Definition of Network Address Translation (NAT) in The Network Encyclopedia.
What is NAT (Network Address Translation)?
NAT stands for Network Address Translation is a form of packet filtering used in firewall products that protect a network from outside intrusion by hackers. Network address translation (NAT) also eliminates the need for an organization to have a set of globally unique IP addresses, thus helping to conserve the available pool of IPv4 addresses for the Internet.
How It Works
NAT is essentially the translation of IP addresses in one network into those for a different network. NAT is usually implemented on firewalls in which one network (the private network) is hidden behind the firewall while the other network (the public network) represents distrusted users from whom the IP addresses of the private network must be hidden.
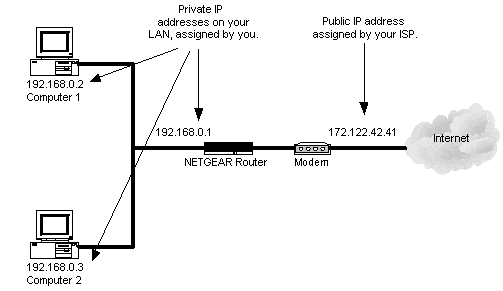
NAT replaces the internal network IP address for each Internet Protocol (IP) packet passing through the firewall with a dummy one from a fixed pool of addresses. The actual IP addresses of computers on the private network are thus hidden from users outside the firewall. All requests that pass through the firewall have their addresses translated on the way to the private network, and all responses returned to the unsecure public network have their addresses translated back on the way out of the private network.
Implementing NAT on a router or firewall essentially involves creating and configuring a NAT table containing the private/public IP address mappings. These mappings can be statically created or dynamically generated from a specified pool of IP addresses (either randomly or, more often, on a round-robin basis). A static NAT table essentially consists of a series of NAT rules that specify how IP addresses will be translated.
Static NAT
For example, a typical static NAT rule might be equivalent to the statement, “Translate all IP addresses belonging to the network 176.43.8.z to IP addresses in the form 145.5.133.z with the subnet mask 255.255.255.0 used for both networks.” This rule results in the address 176.43.8.1 being mapped to 145.5.133.1, 176.43.8.2 being mapped to 145.5.133.2, and so on.
Dynamic NAT
A dynamic NAT rule might be used when the number of IP addresses that need to be translated is not equal to the number of NAT IP addresses that you can translate to. In this case, if all the NAT IP addresses are being used, external hosts trying to form new connections are rejected. Each time a connection is formed between the external and internal networks, a different NAT IP address is assigned to the internal host being connected to. This effectively hides the network identity of the hosts on the private network from hosts outside the firewall.
Masquerading
Another NAT technique that is frequently implemented on Linux machines is called masquerading. In this situation, all the IP addresses of the internal private network are hidden to outsiders, who can access only the single IP address of the interface exposed to the public network. An arbitrary number of Transmission Control Protocol (TCP) connections can be multiplexed through the single IP address by assigning each connection a different port number (chosen by default from the range 61,000 through 65,096, which allows up to 4096 simultaneous connections).
In addition to securing your private corporate network, NAT also reduces the need to get a block of unique IP addresses from your Internet service provider (ISP). Only the far side of your router or firewall server needs a unique IP address from your ISP – you can use any IP addresses within your network because your private network is securely hidden from the outside world behind your firewall. This reduces costs and helps extend the viability of the current IPv4 system by reducing the number of unique IP addresses required on the Internet. In fact, the original impetus for the development of NAT technologies was the fact that the available pool of unique IPv4 addresses was steadily running out. NAT was viewed as a temporary solution until IPv6 could be standardized and implemented, but the security advantages of using NAT in firewalls has revitalized IPv4 and made migration to IPv6 less urgent.
NAT is defined in Request for Comments (RFC) 1631.