Welcome to this comprehensive manual on computer networks, designed to unravel the intricacies of interconnected systems that form the backbone of modern computing. The goal of this manual is to provide a clear, structured understanding of computer networks, from the foundational principles to advanced applications. By the end of this manual, you will be equipped with the knowledge to understand how different network types function, the protocols that govern communication, and the technologies that drive this fascinating area of computer science.
In crafting this manual, we aim to make the concepts accessible while ensuring that the material is thorough and technically precise. Whether you are a student, a professional, or an enthusiast, this guide will help you grasp the essential aspects of networking without needing to consult additional sources.
Table of Contents:
- What is a Network of Computers?
- Historical Evolution of Computer Networks
- Understanding Network Topologies
- Networking Hardware
- Networking Software
- Network Protocols
- Network Security
- Emerging Network Technologies
- Case Studies and Practical Applications
- References

1. What is a Network of Computers?
A network of computers, simply put, is a collection of interconnected devices that share resources and data. These connections can be established using a variety of methods including cables, radio waves, and infrared signals. The primary purpose of a computer network is to facilitate communication and resource sharing, which enhances functionality and efficiency.
1.1 Definition and Key Concepts
At its core, a computer network involves two or more computers that connect using physical and/or wireless technologies to exchange information and share resources. Each device on the network, often referred to as a node, can send and receive data, thereby promoting collaboration and information dissemination across the network.
1.2 Types of Networks
Networks vary widely in size, scope, and functionality. They can range from simple local area networks (LANs) connecting a few devices in a single office, to vast wide area networks (WANs) that span across geographical boundaries. Here are the primary types of networks:
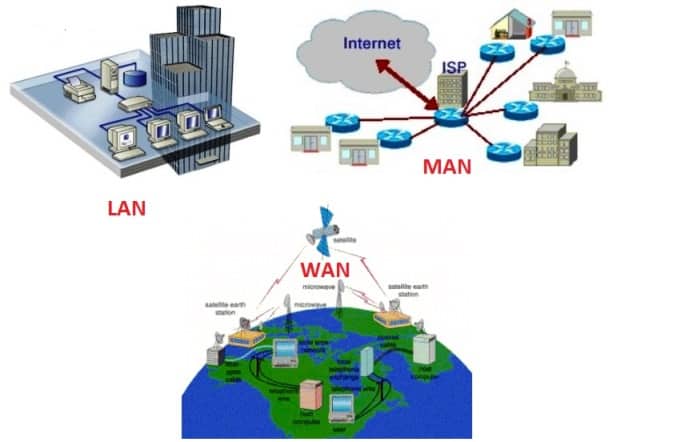
- Local Area Network (LAN): Connects computers within a limited area such as a building or campus.
- Wide Area Network (WAN): Covers broader geographic distances than a LAN, linking computers across cities, countries, or even continents.
- Metropolitan Area Network (MAN): Spans a city or a large campus.
- Personal Area Network (PAN): Connects devices within the reach of an individual, typically within a range of 10 meters.
Moreover, the network’s design often hinges on its purpose and the specific needs of its users. Networks are also classified based on their architecture and the protocols they use, which we will explore in subsequent chapters.
In conclusion, understanding the fundamentals of computer networks sets the stage for exploring more complex networking concepts and technologies. As we proceed, keep in mind that the effectiveness of a network relies heavily on its design and implementation strategies.
2. Historical Evolution of Computer Networks
2.1 Early Developments
The concept of computer networking emerged in the late 1950s with the advent of the military and academic need to share information across multiple locations. Initially, these networks were primitive, using dedicated lines to connect terminals to mainframe computers. The real breakthrough came with the creation of packet switching technology in the 1960s, pioneered by Paul Baran and Donald Davies. This technology laid the foundational principle for data to be sent in small blocks (packets), independently across a network, finding the most efficient route to its destination.
The establishment of ARPANET in 1969 marked a significant leap forward. Funded by the U.S. Department of Defense, ARPANET initially connected four major universities, facilitating the exchange of data and leading to the development of early protocols like NCP (Network Control Protocol).
2.2 Milestones in Networking Technology
Throughout the 1970s and 1980s, networking technology witnessed several milestones that shaped its modern form:
- Introduction of Ethernet (1973): Developed by Robert Metcalfe and Xerox PARC, Ethernet became a standard for linking computers within local networks, allowing multiple devices to access shared media.
- Development of TCP/IP (1983): The introduction of the TCP/IP protocol suite by Vinton Cerf and Bob Kahn enabled different types of networks to interconnect, which eventually led to the formation of the Internet.
- Commercialization of the Internet (1990s): The Internet transitioned from a research and military network to a commercial and public infrastructure, highlighted by the emergence of the World Wide Web, invented by Tim Berners-Lee.
These developments not only expanded the capabilities and applications of networks but also standardized many aspects of networking, leading to the global and highly accessible Internet we know today.
3. Understanding Network Topologies
3.1 Common Topologies Explained
A network topology refers to the arrangement of elements (including nodes, links, and their physical or logical connection) within a computer network. Understanding these arrangements is crucial for efficient network planning and operation. Here are the most common types of network topologies:
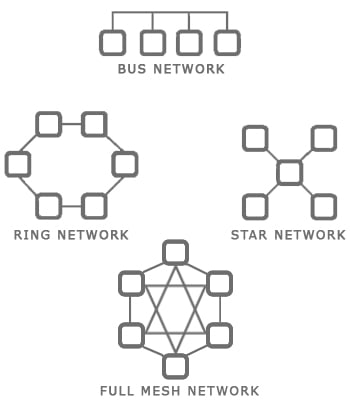
- Bus Topology: In this setup, all devices share a single communication line or bus that has two endpoints. It is simple and effective for small networks but can face performance issues as network size increases.
- Star Topology: Each device connects to a central hub. This topology is widely used due to its inherent fault tolerance – if one link fails, only the connected device is affected.
- Ring Topology: Devices are connected in a circular format, where each computer connects to two others. This topology is beneficial for managing data traffic in a predictable direction but can suffer from a single point of failure.
- Mesh Topology: Every node is connected to every other node. This setup enhances the redundancy and reliability of the network but requires significant cabling and maintenance, especially in full mesh configurations.
- Hybrid Topology: A combination of two or more different topologies, hybrid topology inherits the benefits (and sometimes the disadvantages) of each base topology used.
3.2 Choosing the Right Topology
Selecting the appropriate network topology depends on several factors, including:
- Scale and Scope: The size and geographic distribution of the network influence whether a simple or more complex topology is suitable.
- Budget and Resources: Some topologies, like mesh, are costly and complex to implement and maintain, making them less ideal for organizations with limited resources.
- Performance Requirements: Consider the data traffic and bandwidth requirements. Topologies like star or mesh might be preferred in environments requiring high reliability and intensive data transmission.
- Future Scalability: Consider how the network might need to grow or change over time. A flexible topology like hybrid can accommodate various expansion scenarios.
By evaluating these considerations, network designers can choose the most appropriate topology that meets the needs of the organization while balancing cost, complexity, and future growth.
4. Networking Hardware
4.1 Routers, Switches, and Hubs
Understanding the roles and functionalities of routers, switches, and hubs is fundamental to grasping how networks operate.
- Routers: Routers are critical devices that manage traffic between different networks by determining the best path for sending data across a network. They use protocols such as ICMP to communicate with each other and configure the best route between any two hosts.
- Switches: Switches connect devices within the same network segment, creating a network. They receive incoming data packets and redirect them to their destination on a local area network (LAN) using MAC addresses. Unlike hubs, switches can reduce network traffic by sending data only to the intended recipient.
- Hubs: A hub is a basic networking device that connects multiple Ethernet devices, making them act as a single network segment. Hubs transmit data packets to all connected devices, regardless of the intended recipient, which can lead to collisions and network inefficiency in larger networks.
These devices are essential for the creation and management of networks, each serving distinct but complementary roles.
4.2 Firewalls and Modems
- Firewalls: A firewall is a network security device that monitors incoming and outgoing network traffic and decides whether to allow or block specific traffic based on a defined set of security rules. Firewalls are crucial for protecting networked computers from unauthorized access and threats such as viruses and worms.
- Modems: Modems (modulator-demodulator) are hardware devices that convert data into a format suitable for a transmission medium and then transmit and receive data over that medium. They can be used with various types of communication media, including telephone lines, cable, and DSL, to connect to the internet.
Both firewalls and modems are pivotal in ensuring the effective and secure operation of computer networks.
5. Networking Software
5.3 Network Operating Systems
Network Operating Systems (NOS) are software systems that manage network resources and enable functionality such as file sharing, printer access, communications, and application services. Examples include Microsoft Windows Server, UNIX, and Linux-based systems like Ubuntu Server. These operating systems offer various features critical for network management, including security, user administration, and resource allocation, enabling seamless communication and data management across the network.

5.2 Management and Monitoring Tools
Network management and monitoring tools are essential for maintaining the health, performance, and security of a network. These tools can detect, diagnose, and resolve network issues, ensuring optimal network operation. Examples include:
- SNMP Tools: Simple Network Management Protocol (SNMP) tools help in monitoring network-attached devices for conditions that warrant administrative attention.
- Network Analyzers: Tools like Wireshark allow network administrators to monitor network traffic, analyze it, and troubleshoot network problems.
- Configuration Management Tools: These tools, such as Ansible and Puppet, automate the configuration and management of network devices.
- Performance Monitoring Tools: Software like SolarWinds or Nagios monitors network and application performance to ensure that performance benchmarks are met.
Using these tools, network administrators can ensure that the network remains reliable, secure, and efficient, addressing potential issues before they impact the network’s functionality. These software solutions are indispensable for modern network management, providing the necessary oversight and control over complex networking environments.
6. Network Protocols
6.1 TCP/IP Model
The Transmission Control Protocol/Internet Protocol (TCP/IP) model is the foundational network protocol suite that underpins the Internet and facilitates computer network communication. Developed in the 1970s, the TCP/IP model consists of four layers, each serving a specific role:
- Link Layer (Network Interface Layer): This layer handles the physical and logical connections to the network media by working with various networking hardware and specifies how data should be sent physically through the network.
- Internet Layer (IP Layer): This layer is responsible for addressing, packaging, and routing functions. The core protocol of this layer, the Internet Protocol (IP), routes packets across networks.
- Transport Layer: TCP and UDP are the main protocols of this layer. TCP provides reliable, ordered, and error-checked delivery of data between applications running on hosts communicating over an IP network. UDP provides simpler, connectionless communication services for applications that do not require TCP’s sequencing and error checking.
- Application Layer: This layer includes protocols used by applications to communicate over the network. Protocols at this level provide data exchange for applications.
Each layer of the TCP/IP model provides a specific functionality and interacts with the layers directly above and below it to perform complex networking tasks, simplifying the network design and ensuring robust, scalable communication.
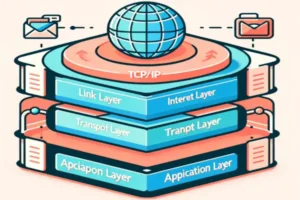
6.2 Application Layer Protocols
Application layer protocols specify how software applications should communicate over a network. They operate at the highest level of the TCP/IP model, providing protocol mechanisms that directly support user applications and services. Key application layer protocols include:
- HTTP (Hypertext Transfer Protocol): The foundation of data communication for the World Wide Web.
- FTP (File Transfer Protocol): Used for transferring files between a client and a server on a network.
- SMTP (Simple Mail Transfer Protocol): A protocol for sending email messages between servers.
- DNS (Domain Name System): Resolves domain names to IP addresses so browsers can load internet resources.
These protocols ensure that applications on different computing devices can communicate and exchange data over a network, thereby providing a smooth and reliable user experience.
7. Network Security
7.1 Threats and Vulnerabilities
Network security is crucial to protect data during its transmission and ensure that networks are reliable and trustworthy. Common threats and vulnerabilities include:
- Malware (Malicious Software): Includes viruses, worms, and Trojan horses that can perform unauthorized actions on the network.
- Phishing Attacks: Attempts to steal sensitive information like usernames, passwords, and credit card details by pretending to be a trustworthy entity.
- Denial of Service (DoS) Attacks: Intended to shut down a network, making it inaccessible to its intended users.
- Man-in-the-Middle (MitM) Attacks: Where the attacker secretly intercepts and possibly alters the communication between two parties who believe they are directly communicating with each other.

7.2 Security Measures and Best Practices
To protect against these threats, several best practices and security measures should be implemented:
- Use of Firewalls: Firewalls can be hardware or software-based and are used to block unauthorized access to network resources.
- Encryption: Encrypting data transmitted across networks to prevent unauthorized access.
- Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS): These systems monitor network traffic for suspicious activity and block potentially harmful traffic.
- Regular Updates and Patch Management: Keeping software and hardware up to date to protect against vulnerabilities.
- Security Policies and Training: Developing comprehensive security policies and training employees in security protocols to mitigate human error.
Implementing these measures will greatly enhance the security of a network, protect against potential threats, and ensure the safe and secure handling of data across networks.
8. Emerging Network Technologies
8.1 IoT and Edge Computing
The Internet of Things (IoT) and edge computing are two technologies redefining how data is processed and managed across networks:
- Internet of Things (IoT): IoT refers to the network of interconnected devices that communicate and exchange data without human intervention. These devices range from simple sensors and home appliances to sophisticated industrial tools. IoT’s rise is supported by advancements in sensor technology, cloud computing, and broadband connectivity, enabling devices to be smarter and more responsive.
- Edge Computing: As a complement to cloud computing, edge computing involves processing data near the edge of the network, where the data is generated, rather than relying on a central data center. This proximity reduces latency, saves bandwidth, and improves response times, making it ideal for time-sensitive data processing in applications such as autonomous vehicles, smart cities, and real-time data analytics.
These technologies are rapidly evolving to support smarter ecosystems and more responsive, decentralized networks.
8.2 Future Trends in Networking
Looking ahead, several key trends are poised to shape the future of networking:
- 5G Technology: The rollout of 5G networks will dramatically increase the speed and responsiveness of wireless networks, enabling more IoT applications and making real-time data processing more efficient.
- Artificial Intelligence and Machine Learning: AI and ML are being integrated into network management to predict network anomalies, enhance security, and optimize traffic flow without human intervention.
- Blockchain: Although primarily known for cryptocurrency, blockchain offers a secure way to record transactions and manage data across a distributed network, potentially revolutionizing how data is tracked and secured across networks.
These trends highlight the dynamic nature of networking technology and its continuous evolution towards more automated, secure, and efficient systems.
9. Case Studies and Practical Applications
9.1 Real-world Networking Examples
One notable case study in networking is the deployment of a multinational corporation’s global network. This involved integrating thousands of devices across multiple locations worldwide, using a combination of WAN technologies and internet-based VPNs to create a cohesive, secure network. The implementation utilized advanced routing protocols like BGP to manage the data flow efficiently and MPLS for prioritizing voice and video traffic, which was critical for maintaining effective communication channels.
The network also included redundant pathways and automatic failover systems to ensure continuous service availability and data integrity. The deployment showcased the importance of strategic planning, rigorous testing, and the need for scalable solutions that can adapt to growing business demands.
9.2 Lessons Learned
From this case study, several key lessons emerged:
- The Importance of Redundancy: Redundancy is crucial for maintaining network reliability, especially in complex, geographically dispersed networks.
- Scalability is Key: Networks must be designed with scalability in mind to accommodate future growth and technology integration without requiring complete overhauls.
- Security Cannot Be Overlooked: As networks expand, they become more vulnerable to attacks, making robust security measures fundamental from the outset.
10. References
Books and Articles
- “Computer Networks” by Andrew S. Tanenbaum provides a detailed overview of the theoretical and practical aspects of computer networks.
- “Networking for Dummies” by Doug Lowe offers a more accessible entry point for beginners (2016 version).
- “The Road to IP Telephony” by Stephanie Carhee provides insights into real-world IT deployment strategies.
Relevant RFCs