In the world of computer security, particularly within Microsoft Windows systems, an Access Token is a vital component, functioning as a digital key to the kingdom. Generated during a successful logon by the security subsystem, this object is a critical element in the authentication and authorization processes. Attached by the Winlogon process to all user processes, it determines what resources a user can access and what operations they can perform.
This article will delve into the nuances of Access Tokens in Windows systems, exploring their structure, creation, and role in maintaining system security. Additionally, we’ll broaden our scope to understand other interpretations of “access token” in the realm of computer networking, including their use in web applications and APIs, offering a comprehensive view of this multifaceted concept.
Table of Contents:
- Access Tokens in Windows Systems
- Components of a Windows Access Token
- Access Tokens in Action: Security and Permissions
- Broader Context: Access Tokens in Computer Networking
- Access Tokens in Web Technologies
- Conclusion
- References

1. Access Tokens in Windows Systems
Definition and Importance in User Authentication and Authorization
In Microsoft Windows systems, an Access Token is an essential security object created during user logon. It embodies the cornerstone of the security model, playing a pivotal role in both authentication and authorization processes. Authentication verifies a user’s identity, while authorization determines their access rights. The Access Token serves as a digital identity card, containing crucial information about the user, including their security credentials and privileges.
How Access Tokens are Generated and Attached to User Processes
- Generation: The process begins with a successful user logon. The Windows security subsystem authenticates the user’s credentials and, upon verification, generates an Access Token.
- Attachment to Processes: This token is then attached to the Winlogon process and subsequently to every process initiated by the user. The token travels with each process as an integral part of the security context, informing the system about the user’s rights and privileges.
- Role in System Security: As the user interacts with the system, the Access Token is consulted to ensure that access to resources and operations is granted only if permitted by the token. This mechanism is fundamental to maintaining the integrity and security of the Windows operating system.
How it works
An access token is like a card key. Your card key will provide you with access to doors that have been configured to grant you permission to open them. The list of card keys that a door will accept is analogous to an access control list (ACL).
Access token -> Access Control List
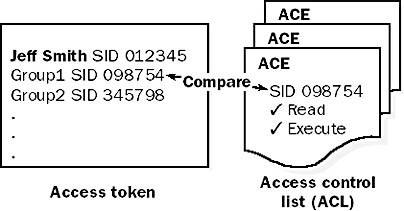
When you successfully log on to Windows, you are granted an access token, which is attached to all your user processes. Your access token contains the security identifier (SID) of your user account and every group to which you belong.
When your application tries to access an object such as a file on a volume formatted with the NTFS file system, Windows OS compares the SIDs in your application’s access token to those in the access control entries (ACEs) in the object’s ACL. If it finds a match, the system grants access to that object.
2. Components of a Windows Access Token
Detailed Breakdown of an Access Token’s Structure
A Windows Access Token is composed of several critical elements, each contributing to the security decision-making process:
- User and Group Security Identifiers (SIDs): The token includes the SID of the user account and SIDs of the groups the user is a member of. These SIDs are central to identifying the user and their group memberships within the system.
- Privileges: These are specific rights assigned to the user or groups. Privileges can include actions like shutting down the system, loading device drivers, or managing system files.
- Other Attributes: Additional attributes in the token may include the logon SID, which is unique to each logon session, and any user-specific data.
Explanation of How These Components Influence User Access
- Determining Access Rights: When a process requests access to a resource, the system checks the Access Token against the resource’s security descriptor. It determines whether the user’s SIDs and privileges allow the requested operation.
- Enforcing Security Policies: The Access Token acts as a gatekeeper, enforcing the security policies defined by the system or network administrators. It ensures that users can only perform actions allowed by their assigned privileges and group memberships.
- Dynamic Access Control: In more advanced scenarios, attributes in the Access Token can interact with dynamic access control policies, further refining access decisions based on current context and user attributes.
3. Access Tokens in Action: Security and Permissions
How Windows Uses Access Tokens to Grant or Deny Access to Resources
Windows leverages Access Tokens as a key mechanism to manage access rights within the system:
- Access Decision Process: When a user or a process attempts to access a resource, such as a file or a directory, the system evaluates the Access Token. It checks the user’s or group’s SIDs and privileges against the resource’s security descriptor, which contains information about who is allowed or denied access.
- Enforcing Security Policies: The Access Token effectively enforces security policies set by administrators. If the Token’s credentials match the permissions of the resource, access is granted; otherwise, it is denied.
- Dynamic Assessment: This process is dynamic and occurs each time a resource is accessed, ensuring that current permissions are always applied based on the user’s current context and security profile.
Real-World Scenarios Illustrating the Use of Access Tokens in Security
- Secure File Access: In a corporate environment, an employee attempts to access confidential files. The system checks the employee’s Access Token against the file’s security settings and grants access only if the employee has the necessary permissions.
- Application Restrictions: An application tries to perform a system-level operation, such as modifying the registry. Windows checks the Access Token of the process running the application to determine if it has the required privileges, ensuring that only authorized changes are made.
4. Broader Context: Access Tokens in Computer Networking
Definition and Use of Access Tokens in Web Applications and APIs
In the broader landscape of computer networking, especially in web applications and APIs, the term “Access Token” takes on a different meaning:
- Bearer Tokens: In web services and applications, Access Tokens are often bearer tokens used in authentication and authorization protocols like OAuth. These tokens represent the user’s credentials and permissions for accessing specific resources on a web server or API.
- API Authentication: When a user logs into a web application or authenticates through an API, an Access Token is generated and provided to the client. This token is then used in subsequent requests to access protected resources or services.
Comparison with Windows Access Tokens
- Scope and Usage: While Windows Access Tokens are used internally within the operating system to manage access to system resources, Access Tokens in web technologies are used for securing access to web-based services and APIs.
- Lifecycle and Management: Web-based Access Tokens typically have a limited lifespan and are managed through different protocols (like OAuth), whereas Windows Access Tokens exist for the duration of a user’s session.
- Security Context: Access Tokens in web applications often require additional security considerations, such as token encryption and secure transmission, compared to the more controlled environment of Windows Access Tokens.
5. Access Tokens in Web Technologies
Detailed Examination of Access Tokens in OAuth, OpenID Connect, and Other Authentication Protocols
In the context of web technologies, Access Tokens are pivotal in authentication and authorization protocols:
- OAuth and OAuth 2.0: OAuth is an open standard for access delegation, commonly used to grant websites or applications access to information on other websites without giving them passwords. In OAuth 2.0, Access Tokens are issued by an authorization server and are used by the client application to access protected resources hosted by a resource server.
- OpenID Connect: Building on top of OAuth 2.0, OpenID Connect is an identity layer that provides a way to verify a user’s identity. The Access Token in OpenID Connect is used alongside an ID Token, which provides the client with details about the authenticated user.
These protocols utilize Access Tokens to manage user permissions and secure API requests, ensuring that only authenticated and authorized users can access specific resources or services.
Their Role in Securing Web Applications and Services
- User Authentication and Service Authorization: Access Tokens enable web applications and services to authenticate users and authorize services without exposing user credentials. This method enhances security by limiting the spread and use of sensitive information.
- Resource Access Control: The tokens act as a control mechanism for accessing resources on web servers, ensuring that each request is accompanied by the correct credentials for the requested resources.
- Token Security Measures: Security measures, such as token encryption and the use of HTTPS, are vital to protect tokens from interception and unauthorized use.
6. Conclusion
Access Tokens, whether in Windows systems or web technologies, serve as a cornerstone in the realm of digital security. In Windows, they are integral to the system’s security architecture, dictating access rights and permissions for users and processes. In web technologies, Access Tokens play a critical role in OAuth, OpenID Connect, and similar protocols, securing web applications and services by managing user authentication and resource authorization.
The evolution and application of Access Tokens across different platforms highlight their versatility and essential role in maintaining robust security in both local and network environments. Understanding their function and application is crucial for anyone involved in cybersecurity and network administration.
7. References
- “Windows Internals, Part 1” by Mark Russinovich and David Solomon – for understanding Windows Access Tokens.
- RFC 6749: The OAuth 2.0 Authorization Framework – provides technical details on OAuth 2.0 protocols.
- “OAuth 2.0 Simplified” by Aaron Parecki – a guide to OAuth 2.0 protocols.
- OpenID Connect Core 1.0 – a public specification defining OpenID Connect.
- “Identity and Data Security for Web Development” by Jonathan LeBlanc and Tim Messerschmidt – covers security in web applications, including Access Tokens.
- Microsoft’s Official Documentation on Access Tokens – for insights into Windows Access Tokens.