Acknowledgment, commonly known as ACK, is a fundamental concept in computer networking, pivotal for ensuring error-free data transmission. It serves as a signal from the receiving station to the transmitting station, confirming the successful receipt of data.
This mechanism plays a crucial role in maintaining the reliability and efficiency of network communication. In this article, we delve into the nuances of ACK, exploring its workings, importance, and applications in the realm of computer networking. Whether you’re a student, a professional, or a curious enthusiast, this comprehensive guide aims to enhance your understanding of ACK and its critical function in network communication.
In this article:
- What is ACK?
- How ACK Works
- The Importance of ACK in Network Reliability
- Advanced Concepts: Variations and Extensions of ACK
- Troubleshooting and Common Issues
- References

1. What is ACK?
Acknowledgment, abbreviated as ACK, is a crucial concept in computer networking, serving as a cornerstone for reliable data transmission. At its core, ACK is a signal sent from a receiver to a transmitter, indicating the successful reception of data packets. This feedback mechanism is fundamental in networks, especially in protocols where data integrity and error-free transmission are paramount.
ACK operates under a simple yet effective principle. When a device sends data across a network, it waits for an acknowledgment from the receiving device. This acknowledgment confirms that the data has arrived intact and without errors. If the sender doesn’t receive an ACK within a specified time frame, it assumes the data was lost or corrupted in transit and resends the packets. This process not only ensures data integrity but also optimizes network performance by avoiding unnecessary data retransmissions.
NAK (negative acknowledgment)
On the other hand, if the receiving station determines that the data transmission is late or has not arrived, a NAK (negative acknowledgment) is generated to indicate to the transmitting station that the data should be sent again.
The Role of ACK in Networking Protocols
In the realm of networking protocols, ACK plays a diverse and significant role. It’s most prominently featured in the Transmission Control Protocol (TCP), where it is integral to the protocol’s ability to provide reliable, ordered, and error-checked delivery of a stream of bytes between applications running on hosts communicating over an IP network.
TCP uses a sequence number to keep track of packets. When a packet is received, the receiver sends back an ACK with the next expected sequence number. This confirms the successful receipt of the packet and informs the sender of the next packet it should send. This method is not only efficient but also allows for the reordering of packets that might arrive out of sequence, further enhancing the reliability of the transmission.
In addition to TCP, ACK is used in various other protocols, each adapting the concept to fit specific requirements and environments. For instance, in wireless networking protocols, ACKs are critical for coping with the inherently unstable nature of wireless communication.
The Transmission Control Protocol (TCP) is a connection-oriented protocol that relies on acknowledgments for successful transmission of data. When a stream of TCP packets is being sent over the network, each packet contains an acknowledgment number indicating the sequence number of the next packet that the receiving station should expect to receive.
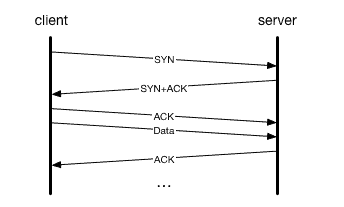
TCP can use an ACK to acknowledge a series of TCP packets that have been received, rather than just a single packet. A TCP packet sent as an acknowledgment has its ACK flag set to 1 to indicate that the acknowledgment numbers of the packets received are valid.
2. How ACK Works
The ACK Mechanism in TCP/IP
In TCP/IP, the most widely used suite of communication protocols, ACK works hand-in-hand with the TCP to ensure reliable data transfer. The mechanism is sophisticated yet operates on a basic principle. When a packet is sent from one device to another over a TCP/IP network, the sender keeps a copy of the packet until it receives an acknowledgment from the receiver. This process is part of what is known as the TCP three-way handshake, which establishes a reliable connection between the sender and receiver before the actual data transmission begins.
During data transmission, each TCP packet includes a sequence number. This number is crucial as it helps the receiving device to assemble the packets in the correct order and to identify any missing packets. Once the packet is successfully received and ordered, the receiver sends back an ACK packet. This packet doesn’t contain any data; instead, it includes the sequence number of the next expected packet. This sequence number acts as confirmation that all previous packets have been received correctly.
Examples of ACK in Action
Consider a scenario where a computer (Computer A) is sending a large file to another computer (Computer B) over a TCP/IP network. The file is divided into multiple packets for transmission. As each packet reaches Computer B, it sends an ACK back to Computer A, indicating the successful receipt and the sequence number of the next expected packet.
If a packet is lost or arrives with errors, Computer B’s response will indicate the last successfully received packet. Computer A, upon not receiving the expected ACK, will retransmit the missing packet. This mechanism ensures that even in the case of packet loss or errors, the integrity of the data transfer is maintained, and the file reaches Computer B intact.
This ACK process is not just limited to file transfers but is a fundamental part of any data exchange in TCP/IP networks, playing a vital role in web browsing, email communication, and more, ensuring that the vast and varied landscape of internet communication remains reliable and efficient.
3. The Importance of ACK in Network Reliability
Error Detection and Correction
Acknowledgment (ACK) plays a pivotal role in error detection and correction within network communication. This function is integral to maintaining data integrity, a key aspect of network reliability. When data packets are sent over a network, they can encounter various issues like packet loss, duplication, or errors due to network congestion, interference, or faulty hardware.
ACK serves as a vital tool in identifying these issues. By awaiting a confirmation for each packet sent, the sender can detect when a packet has not been received or has been received with errors. In the absence of an ACK, or if an incorrect ACK is received, the sender knows to retransmit the packet. This process ensures that all data reaches its destination correctly and in its entirety.
Moreover, the acknowledgment mechanism allows for error correction. When a packet is identified as lost or erroneous, the mechanism of retransmission corrects these errors, ensuring the data is eventually delivered correctly. This continuous check-and-balance approach is crucial for network reliability, especially in applications where data integrity is non-negotiable.
Impact on Data Transmission Efficiency
The efficiency of data transmission in a network heavily relies on the effectiveness of the ACK system. Efficient ACK mechanisms reduce the need for retransmission, saving bandwidth and reducing network congestion. A well-implemented ACK system ensures that only necessary retransmissions occur, which is vital for optimizing network performance, particularly in high-traffic environments.
By confirming the receipt of packets and enabling the sender to adjust its transmission rate accordingly, ACK also plays a role in flow control. This aspect of ACK helps prevent network overload by ensuring that a sender does not overwhelm a receiver with too much data at once. As a result, the network maintains a balanced load, leading to more efficient data transmission and overall network performance.
4. Advanced Concepts: Variations and Extensions of ACK
Selective ACK and Cumulative ACK
The evolution of network technology has led to advanced variations of the basic ACK mechanism, such as Selective Acknowledgment (SACK) and Cumulative Acknowledgment. Selective ACK is an enhancement over the traditional ACK approach. Instead of sequentially acknowledging the receipt of all packets, SACK allows the receiver to acknowledge non-contiguous blocks of packets. This means that if packets arrive out of order, the receiver can inform the sender which specific packets have been received, reducing unnecessary retransmissions and improving network efficiency.
Cumulative ACK, on the other hand, is a simpler form where the receiver only sends an acknowledgment for the highest in-order packet it has received. This means if packets 1, 2, 4, and 5 are received, but packet 3 is missing, the receiver will send an ACK for packet 2. Cumulative ACK is simpler but less efficient in scenarios with high packet loss.
ACK in Wireless and Mobile Networks
In wireless and mobile networks, the role of ACK adapts to the unique challenges posed by these environments, such as higher rates of packet loss and variable connection quality. In such networks, the ACK mechanism is often more robust to cater to frequent changes in network conditions.
For instance, in mobile networks, the ACK mechanism might include additional features like fast retransmit and dynamic adjustment of retransmission timers to cater to the higher probability of packet loss and variable latency. These enhancements ensure that the ACK system remains effective even in the less predictable and more error-prone wireless environment.
Furthermore, in protocols like LTE (Long-Term Evolution), ACK plays a critical role in ensuring the reliability of high-speed data transmission. The mechanism is optimized to handle high volumes of data with minimal delay, adapting to the fast-paced and mobile nature of the network. The evolution of ACK in these environments showcases its versatility and essential role in the diverse landscape of modern networking.
5. Troubleshooting and Common Issues
Identifying ACK-related Problems in Networks
Troubleshooting in networking often involves identifying and resolving ACK-related issues, which can significantly impact network performance. Common indicators of ACK problems include slow data transfer rates, frequent timeouts, and data loss. To diagnose these issues, network administrators often rely on tools like packet analyzers and network diagnostics software.
Packet analyzers can be particularly effective, as they allow administrators to see the sequence of packets sent and received, along with their ACKs. By analyzing this data, one can identify patterns such as missing ACKs or delayed acknowledgments, which are indicative of network problems. Additionally, monitoring network traffic for retransmissions can help in pinpointing areas where data packets are consistently failing to be acknowledged.
Solutions and Best Practices
Once ACK-related problems are identified, the next step is to implement solutions. These can vary based on the specific issue but often involve optimizing network settings or addressing hardware-related problems. For instance, adjusting the TCP window size can help in cases where the rate of ACKs is affecting data throughput. In scenarios involving packet loss, improving the physical network infrastructure, like upgrading cables or network interfaces, can be effective.
Best practices in preventing ACK-related issues include regular network monitoring, maintaining up-to-date firmware and software, and ensuring that network devices are properly configured. Implementing robust error-handling and retransmission strategies in network protocols also goes a long way in mitigating the impact of ACK-related problems.
6. References
- Books:
- “TCP/IP Illustrated, Volume 1: The Protocols” by W. Richard Stevens
- “Computer Networking: A Top-Down Approach” by James F. Kurose and Keith W. Ross
- Research Papers:
- “Enhancing TCP Performance in Wireless Networks” by Hari Balakrishnan et al.
- “A Comparative Study of Error Control Techniques for Wireless Communication” by S. Lin, D. J. Costello, and M. J. Miller
- RFCs: