In a digital age where cybersecurity threats loom large, ensuring the integrity and origin of software becomes paramount. Microsoft’s Authenticode technology serves this very purpose. It authenticates the identity of the software publisher and verifies the code integrity to safeguard against unauthorized modifications. This article aims to dissect Authenticode from its conceptual framework to its operational nuances. By the end of this guide, you’ll gain an in-depth understanding of why Authenticode is a cornerstone in software security.
In this article:
- What is Authenticode?
- How Does Authenticode Work?
- Types of Certificates Used in Authenticode
- Benefits of Using Authenticode
- Limitations and Drawbacks
- Authenticode in Action: Use Cases
- Setting Up Authenticode for Your Software
- Best Practices in Managing Authenticode
- Future of Authenticode
- Conclusion
- Additional Resources
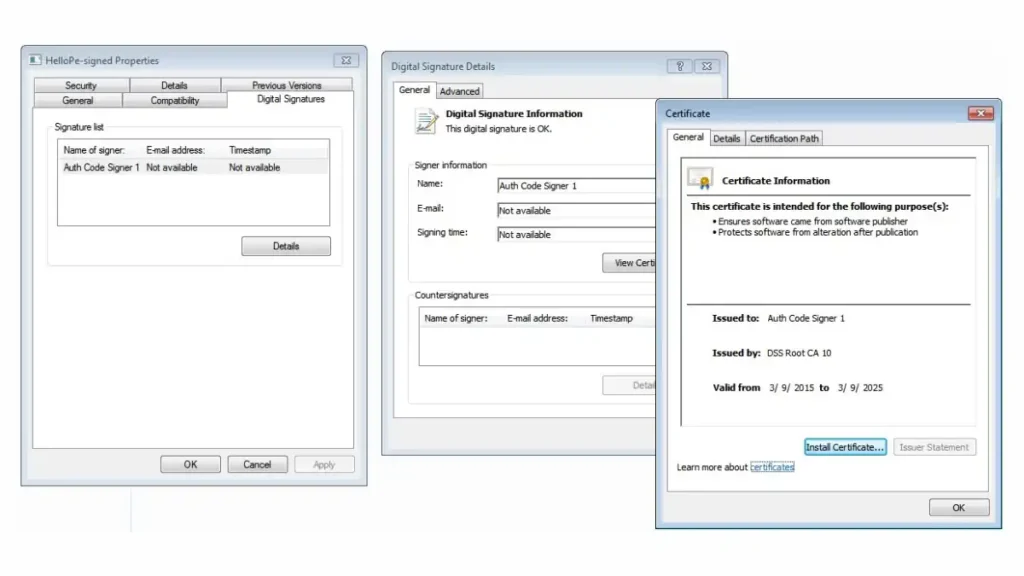
1. What is Authenticode?
Definition and Origins
Authenticode is a Microsoft technology designed to authenticate the source and confirm the integrity of software programs. Developed in the late 1990s, this technology leverages digital signatures to assure end-users that the software they are installing or running is legitimate and unaltered since its creation. The term “Authenticode” is derived from “Authentication” and “Code,” pointing directly to its fundamental purpose—authenticating the code you interact with.
The Necessity for Authenticode in Modern Computing
In today’s digital age, the risks tied to software distribution are sky-high. Phishing scams, malware, and code injections are just the tip of the iceberg. When you download or install a program, you want to be certain that it hasn’t been tampered with and that it originates from a trusted source. Herein lies the necessity for Authenticode.
In fact, Authenticode isn’t merely a fancy add-on; it’s a cornerstone of secure software distribution. It acts as a gatekeeper, only permitting software with a valid digital signature to pass through. This screening process becomes even more crucial in enterprise settings, where a single malicious software can compromise an entire network.
Core Components
Authenticode operates using a range of core components, each serving a critical function in the authentication and verification process. Below are the key elements:
» Digital Signature
This is the cryptographically secure stamp of approval. It is affixed to the software by the publisher, acting as evidence that the software has not been altered after signing.
» Certificate Authority (CA)
The role of the CA is to issue digital certificates that validate the identity of the certificate holder and provide the public key to establish secure communications.
» Public and Private Keys
In the context of Authenticode, a private key is used by the software publisher to create a digital signature. On the other hand, the public key is used by end-users to verify this signature.
» Timestamping
This provides a digital record of the exact time the software was signed, enabling users to ascertain that the signature was applied during the validity period of the certificate, even if the certificate has since expired.
Authenticode, thus, unites these components to create an ecosystem where both publishers and users can operate with enhanced trust and security. Its intricate architecture is geared towards not just validating the identity of the software publishers, but also ensuring the code you run is exactly as it was when first signed.
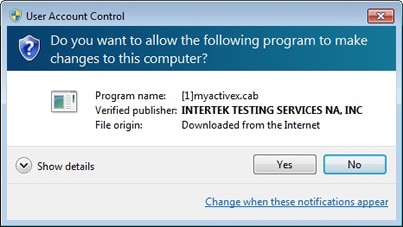
In sum, Authenticode serves as an essential security layer, creating a trusted bridge between software publishers and end-users. It not only verifies who you’re getting the software from but also assures you that what you’re getting is genuine.
2. How Does Authenticode Work?
Understanding how Authenticode functions is vital for anyone involved in software development, distribution, or simply running applications on their systems. Let’s peel back the layers to see how it all comes together.
The Signing Process
Code signing is the heartbeat of Authenticode. After developing an application or a piece of software, the publisher uses their private key to digitally sign the code. Here’s a simplified step-by-step guide on how it works:
- Hash Generation: Firstly, a cryptographic hash of the original software code is generated. This hash serves as a unique identifier.
- Private Key Signing: The generated hash is then signed using the publisher’s private key.
- Certificate Attachment: Finally, the signed hash and the digital certificate from the CA (Certificate Authority) are bundled with the original software code.
At the end of this process, we have software that carries a digital signature, a timestamp, and a certificate, validating its origin and integrity.
Certificate Authorities (CAs)
In the world of Authenticode, Certificate Authorities play the role of trusted middlemen. CAs are responsible for verifying the identity of the software publisher before issuing a digital certificate. This certificate, once attached to the software, acts as a guarantee that the publisher is who they claim to be.
CAs operate under stringent guidelines, ensuring that their issued certificates meet rigorous security standards. Furthermore, their involvement adds a layer of trust and reliability to the entire process.
Public and Private Keys
A pair of cryptographic keys is used in the signing and verification process:
- Private Key: Known only to the software publisher, this key is used to create the digital signature during the signing process.
- Public Key: This key is available to anyone wanting to verify the authenticity of the digital signature. It is often distributed as part of the digital certificate.
The two keys are mathematically linked; what one key encrypts, only the other can decrypt. The private key remains confidential, while the public key is disseminated widely.
The Verification Process
When a user attempts to download or run the signed software, the Authenticode technology kicks in to verify the digital signature. Here’s how:
- Extract Signature: The technology first extracts the digital signature attached to the software.
- Public Key Decryption: The signature is decrypted using the public key, revealing the original hash.
- New Hash Generation: A new cryptographic hash of the downloaded software code is generated.
- Hash Comparison: Finally, the decrypted original hash and the newly generated hash are compared. If they match, it confirms the code has not been altered.
Validation Steps
Validation goes beyond just checking the integrity of the software. Additional checks include:
- Certificate Validation: Authenticode ensures the accompanying digital certificate is legitimate and is issued by a trusted CA.
- Timestamp Verification: The timestamp is checked to see if the digital signature was applied during the validity period of the certificate.
However, if any of these validation steps fail, the user receives a warning message, urging them to reconsider running the software.
In summary, Authenticode employs a multi-faceted approach to secure the software supply chain, involving hashing, key cryptography, and third-party validation. This ensemble of techniques ensures that both the identity of the publisher and the integrity of the software code are rigorously verified, forming the bedrock of software security in modern computing.
Authenticode can be used to sign Microsoft ActiveX controls, .cab files, Java applets, or any other executable files.
3. Types of Certificates Used in Authenticode
Authenticode leverages various types of certificates to achieve its mission of secure and verified software distribution. Understanding these certificates is key to grasping the nuances of how Authenticode operates.
Code Signing Certificates
These are the foundational elements of the Authenticode system. Code signing certificates are issued by trusted Certificate Authorities (CAs) and tied to a specific software publisher. The certificate contains information like the publisher’s name and the public key. When the software is signed using the publisher’s private key, this certificate is bundled with the software, serving as a virtual ID card that vouches for the source of the software.
Timestamping Certificates
Timestamping certificates add an extra layer of trust by recording the exact moment the software was signed. With this certificate, even if the original code signing certificate expires, users can still verify that the software was signed during a time when the certificate was valid. This is crucial for long-term software integrity, allowing software to maintain its authenticated status beyond the expiration date of the original code signing certificate.
Extended Validation (EV) Code Signing Certificates
EV Code Signing Certificates represent the highest level of trust and security in the Authenticode system. Obtaining one involves a rigorous validation process, where the software publisher must adhere to strict identity verification procedures. Software signed with an EV certificate typically triggers fewer security warnings, providing a smoother user experience. In many instances, platforms like Microsoft SmartScreen may treat software signed with an EV certificate more favorably, fast-tracking them through security checks.
4. Benefits of Using Authenticode
Having explored the technical aspects of Authenticode, let’s shift gears and delve into the benefits it offers. Authenticode isn’t just about cryptographic hashes and digital certificates; it’s about building a safer, more reliable digital world.
Enhancing Trust
In a digital landscape riddled with threats, trust is a valuable currency. Authenticode helps build this trust by assuring users that the software they are downloading or installing comes from a verified source and remains untampered. When users see that a piece of software is signed with a valid certificate, their confidence in using the software shoots up.
Protection against Tampering
One of the paramount goals of Authenticode is to safeguard software integrity. By verifying that the code has not been altered since it was signed, Authenticode effectively defends against unauthorized modifications. This is vital for protecting users from malware injections and other forms of code tampering that could compromise security.
Facilitating Secure Distribution
For software publishers, Authenticode significantly smoothens the distribution pipeline. Platforms and browsers are increasingly skeptical of unsigned software, often flagging them as potential threats. Having an Authenticode signature ensures that your software sails through these security checks, providing an uninterrupted download and installation experience for the user.
In conclusion, Authenticode offers a trifecta of benefits—trust, security, and ease of distribution—that together build a robust framework for software authentication. It balances technical finesse with practical advantages, making it an indispensable tool in the realm of software security.
5. Limitations and Drawbacks
While Authenticode offers an array of benefits, it’s critical to also consider its limitations and drawbacks. No system is foolproof, and understanding these constraints is essential for a well-rounded perspective on software security.
Costs Involved
One of the primary barriers to the widespread adoption of Authenticode is the cost. Acquiring a digital certificate from a reputable Certificate Authority (CA) often involves a financial investment that may be prohibitive for small developers or open-source projects. Ongoing costs may also include renewal fees and administrative charges for certificate management.
Expiry and Revocation
Digital certificates have expiration dates, necessitating periodic renewals to maintain the authenticated status of the software. Additionally, if a private key is compromised, the certificate must be revoked, leading to potential distribution hitches and requiring reissuing and re-signing—a complex and time-consuming affair.
False Sense of Security
Authenticode verifies the source and integrity of software, but it does not evaluate the quality or safety of the code itself. Malicious software can also be signed if the attacker manages to deceive the CA or compromise a publisher’s private key. Thus, users should exercise caution and not blindly trust all signed software.
6. Authenticode in Action: Use Cases
To better understand the value and application of Authenticode, let’s examine a couple of real-world use cases that highlight its significance in software security.
Case Study 1: Secure Software Distribution
Context:
A mid-size software company specializing in financial tools aimed to distribute its new accounting software globally.
Challenge:
Ensuring the software reaches the end-user without tampering and retains the user’s trust in the brand.
Solution:
By employing Authenticode, the company was able to securely sign its software. Users downloading the software could easily verify its legitimacy, thereby boosting confidence in the product and the brand.
Outcome:
An increase in software adoption rates, reduced instances of software tampering, and a strong reputation for security and reliability.
Case Study 2: Enterprise-Level Application Security
Context:
A large enterprise with stringent internal security protocols needed to deploy a set of internal tools across multiple departments.
Challenge:
Ensuring, in fact, that the software tools were not tampered with during distribution and that they came from an authenticated internal source.
Solution:
Authenticode was used to sign the internal software tools. The use of Extended Validation (EV) Code Signing Certificates added an extra layer of trust and ensured a smoother rollout with fewer security warnings.
Outcome:
Secure and seamless software deployment bolstered internal confidence in the tools and a significant reduction in security risks related to software integrity.
In summary, by highlighting these use cases, we can see how Authenticode serves as an invaluable asset for both software publishers and end-users. In fact, it helps in securely bridging the gap between software production and consumption, providing a win-win situation for all involved parties.
7. Setting Up Authenticode for Your Software
Implementing Authenticode may seem like a technical labyrinth, but broken down into steps, it’s a manageable and straightforward process. Here’s a step-by-step guide to get you started:
Step-by-Step Guide
1. Obtaining a Certificate
Before you can sign your software, you need a code signing certificate. Follow these steps:
- Select a Certificate Authority (CA): Choose a reputable CA that offers code signing certificates.
- Submit Application: You’ll have to provide documentation to verify your identity or your organization’s identity.
- Undergo Validation: The CA will verify your credentials before issuing a certificate.
- Retrieve Certificate: Once validation is complete, you’ll receive your digital certificate containing your public key and other details.
2. Signing the Code
With the certificate in hand, you can now sign your software.
- Prepare the Code: Ensure your software is in its final version, as any changes post-signing will invalidate the signature.
- Generate a Hash: Use cryptographic algorithms to create a hash of your software.
- Apply the Signature: Use your private key to sign the hash.
- Attach the Certificate: Bundle the signed hash and the digital certificate with your software package.
3. Verifying the Signature
It’s a good practice to verify the signature to ensure everything is set up correctly.
- Use Verification Tools: Most operating systems have built-in tools to verify digital signatures.
- Check the Hash: The verification process should regenerate the hash of the downloaded software and compare it against the decrypted hash from the signature.
- Validate the Certificate: Ensure that the accompanying certificate is still valid and has not been revoked.
8. Best Practices in Managing Authenticode
Now that you’re up and running, maintaining the integrity and security of your Authenticode implementation is crucial. Here are some best practices to follow:
Certificate Management
- Secure Private Keys: Your private key is a critical asset; store it securely to prevent unauthorized access.
- Regular Renewals: Keep tabs on your certificate’s expiration date and renew it well in advance to avoid service disruption.
- Revoke When Necessary: If you suspect your private key is compromised, revoke the certificate immediately and obtain a new one.
Regular Auditing
- Monitor Signature Status: Regularly check the validity of the signatures on your distributed software.
- Audit Certificate Usage: Ensure only authorized personnel have access to the certificate and monitor its usage.
- Review Security Policies: Regularly update your internal security policies to adapt to new security threats and challenges.
Third-party Tools and Resources
- Automated Signing: Consider using automated code signing solutions that integrate with your development and distribution pipeline.
- Validation Services: Use third-party services that can externally validate your signatures and provide an extra layer of trust.
- Community Resources: Stay updated with security trends and best practices by engaging with developer communities and forums.
By following these guidelines, in fact, you not only uphold the security of your software but also build lasting trust with your users. Authenticode isn’t just a tool; it’s a commitment to a safer and, certainly, more secure digital world.
9. Future of Authenticode
As cybersecurity threats continue to evolve, so too must the tools we use to combat them. Authenticode is no exception. Let’s take a look at what the future holds for this venerable technology.
Upcoming Features and Enhancements
While specific roadmaps are often kept under wraps, the general trend suggests that Authenticode will become even more secure, versatile, and easier to use. We can expect:
- Stronger Cryptographic Algorithms: As computational power increases, stronger hashing algorithms will likely be employed.
- Machine Learning Capabilities: Integration of AI could help in automating certificate management, flagging unusual activities, and improving overall security.
- User Interface Improvements: More intuitive tools and dashboards are likely to be introduced to make managing certificates simpler for developers.
Integration with Other Security Mechanisms
Given the interconnectedness of security technologies, Authenticode is likely to see increased integration with other mechanisms such as:
- Endpoint Security Systems: Combining Authenticode with endpoint security solutions could offer more comprehensive protection.
- Blockchain: A decentralized and immutable ledger could offer another layer of verification, ensuring even greater security.
- Zero Trust Architecture: Authenticode could be incorporated into a broader zero-trust framework that assumes no user or system is trustworthy until proven otherwise.
10. Conclusion
Authenticode serves as a vital bridge between software developers and end-users, ensuring that the software distributed is both secure and trustworthy. From the types of certificates used to its numerous benefits, we’ve covered a gamut of facets that make Authenticode indispensable. However, while it offers a robust method of verifying software integrity, it’s not a panacea and comes with its own set of limitations.
To conclude, the key to maximizing Authenticode’s utility lies in effective certificate management, regular auditing, and staying abreast of the latest security trends. As we look to the future, Authenticode is poised for significant enhancements that promise to keep it relevant in an ever-evolving cybersecurity landscape.
11. Additional Resources
Recommended Books
- “Cryptography and Network Security” by William Stallings
Tools
- SignTool: Microsoft’s command-line tool for code signing.
- DigiCert Certificate Utility: A user-friendly tool for certificate management.
Websites
- Microsoft Authenticode Documentation
- CA Security Council
- Stack Overflow: A valuable resource for any coding or implementation questions you might have.
- Image credits: PrimeKey.com
Finally, by investing in a deeper understanding and effective implementation of Authenticode, you’re not just fortifying your software—you’re contributing to a safer, more secure digital world for all.