The CHAP Protocol represents a pivotal chapter in the history of network security protocols. Developed as a more secure alternative to its predecessors, CHAP played a crucial role in authenticating network connections, especially in wide-area networks (WANs).
This article explores CHAP’s methodology, its place within PPP authentication schemes, and the transition to modern authentication protocols.
Index
- What is CHAP (Challenge Handshake Authentication Protocol)?
- How CHAP Protocol Works
- CHAP vs. Other PPP Authentication Protocols
- The Transition from CHAP to Modern Authentication Protocols
- The Legacy and Current Relevance of CHAP
- Conclusion
- References

1. What is CHAP (Challenge Handshake Authentication Protocol)?
Challenge Handshake Authentication Protocol, or CHAP, is an encrypted authentication scheme in which the unencrypted password is not transmitted over the network. Challenge Handshake Authentication Protocol (CHAP) is one of several authentication schemes used by the Point-to-Point Protocol (PPP), a serial transmission protocol for wide area network (WAN) connections. Other authentication schemes supported by PPP include Password Authentication Protocol (PAP), Shiva Password Authentication Protocol (SPAP), and Microsoft Challenge Handshake Authentication Protocol (MS-CHAP).
CHAP was designed to provide a more secure alternative to the Password Authentication Protocol (PAP) and other schemes by utilizing encryption techniques to protect transmitted information.
2. How CHAP Works
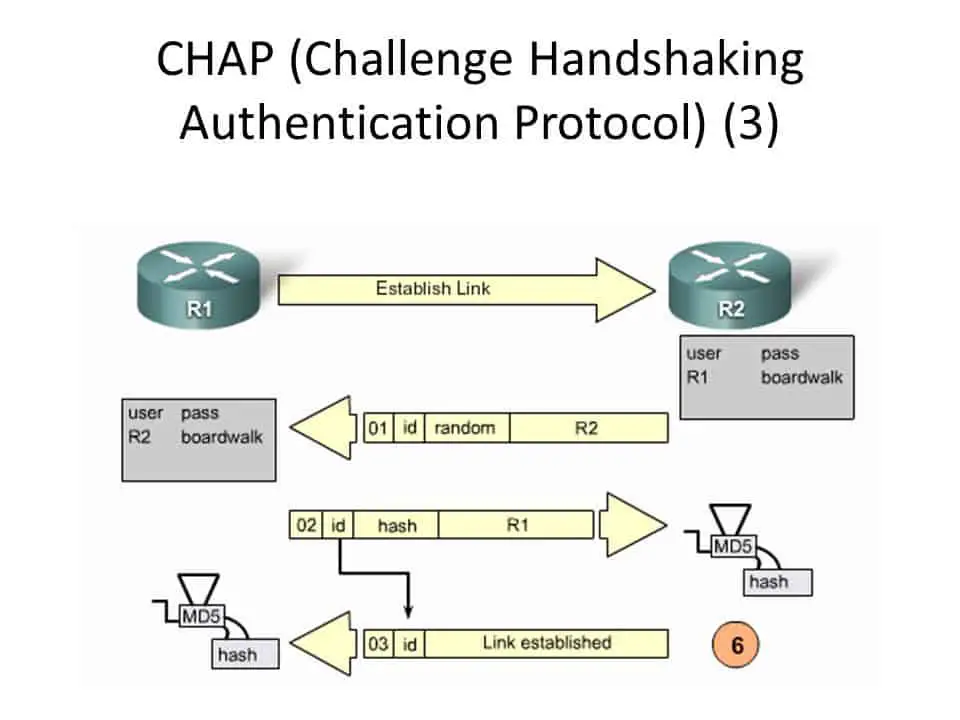
The Challenge Handshake Authentication Protocol (CHAP) secures network access using a three-way handshake mechanism, ensuring that the password is never actually transmitted over the network. This process involves several key steps:
- Challenge Phase: Upon request for access, the server sends a challenge to the client. This challenge is a randomly generated string, ensuring that each authentication session is unique and preventing replay attacks.
- Response Phase: The client, upon receiving the challenge, concatenates the challenge string with its password and applies a one-way hashing function (typically MD5) to this combination. The hash output, along with the username, is then sent back to the server as the response to the challenge.
- Verification Phase: The server performs a similar hashing operation on its side, using the challenge it sent and the password known to it for the user. If the hash value generated by the server matches the hash value received from the client, the authentication is deemed successful, and access is granted.
- Maintenance Phase: To maintain security throughout the connection, the CHAP Protocol periodically repeats the challenge-response process at random intervals. This ensures continuous verification of the client’s identity and guards against session hijacking.
This robust mechanism significantly enhances security by ensuring that the actual password is never exposed during the authentication process and by providing dynamic verification throughout the session.
3. CHAP vs. Other PPP Authentication Protocols
CHAP stands out among PPP authentication protocols due to its enhanced security features. Let’s compare CHAP with its counterparts:
- PAP (Password Authentication Protocol): PAP is the simplest form of authentication, where the username and password are sent “in the clear” over the network. This makes PAP highly susceptible to eavesdropping and replay attacks. Unlike CHAP, PAP does not offer encryption or periodic authentication checks.
- SPAP (Shiva Password Authentication Protocol): SPAP is a proprietary protocol developed by Shiva Corporation, offering a slightly more secure alternative to PAP by encrypting the password. However, it lacks the dynamic challenge-response mechanism and widespread support of CHAP.
- MS-CHAP (Microsoft Challenge Handshake Authentication Protocol): MS-CHAP is Microsoft’s variation of CHAP, designed to integrate with Windows network environments. It offers two versions, MS-CHAP v1 and MS-CHAP v2, with the latter providing enhanced security through mutual authentication and stronger encryption techniques. While MS-CHAP improves upon CHAP’s framework, it has been criticized for vulnerabilities and is considered less secure than newer protocols.
CHAP’s method of using a challenge-response mechanism for authentication provides a significant security advantage over PAP and SPAP, and while MS-CHAP offers improvements for Windows environments, it too has been surpassed by more secure alternatives.
4. The Transition from CHAP to Modern Authentication Protocols
The evolution from the CHAP Protocol to modern authentication protocols reflects the increasing complexity of network environments and the need for more sophisticated security measures.
Key developments include:
- EAP (Extensible Authentication Protocol): EAP is a framework that supports multiple authentication mechanisms, including tokens, smart cards, and certificates. EAP is flexible and adaptable to various network environments, including wireless networks, making it a versatile choice for modern authentication needs.
- OAuth and OpenID Connect: These protocols are designed for secure authorization in a decentralized environment, such as the Internet. They are widely used for web and mobile applications, providing secure access to resources without exposing user passwords.
- Kerberos: A protocol that uses strong symmetric-key cryptography for mutual authentication between the client and server. Kerberos is highly regarded for its ability to securely manage authentication for distributed services.
The transition to these protocols has been driven by the need for more robust security, flexibility, and compatibility with a broader range of services and devices. Modern protocols address the limitations of CHAP by offering stronger encryption, mutual authentication, and support for a wider variety of authentication methods, catering to the security demands of today’s networked environments.
5. The Legacy and Current Relevance of CHAP
The Challenge Handshake Authentication Protocol (CHAP) has left an indelible mark on the landscape of network security. Its legacy is twofold: it represents a significant step forward in authentication technology and continues to influence the design of modern security protocols. Despite being overshadowed by more sophisticated technologies, CHAP’s principles remain relevant in understanding the evolution of network security measures.
Legacy
CHAP was a groundbreaking solution in its time, addressing the glaring vulnerabilities of its predecessors like PAP. By introducing a challenge-response mechanism and periodic authentication verification, the CHAP Protocol significantly improved the security of network access. These concepts have become foundational in the development of subsequent authentication protocols, highlighting CHAP’s lasting impact on the field.
Current Relevance
In today’s network security environment, CHAP is rarely used in its original form for public internet connections, largely due to advancements in encryption and authentication technologies. However, its presence is still felt in certain niche applications and legacy systems where its level of security suffices and where system updates might not be feasible or cost-effective. Furthermore, CHAP’s methodology informs the ongoing development of security protocols, underscoring the importance of continuous authentication and the avoidance of direct password transmission over networks.
Moreover, CHAP’s simplicity and effectiveness in specific contexts, such as within VPNs or PPPoE connections, demonstrate that older protocols can still serve a purpose in complementing the security of modern networks. This enduring relevance underscores the importance of understanding the CHAP Protocol as part of the broader narrative of network security evolution.
6. Conclusion
The Challenge Handshake Authentication Protocol (CHAP) has played a crucial role in the evolution of network authentication. By implementing a secure method for verifying a user’s identity without transmitting their password, CHAP set a new standard for security during its time. While modern protocols have surpassed CHAP in terms of security and versatility, the principles it introduced continue to influence the design and implementation of contemporary authentication methods. Understanding CHAP’s mechanisms, its comparative advantages, and its legacy provides valuable insights into the ongoing development of network security protocols. As technology progresses, the lessons learned from the CHAP Protocol will undoubtedly continue to inform future innovations in cybersecurity.
7. References
- RFC 1334: “PPP Authentication Protocols” – This document provides the technical specifications for PAP and CHAP, offering a deep dive into the protocols’ operational details.
- Kurose, James F., and Keith W. Ross: “Computer Networking: A Top-Down Approach” – This textbook offers comprehensive coverage of networking concepts, including authentication protocols like CHAP, within the broader context of computer networks.
- Stallings, William: “Network Security Essentials: Applications and Standards” – Stallings’ work discusses various aspects of network security, including authentication protocols and their evolution over time.