Ring topology is a type of network topology in which each computer or device is connected to exactly two other devices, forming a continuous loop.
This comprehensive guide aims to provide you with a robust understanding of ring topology, focusing on key distinctions such as single versus dual rings. We’ll delve into scenarios where circular configuration shines or falls short and introduce you to important protocols like Token Ring and FDDI. Our FAQ section will answer common questions to ensure you have a holistic understanding of the subject.
Jump to:
- What is Ring Topology?
- Key Features
- Types of Ring Topology
- Advantages and Disadvantages
- Components Involved
- Protocols Commonly Used
- Real-world Applications
- Key Challenges
- FAQ Section
- Conclusion
- References
What is Ring Topology?
Ring topology is a networking configuration where each node or device is connected to exactly two other nodes, forming a continuous closed loop. This topology is chiefly characterized by the absence of a central hub, making it distinct from other topologies like star and tree. Instead, the devices are connected in a circular fashion, and data packets travel through this circle to reach their destination.
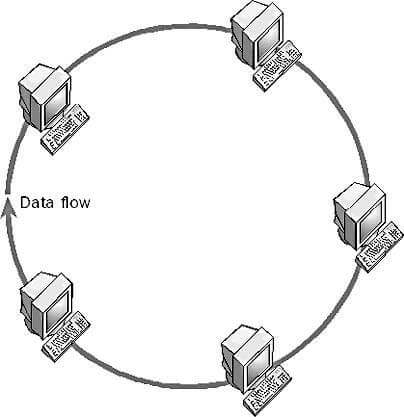
The ring topology is commonly used in the following kinds of networks:
- Token ring networks: The ring of a token ring network is concentrated inside a device called a Multistation Access Unit (MAU).
- Fiber Distributed Data Interface (FDDI) networks: The ring in this case is both a physical and logical ring and usually runs around a campus or collection of buildings to form a high-speed backbone network.
2. Key Features
Point-to-Point Connection
In a ring topology, each node is connected in a point-to-point manner with its two adjacent nodes. This means that every device has a direct connection with only the devices immediately preceding and succeeding it in the network loop. This point-to-point connection forms the backbone of this topology and is responsible for its unique characteristics.
Data Transmission
In a basic ring topology, data typically moves in a unidirectional fashion, making a loop until it reaches its destination. However, it can also be configured for bidirectional data flow in some variations like a dual ring. Packets or “tokens” are sent through the network, passing through each node where they are either captured or forwarded until they reach their destination node.
Closed Loop
One of the defining features of this topology is its closed-loop structure. Unlike bus topology, which has distinct endpoints, the ring topology forms a closed circuit. This loop ensures a predictable path for data packets, but it also means that if one point in the network fails, it could potentially disrupt the entire system.
3. Types of Ring Topology
Single Ring
In a single-ring topology, all the nodes are connected in a closed loop, and data travels in a single direction. This is the simplest form of ring topology and is easy to set up. The primary advantage here is predictability; data moves in one direction, so it’s easy to trace and manage. However, if one node fails, the entire network gets disrupted because the loop is broken.
Dual Ring
A dual-ring topology is essentially two-ring networks built on top of each other. In this setup, data can travel in both clockwise and counterclockwise directions. This offers redundancy and increased fault tolerance. If one ring fails, the data can travel in the opposite direction on the other ring, ensuring that network communication remains uninterrupted. However, dual-ring topologies are more complex to manage and set up than single rings.
In summary, the type of ring topology you choose—be it single or dual—depends on your specific needs, such as the level of fault tolerance required, simplicity, or data transmission speed.
4. Advantages and Disadvantages
Pros
- Simplicity: Ring topology is relatively easy to install and configure, especially in its single-ring form.
- Predictable Routing: The closed-loop structure means that data packets have a predictable path to follow, making it easier to manage the network.
- Efficient Use of Resources: In smaller setups, ring topology can be cost-effective and require fewer resources than other topologies like mesh and star.
Cons
- Single Point of Failure: In a single-ring topology, the failure of a single node can disrupt the entire network, making it less reliable compared to other topologies.
- Limited Scalability: Adding or removing nodes often requires network downtime, and as more nodes are added, performance can degrade.
- Data Collision: In single-ring topologies, data collision can occur if multiple nodes send data simultaneously, although this is mitigated in protocols like Token Ring.
Scenarios Where It’s Advantageous or Disadvantageous
- Advantageous: Ring topology can be advantageous in smaller networks where simplicity and minimal resource usage are more important than scalability and fault tolerance.
- Disadvantageous: For larger networks, or those requiring high levels of reliability and fault tolerance, other topologies like mesh or star are often more suitable.
5. Components Involved in Ring Topology
Nodes
In ring topology, the term “nodes” refers to the computers, servers, or other network devices that are connected in the ring. Each node has a unique address and is capable of sending and receiving data packets.
Network Cable
The network cables used in this topology can vary depending on the specific requirements and may include coaxial cables, fiber-optic cables, or standard Ethernet cables. The choice of cable often depends on the data transmission speed requirements and the environment in which the network is set up.
Hub/Switch
While not strictly necessary in a basic ring topology, a hub or switch can be added to increase network efficiency. In the case of a dual ring, switches can manage the flow of data between the two rings.
Network Interface Cards (NICs)
Network Interface Cards are critical for facilitating the connection between the nodes and the network cables. Each node in this topology needs to have a NIC installed to connect to the network.
6. Protocols Commonly Used
Token Ring Protocol
Developed by IBM, the Token Ring protocol is specially designed for ring topology. In this protocol, a “token” circulates around the network, granting permission to the node holding the token to send data. This effectively reduces data collisions and makes the network more predictable. Token Ring used to be quite popular but has largely been replaced by Ethernet due to speed limitations and higher costs.
Fiber Distributed Data Interface (FDDI)
FDDI is a standard for transmitting data in local area networks (LANs) that can extend in range up to 200 kilometers. Although it’s often implemented in a dual-ring topology, it can also be used in single-ring configurations. FDDI uses fiber-optic cables, providing higher bandwidth and supporting the transmission of data at speeds of up to 100 Mbps.
Synchronous Optical Network (SONET)
SONET is mainly used in high-speed, long-distance networks. While not strictly limited to ring topology, it is commonly implemented in ring configurations, particularly dual-ring topologies, to provide network redundancy. SONET rings can operate at speeds ranging from 51.84 Mbps to several gigabits per second, making them suitable for heavy-duty applications like internet backbones.
7. Real-world Applications
Office Buildings
In smaller office settings, a simple ring topology can be an efficient way to connect a limited number of devices. It offers a straightforward, easy-to-manage networking solution where high-speed data transmission and fault tolerance are not critical.
Small Campus Networks
Educational and research campuses with smaller user bases can benefit from this topology for connecting multiple buildings or departments. Here, the topology can offer a cost-effective solution with easier management protocols compared to more complex configurations.
Metro Ring Networks
In Metropolitan Area Networks (MANs), dual-ring topology is commonly used to connect different locations across a city. These setups often employ high-speed protocols like SONET and use fiber-optic cables to ensure fast, reliable data transmission across longer distances.
8. Key Challenges
Maintenance
Ring topology, particularly in its dual-ring form, can be challenging to maintain. Even though dual rings offer redundancy, the complexity of managing two interlinked loops can lead to difficulties in troubleshooting and repairs. Moreover, in a single ring, the failure of one node or connection can take down the entire network, requiring immediate maintenance.
Cost
While a single-ring topology can be cost-effective for small setups, the costs can quickly escalate when scaling. Adding more nodes or transitioning to a dual-ring configuration will not only require additional hardware but may also necessitate network downtime, contributing to indirect costs.
Technology Evolution
As technology evolves, many networks are transitioning to more scalable and reliable topologies like mesh and star. While protocols used are robust, they are often not as fast or efficient as newer technologies, requiring additional investment to keep the network up-to-date.
9. FAQ Section
Q: Is Ring Topology still in use today?
A: While less common than other topologies like star and mesh, ring topology is still used in specific scenarios that require its unique features.
Q: What happens when a single node fails in a ring topology?
A: In a single ring, the failure of just one node or a break in the cable can disrupt the entire network. This is because data packets can’t complete their loop, causing a breakdown in communication until the issue is resolved.
Q: Can ring topology be set up using wireless technology?
A: While traditionally implemented using wired connections, ring topologies can also be configured wirelessly, although this is less common.
Q: What’s the primary advantage of using dual-ring topology over single-ring?
A: Dual-ring topology offers greater fault tolerance. If one ring fails, the second ring can still function, keeping the network operational.
Q: How is a dual-ring topology different from a single-ring topology?
A: In a dual-ring, there are two rings: one for data to flow in a clockwise direction and another for data to flow counterclockwise. This provides redundancy; if one ring fails, the other can still function, maintaining network communication.
Q: Name a real-world application where ring topology is commonly used.
A: This topology is often used in Metropolitan Area Networks (MANs) to connect different locations across a city. These setups frequently use high-speed protocols like SONET and fiber-optic cables for reliable data transmission over longer distances.
10. Conclusion
Ring topology is a fascinating and nuanced network configuration with its unique set of advantages, disadvantages, and challenges. Its two primary types, single-ring and dual-ring, offer different levels of complexity and reliability. Understanding the protocols involved, like Token Ring, FDDI, and SONET, can give you an in-depth perspective on how and why these networks function as they do.
While this topology may not be as commonly deployed as other configurations like star or mesh, it still has applications in various real-world scenarios, from small office settings to metropolitan networks. However, it comes with its own set of challenges in terms of maintenance, cost, and keeping up with evolving technology.
By now, you should have a well-rounded understanding of this topology that should serve you well in both exam preparation and in the field. Remember, the right topology depends on the specific needs of the network you’re dealing with, so always consider the trade-offs involved.
Thank you for joining us in this comprehensive guide on ring topology. We hope it has been informative and beneficial for your understanding of network configurations.
11. References
Books:
- “Computer Networks” by Andrew S. Tanenbaum and David J. Wetherall
- “Network Warrior” by Gary A. Donahue
Network Encyclopedia Articles:
- What is Bus Topology?
- Learn Mesh Topology
- Star Bus Topology Comprehensive Guide
- Star Topology Basics
Request For Comments: