attacker sets up the technical aspects of the trap:
- Domain Acquisition: Purchasing domains that either spoof legitimate brands or contain keywords designed to instill trust.
- Website Cloning: Creating a facsimile of legitimate websites, ensuring the look and feel are indistinguishable from the original.
- Payload Preparation: If the goal is malware distribution, attackers will often pack or encrypt the malware to make detection harder for traditional antiviruses.
- Command and Control Servers (C2): These servers allow attackers to control compromised systems remotely.
4. Casting the Net
The phishing emails are sent en masse or to specific targets, depending on the nature of the attack (general phishing vs. spear phishing).
Advanced attacks might use botnets – networks of compromised devices – to send these emails, making tracing the origin more challenging.
5. The Catch
Once a user takes the bait, several outcomes may unfold:
- They might be redirected to a cloned site, where their login credentials or personal information is harvested.
- Malicious attachments, when opened, may exploit known vulnerabilities in software to execute code, potentially installing ransomware, trojans, or keyloggers.
- The attacker gains an initial foothold, which can be exploited further for lateral movement within networks, especially in corporate environments.
6. Exfiltration and Exploitation
Captured data, whether personal details or corporate secrets, is extracted. Cybercriminals might sell this information on the dark web, use it to commit identity theft, or even leverage it for further targeted attacks.
7. Covering Tracks
To evade detection and prolong their illicit access, cybercriminals employ techniques to erase logs, employ encrypted channels to communicate with their C2 servers, or even use proxies to bounce their connections across multiple geographic locations.
Understanding these mechanics doesn’t just satiate our curiosity; it provides invaluable insight into the multi-faceted strategies employed by attackers. By appreciating this complexity, we recognize the urgency to adopt holistic cybersecurity measures – because while the phishing email is the tip of the iceberg, there’s a vast structure of deception submerged below the surface.
» To read next: What is Security Assertion Markup Language?
Common Phishing Techniques: Recognizing spear phishing, whaling, and more
The universe of phishing is not monolithic; it’s a constellation of techniques, each tailored for distinct targets and outcomes. As we chart these stars, it becomes evident that while each type might differ in approach, their endgame remains constant: deception for exploitation. Today, we navigate through the most prominent techniques, arming ourselves with the knowledge to identify and thwart them.
1. Spear Phishing
The Sniper’s Approach.
Unlike the scattergun method of traditional phishing, which targets a broad audience, spear phishing is laser-focused. The attacker painstakingly researches a specific individual or organization to craft a highly personalized message. Such emails might reference recent transactions, known associates, or ongoing projects to appear genuine. The precision of spear phishing, while labor-intensive, often yields a higher success rate due to its seemingly legitimate context.

2. Whaling
Hunting the Big Fish.
Even within the hierarchy of spear phishing lies a subset targeting the very top echelon: the C-level executives, the high-ranking officers. Dubbed ‘whaling,’ these attacks are tailored for the big fish – the CEOs, CFOs, and other titans of industry. Given the vast authority these individuals wield, compromising their accounts or deceiving them can lead to substantial illicit gains, whether monetary or informational.
3. Vishing (Voice Phishing)
Deception on the Line.
While phishing is often associated with emails, cybercriminals have not overlooked the trusty telephone. Vishing involves voice calls where the attacker impersonates bank officials, tech support, or any other authority figure to extract personal details or financial information. With the rise of VoIP services, these attacks can be orchestrated on a massive scale and masked with deceptive caller IDs.
4. Smishing (SMS Phishing)
Textual Deceit.
In an age dominated by smartphones, text messages become a potent vector for deception. Smishing employs alarming or enticing text messages luring recipients to click on shortened or cloaked links, leading to malicious sites or triggering malware downloads.
5. Pharming
Domain Deception.
Pharming doesn’t wait for a user to take the bait; it redirects them to fraudulent websites without their knowledge. By exploiting vulnerabilities in DNS servers or altering a victim’s host file, attackers ensure that even if you type in the correct web address, you’re led astray. The site you land on, while a spitting image of the genuine one, is a trap set to harvest information.
6. Watering Hole Attack
Predator and Prey.
Instead of targeting the victim directly, attackers focus on frequented places, like a lion targeting a watering hole. They identify websites or online resources their targets frequently visit and compromise them, lying in wait for the prey to arrive and get infected or deceived.
7. Clone Phishing
Mirror Images.
Here, attackers replicate legitimate messages from trusted sources but alter the content slightly to introduce their malicious intent. This might involve changing a link or attachment to a malicious version, capitalizing on the trust previously established by the original sender.
8. Pop-Up Phishing
Digital Masquerades.
These are unsolicited browser windows mimicking legitimate sites, often prompting users to input sensitive information. Their sudden appearance, coupled with a false sense of urgency (e.g., “Your PC is at risk!”), can catch users off-guard.
Recognizing the myriad ways cybercriminals ply their deceptive trade is the first step in creating an armor of vigilance. As these techniques morph and evolve, our understanding of them must too. It’s a dynamic dance, one where awareness, skepticism, and continuous education are our best moves against an ever-adaptive adversary.
The Psychology Behind Phishing: Understanding the Human Elements
At its core, phishing is more than just a technological exploit—it’s a psychological play. It hinges on the manipulation of human behavior, leveraging the intricacies of our minds against us. This chapter explores the cognitive and emotional triggers that cybercriminals prey upon, making their deceptions so dangerously effective.
1. Trust and Familiarity
The Trojan Horse Tactic.
Humans inherently trust known entities—family, friends, familiar brands. Attackers exploit this by masquerading as these trusted figures. This is why a phishing email disguised as a message from your bank or a popular online service can instantly lower defenses, prompting swift and often regrettable action.
2. Curiosity Killed the Cat
The Lure of the Unknown.
An enigmatic email title such as “You won’t believe what I found about you online!” can stimulate innate curiosity. This tantalizing bait often leads victims into the phisher’s trap, as they’re compelled to click on links or download attachments.
3. Urgency and Fear
Tick-tock Tactics.
Fear is a potent motivator. Cybercriminals know that inducing panic—like sending an “urgent” notice about a compromised account—can cloud judgment. Under the adrenaline rush of potential threat, individuals are more likely to impulsively click on links without scrutiny.
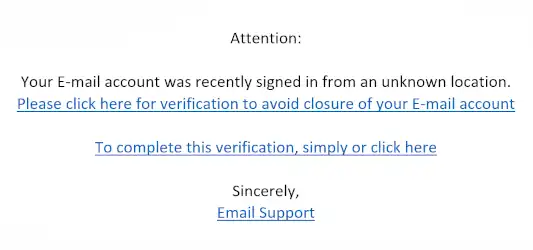
4. Authority and Obedience
Pulling Rank.
From a young age, we’re conditioned to respect and follow authority. Phishing scams capitalizing on this will impersonate CEOs, law enforcement, or other figures of authority, banking on the fact that people are less likely to question such figures and more likely to comply with their directives.
5. Social Proof
Following the Herd.
“Your friends have joined this app! Click here to see what they shared!” Such messages lean on our inherent desire to belong, to be part of the in-group. This notion of ‘everyone’s doing it’ can be a powerful force, pushing even skeptical users into the snare.
6. Reciprocity
The Give and Take.
Humans have an intrinsic desire to return favors. Phishing campaigns might offer something—a gift, exclusive access, a deal. This ‘generosity’ can sometimes create a subconscious obligation in the victim’s mind, making them more likely to engage or share information in return.
7. Commitment and Consistency
The Slow Boil.
Some phishing campaigns play the long game. They engage targets over a period, fostering a rapport and trust. As humans, once we commit to a particular path or person, cognitive dissonance nudges us to remain consistent with our prior actions, making us more susceptible over time.
8. Overload and Distraction
The Magician’s Sleight.
Much like a street magician using distraction to complete a trick, some phishing attempts will intentionally overload users with information, causing them to miss subtle cues or red flags.
By delving into the psychological foundations of phishing, it becomes glaringly apparent that these attacks are a blend of art and science. The art lies in understanding human nature and behavior, while the science is in the precise execution of the attack. To be truly cyber resilient, we must fortify not just our systems, but also our minds. It’s a journey of continuous self-awareness, learning, and adaptation in the face of ever-shifting tactics that assail our most human instincts.
Real-life Case Studies: Analysis of high-profile phishing incidents
Every phishing incident serves as a stark reminder of the intricate confluence of technical prowess and psychological cunning that cybercriminals employ. However, high-profile cases, given their far-reaching impact and the heightened attention they garner, offer invaluable lessons. In this chapter, we shine a spotlight on a few such incidents, unraveling the mechanics and consequences of each.
1. The 2016 DNC Email Leak
Politics and Phishing.
In what stands as a watershed moment in political cybersecurity, the Democratic National Committee’s (DNC) emails were compromised in 2016. Spear phishing played a pivotal role. Key individuals received emails urging them to reset their passwords, which redirected to a fake login page—effectively capturing their credentials. The ramifications were far-reaching, including the dissemination of sensitive emails and a profound impact on the U.S. elections.
- Lessons Learned: Even the most vigilant can fall prey to a well-crafted spear phishing attack, underscoring the need for multi-factor authentication and continuous cybersecurity training.
2. The 2013 Target Data Breach
Entry through a Backdoor.
One of the largest retail breaches in history saw Target’s payment systems compromised, leading to the theft of 40 million credit and debit card records. The breach’s genesis? A phishing email sent to an HVAC contractor affiliated with Target. Once inside the contractor’s systems, the attackers leapfrogged to Target’s network.
- Lessons Learned: A chain is only as strong as its weakest link. Organizations must ensure that not only their systems but also those of their partners and affiliates are fortified against cyber threats.
3. Operation Aurora – Google, 2009
Silicon Valley Under Siege.
A sophisticated series of cyber-attacks, dubbed “Operation Aurora,” targeted several top-tier companies, including Google. Spear phishing was a key vector, where employees were sent a link to a malicious website, ultimately compromising their machines. This breach not only led to intellectual property theft but also access to some Gmail accounts.
- Lessons Learned: No entity, regardless of its technological prowess, is invincible. Regular patching, network segmentation, and a zero-trust model are imperative in safeguarding organizational assets.
4. Wombat Security Breach, 2014
Irony Strikes.
In an ironic twist, Wombat Security, a company specializing in phishing awareness training, became a victim of phishing itself. A targeted spear phishing email allowed attackers to compromise the system and gain access to user data.
- Lessons Learned: Complacency is a cybercriminal’s best friend. Constant vigilance, updated security protocols, and never resting on one’s laurels are essential.
5. The AP Twitter Hack, 2013
140 Characters, $136 Billion Fallout.
When the Associated Press’s Twitter account tweeted about explosions at the White House injuring then-President Obama, stock markets plunged, wiping out $136 billion in value. It was a hoax—a result of a spear-phishing email received by an AP employee.
- Lessons Learned: The integration of digital platforms with real-world systems can have tangible consequences. Beyond financial safeguards, we must invest in ensuring the veracity of digital information.
Diving deep into these high-profile incidents reveals that phishing is not a mere annoyance—it’s a critical threat with genuine, often monumental repercussions. Yet, with each breach comes enlightenment—a roadmap on pitfalls to avoid, strategies to embrace, and the reaffirmation that vigilance, in the digital realm, is not just a virtue but a necessity.
» You may also like: What is Optical Burst Switching (OBS)?
Detecting Phishing Attempts: Tools and Techniques for Identification
In the labyrinthine digital expanse, phishing attempts are akin to camouflaged predators lying in wait for their prey. But what if we could train our eyes to discern these hidden threats, to spot the anomalies amidst the familiar? Armed with the right tools and techniques, one can significantly enhance their ability to identify and sidestep these digital pitfalls. Let’s embark on this enlightening journey of detection.
1. Email Header Analysis
Peering Behind the Curtain.
Every email comes with a ‘header’—a digital footprint revealing its journey through the web. By scrutinizing an email’s header, you can trace its origin and verify its legitimacy. Look for discrepancies such as mismatched ‘From’ addresses or unfamiliar servers. Tools like MXToolbox and EmailHeaderAnalysis can aid in dissecting these headers.
2. URL Inspection
Beyond What Meets the Eye.
Hovering over hyperlinks without clicking can unveil the actual URL destination. Phishers often employ shortened URLs or craftily misspelled domains to cloak their deceptive sites. Bookmarking essential websites and using URL expanders like CheckShortURL can prove invaluable.
3. SSL Certificates
The Digital Seal of Authenticity.
Legitimate websites often use SSL (Secure Socket Layer) to encrypt data. When browsing, look for the padlock icon next to the URL or the prefix ‘https’ as a sign of security. However, be cautious; some phishing sites also use SSL. Certificate Transparency logs and tools like SSL Labs’ SSL Test can further verify a site’s authenticity.
4. Multi-factor Authentication (MFA)
Double-Locking Digital Doors.
Even if phishers acquire login credentials, MFA can stymie unauthorized access. By necessitating a secondary verification step—like a texted code or fingerprint scan—MFA adds an invaluable layer of security.
5. Anti-phishing Toolbars
Guardians of the Browser.
Several browsers offer anti-phishing toolbars that actively compare the websites you visit against databases of known phishing sites. If you’re about to step into a trap, these toolbars sound the alarm.
6. AI and Machine Learning
Future-tech Watchdogs.
Emerging technologies like AI and ML are being harnessed to detect phishing attempts proactively. They analyze vast datasets, learning patterns of phishing attacks, and subsequently warning users of suspicious content or behaviors in real-time.
7. Heuristic Analysis
Pattern Recognition.
Heuristic analysis in cybersecurity tools identifies common tactics and patterns associated with phishing. By checking for characteristics typical of phishing attacks rather than known signatures, it can even detect new, previously unidentified attempts.
8. Regular Training and Simulations
Forewarned is Forearmed.
Periodic training sessions coupled with simulated phishing tests can bolster an organization’s human firewall. Platforms like GoPhish or PhishMe help orchestrate these simulations, providing a safe environment to learn and test awareness.
9. Email Filtering Solutions
Sentries of the Inbox.
Advanced email filtering solutions go beyond standard spam filters. They scrutinize incoming emails for malicious attachments, links, and typical phishing patterns, quarantining suspicious messages before they reach the inbox.
As we navigate the vast, interconnected digital seas, these tools and techniques are our compass and lighthouse, guiding us away from potential dangers. The key is a balanced synergy between human vigilance and technological prowess. With every phishing attempt thwarted, we not only safeguard our data but also send a resounding message to cybercriminals: We are alert, aware, and always a step ahead.
» To read next: Planning a Campus Network.
External References
Books:
- “Phishing Dark Waters: The Offensive and Defensive Sides of Malicious Emails” by Christopher Hadnagy and Michele Fincher. An in-depth look into the art of phishing, offering both an understanding of attacks and methodologies to defend against them.
- “Phishing Exposed” by Lance James. A dive into the world of cyber deception, understanding the techniques and mindsets of phishers.
- “The Web Application Hacker’s Handbook: Finding and Exploiting Security Flaws” by Dafydd Stuttard and Marcus Pinto. While not exclusively about phishing, it provides valuable insights into broader web vulnerabilities.
- “Phishing for dummies – Cisco Special Edition”, by Gabrielle Bridgers, Christina Hausman, Adam Tomeo, and Ganesh Vellala Umapathy [Free eBook]
Websites:
- Anti-Phishing Working Group (APWG): An international consortium that brings together businesses affected by phishing attacks, security products, and services companies.
- PhishTank: A free community site where anyone can submit, verify, track, and share phishing data.
- Google’s Transparency Report on Safe Browsing: Offers insights into unsafe web resources and provides lists of websites flagged for phishing and malware.
Scholarly Papers and Studies:
“Why Phishing Works”
- Authors: Rachna Dhamija, J. D. Tygar, and Marti Hearst.
- Synopsis: This paper delves into the success of phishing strategies, focusing on user vulnerabilities. Found in the Proceedings of the SIGCHI Conference on Human Factors in Computing Systems.
- [Read article]
“Email Phishing: Getting You On The Hook”
- Author: Rob Larson.
- Synopsis: How cyber attacks are evolving and how to protect yourself online.
- [Read Article]
“Spear Phishing”
- Authors: CPNI
- Synopsis: This paper describes how Spear Phishing attacks work, the likelihood of being targeted, and the steps an organization can take to manage the business risks.
- [Download Paper]
“An Empirical Analysis of Data Deletion and Opt-Out Choices on 150 Websites”
- Authors: Hana Habib, Carnegie Mellon University; Yixin Zou, University of Michigan; Aditi Jannu, Neha Sridhar, Chelse Swoopes, Alessandro Acquisti, Lorrie Faith Cranor, and Norman Sadeh, Carnegie Mellon University; Florian Schaub, University of Michigan.
- Synopsis: While not exclusively about phishing, this paper explores data practices that can indirectly feed into phishing vulnerabilities. Presented at the USENIX Security Symposium.
- [Read Article]
Harnessing the power of these resources, readers can embark on a transformative journey, transitioning from being passive receivers of knowledge to proactive defenders against the cyber onslaught of phishing. As the landscape of cyber threats continues to evolve, this curated list serves as a foundational stepping stone, propelling one toward deeper understanding and vigilant preparedness.