Prevention is the key when it comes to network security. However, identifying a potential intrusion is not always obvious. The usual security suspects – Soviet spies, CIA agents, and industrial espionage – don’t pose real risks to the average company. Still, just because you’re not building the next secret weapon doesn’t mean that you’re not at risk from security breaches.

Index
- What is a firewall?
- Protecting the Perimeter
- Exposed to the Net, only if we need to!
- Security threats examples
- Personal Firewalls
- Why are Firewalls and Intrusion Detection Systems (IDS) important
- Keeping the bad guys out of the network
- What Does a Firewall Do?
- How to tell if it’s a good packet or a bad packet
What is a firewall?
Firewalls are network security devices that are designed to monitor both outgoing and incoming network traffic. It also doubles in functioning as a block and permission to data packets, with all its actions based on particular security rules.
The primary purpose of the firewall is to make sure that there is the presence of a barrier, right in between your internal network system and the external traffic of data coming from foreign network sources. For instance, if your company manages a LAN, any data that is to go into the LAN from another source will first have to go through the firewall. This way, vibrated and malicious data traffic can be identified and blocked.
Check our main article: Firewall.
Protecting the Perimeter
As more computers connect to public networks, and as their employees connect to work through the Internet, opportunities increase for malicious attacks from hackers and Hijackers. The same applies to internal corporate networks, in that companies must protect their data centers and computing resources from internal and external attacks.
News stories often tell of websites being broken into, computers being erased, corporate data being stolen, and lethal viruses destroying computer systems.
With the number of home users taking advantage of broadband “always-on” networks, hackers and data thieves have a whole playground of unsuspecting exposed home networks to tamper with.
Network attacks can occur for a variety of reasons: extortion, fraud, espionage, sabotage, or simple curiosity. The acts themselves can involve a range of activity, including misuse of authorized systems, system break-ins, equipment theft, interception of network traffic, and reconfiguration of computer systems to allow for future access. Because of the nature of global networks, these attacks can (and often do) cross network and national boundaries.
How can home users and corporations protect themselves?
Exposed to the Net, only if we need to!
The most secure way to avoid an attack is to stay away from the network. Physical security remains an issue, but otherwise going off-net is the most secure method to reduce exposure to security risks.
That’s an unreal option.
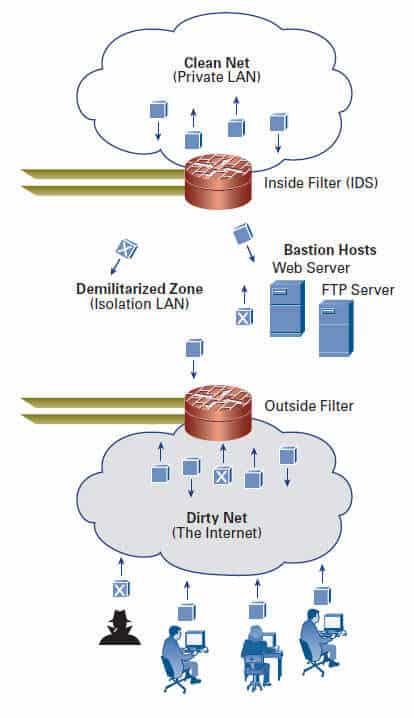
Instead, there is the concept of perimeter security. Perimeter security traditionally is provided by a firewall. Firewalls sit between an unsafe (“dirty”) or WAN side and a safe (“clean”) or LAN side.
Sometimes, devices such as web servers or intrusion-monitoring products sit between the WAN and LAN sides. This “limbo” location between the dirty and clean networks is often called the demilitarized zone (DMZ).
For example, a home user could put a firewall between his or her computer and the Internet connection. The side of the firewall that connects to the Internet is the dirty side (meaning that the traffic cannot be trusted), and the side of the firewall that connects to the home network is the clean side (the traffic can be trusted). The firewall inspects packets going in either direction and determines whether the traffic should be allowed to pass through or should be dropped.
The firewall has become the central location to perform perimeter-related activities.
Security threats examples
Firewalls are designed to combat network-related security threats such as the following:
- Passive eavesdropping: Attackers can use packet-capture programs to glean sensitive information or steal username/password combinations.
- IP address spoofing: An attacker pretends to be a trusted computer by using an IP address that is within the accepted range of internal IP addresses. This is similar to assumed identity.
- Port scan: Servers “listen” for traffic on different ports. For instance, port 80 is where servers listen for web HTTP traffic. Attackers find ways to infiltrate servers through individual server ports.
- DoS attack: The attacker attempts to block valid users from accessing servers by creating TCP SYN (or ICMP, or other) packets that exhaust the server and keep it from being able to handle any other valid requests. These types of attacks are also called ping floods.
- Application layer attack: These are attacks that exploit the weaknesses of certain applications to obtain illicit access to the hosting server.
Firewalls let you block these and other attacks by inspecting traffic, keeping track of valid sessions, and filtering traffic that looks suspect so that it cannot pass.
Personal Firewalls
Another type of firewall that has become popular is the personal firewall.
Typically, this is a software program on a laptop or computer that acts as a firewall. Its function is slightly different than the firewalls just described.
Personal firewalls typically guard a computer or laptop against unauthorized installation of programs, such as a malicious program or spyware installing itself on your computer, commonly without the user’s knowledge.
Another function of the personal firewall is to monitor programs on the computer that are trying to access the Internet, enabling the user to allow or deny access program by program. In this way, malicious programs seeking to access the Internet, either to propagate themselves or to report information back to the creator, can be blocked from doing so.
To learn more about Personal Firewalls, pick up a copy of Home Network Security Simplified (Cisco Press).
Why are Firewalls and Intrusion Detection Systems (IDS) important
Firewalls and Intrusion Detection Systems (IDS) provide perimeter defense for corporate and personal networks. As hackers have become more sophisticated (and aggressive) in their attacks, so has the technology behind keeping networks safe. Firewalls and IDS were created as a direct response to hackers.
In addition to pure technology advances, a great deal of innovation has occurred concerning how to deploy these systems. This topic is of special importance to companies with websites.
Article: Do you know what edge traversal is?
Keeping the bad guys out of the network
The main goal of perimeter security is to keep the bad guys out of the network. The only way to be absolutely sure about perimeter security is to not connect to anything. Most companies rely on the Internet, though, and for some it is a critical aspect of their business. The problem to be solved, then, is how to have an external presence and still be relatively safe against attacks.

The answer is the three-part firewall system, which places external-facing servers in an intermediate zone (DMZ) in the network between two separate firewalls.
What Does a Firewall Do?
Firewalls keep both corporate and personal networks safe from attack by inspecting packets for known attack profiles and by acting as a proxy between you and the rest of the world.
Profiles (such as virus signatures or rules for packet contents) are usually discovered and maintained by service companies that sell the profile packages for a fee.
The proxy function works by using a third IP address (as opposed to the user’s actual source IP address or that of the server) whenever you communicate with the world. That way, no one knows your actual IP address.
How to tell if it’s a good packet or a bad packet
In terms of a firewall system, good packets fall into two categories:
- Good outbound packets are sent by inside users to approved external locations, such as a website.
- Good inbound packets originate outside the external firewall. They either correspond to a TCP session originated by an inside user (that is, they can only be response packets) or are accessing publicly available services such as web traffic.
Bad packets are pretty much everything else (unsolicited packets that are not sent in response to a request from inside). They are discarded for the safety of the network.
Clean Net
The clean net is the interior corporate network.
The only “outside” packets permitted on the clean net are those that have been inspected and have the acknowledgment to a TCP packet generated from an inside computer.
Inside Filter
The inside filter performs the functions of both a firewall and intrusion detection system. In addition to blocking attacks such as DoS, it inspects every packet, making sure that no externally initiated TCP sessions reach the clean net, because hackers can gain access by spoofing a session. Any packets of questionable origin get trashed. The inside filter also inspects outbound packets to ensure compliance with corporate policies.
Isolation LAN
The isolation LAN or DMZ acts as a buffer between outside- (web) facing applications and the clean LAN. Servers located in the DMZ are called bastion hosts. Outsiders use them to access public web pages or FTP servers. These servers are protected but are still prone to hackers. Bastion hosts should have as few services as possible and should contain very simple access rules to prevent back doors into the clean LAN.
Outside Filter
The outside filter is a firewall that screens for TCP replies and UDP packets assigned to port numbers associated with whatever bastion hosts are present.
This firewall should have only static routes and very clean rules because complicated processes are prone to errors, and hackers love errors!
The Dirty Net
The Internet is often called “the dirty net” by network and security admins. In the interest of network security, they assume that every packet is sent by a hacker until proven otherwise. The vast majority of users are honest, but this guilty-until-proven-innocent attitude can and does prevent disasters.
Hackers and Their Evil Ways
Hackers use a number of tools and tricks to exploit networks. These include, but are not limited to, DoS attacks, IP address spoofing, viruses, worms, Trojan horses, and e-mail bombs. Many of these attacks are discussed in detail on separate articles.
(Adapted from CISCO NETWORKING SIMPLIFIED 2ND EDITION 2008, Jim Doherty, Neil Anderson, Paul Della Maggiora – CISCO PRESS)