Imagine sending a letter and forgetting to write down the address of your friend. You know their name and some details, but the postal code escapes you. In the digital world, a similar scenario unfolds when a device knows an IP address but seeks the corresponding domain name. This is where the concept of an inverse query, a somewhat old-school but intriguing aspect of the DNS, comes into play. Let’s explore the intricacies of inverse queries, their evolution, and their role in the seamless operation of the internet.
Index
- What is an Inverse Query?
- The Evolution of Inverse Queries
- Moving Beyond Inverse Queries
- Practical Applications and Considerations
- Conclusion
1. What is an Inverse Query?
An Inverse Query in the Domain Name System (DNS) represents a unique type of query where the roles are reversed: instead of translating a domain name into an IP address, it aims to find the domain name associated with a specific IP address. This process, known as reverse name lookup, is like flipping through an address book backwards to find someone’s name by their phone number.
In other words, an Inverse Query is a Domain Name System (DNS) query in which a resolver contacts a name server to perform a reverse name lookup, requesting a host name for a given IP address. An inverse query is the opposite of the usual DNS query – that is, given a host’s fully qualified domain name (FQDN), it determines the host’s IP address.
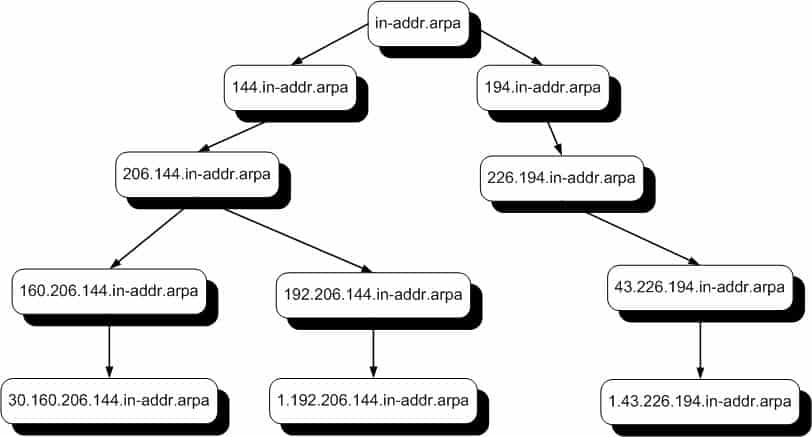
Because of the hierarchical structure of the namespace of the DNS, inverse queries normally have to search all domains to resolve the IP address. To circumvent this, a special domain called in-addr.arpa exists for reverse name lookups. The nodes in this domain are named after the IP addresses of hosts but with the octets in reverse order to facilitate searching. However, inverse queries can take place only on the name server queried and cannot be forwarded to another name server. Because individual name servers manage only a small portion of the entire DNS namespace, there is no guarantee that a given inverse query issued against a specific name server will meet with a successful response.
2. The Evolution of Inverse Queries
Initially, inverse queries were thought to serve as a fundamental tool within the DNS infrastructure, facilitating tasks such as verifying the identity of a host from its IP address. Due to the DNS’s hierarchical structure, performing an inverse query could theoretically require searching through the entire namespace, a daunting and inefficient task.
To streamline this process, the special domain in-addr.arpa was created. Designed specifically for reverse lookups, this domain organizes IP addresses in a mirror image of their forward counterparts, with octets reversed, simplifying the search. Despite this, inverse queries presented limitations, notably their inability to be forwarded beyond the initially queried name server.
3. Moving Beyond Inverse Queries
Over time, the practical use of inverse queries in DNS has largely been superseded by Pointer (PTR) records within the in-addr.arpa domain. PTR records provide a more direct and efficient mechanism for reverse DNS lookups, mapping IP addresses back to their canonical hostnames. This method is widely used for tasks such as email spam filtering, where verifying a sender’s domain against their IP address can help assess credibility.
4. Practical Applications and Considerations
While the term “inverse query” has faded from regular use, the concept of reverse lookups remains vital. Services like nslookup and diagnostic tools rely on the in-addr.arpa domain to perform these reverse mappings, ensuring that administrators can troubleshoot and verify network configurations.
Configuring PTR records for your domains, especially for mail servers, is crucial for smooth operation and compliance with best practices on the internet. It helps in reducing the chance of emails being marked as spam and assists in network troubleshooting and security auditing.
5. Conclusion
Though the term “inverse query” might evoke images of the DNS’s early days, the practice of reverse name lookups continues to be a cornerstone of network management and security. By understanding the transition from inverse queries to the use of PTR records in reverse DNS lookups, we gain insight into the DNS’s adaptability and its pivotal role in the internet’s infrastructure.