In the digital world, security isn’t just a feature; it’s a necessity. As we increasingly rely on online platforms for everything from social interaction to financial transactions, ensuring secure connections becomes a priority. One of the tools in the cybersecurity toolbox is Network Level Authentication (NLA). This article aims to distill the complexity of NLA into a straightforward explanation suitable for college students and digital enthusiasts alike.
Understanding the working of NLA will not only help you appreciate the intricate dance of secure network communication but also shed light on the extensive measures undertaken to safeguard our digital lives. Whether you’re studying computer science, or just interested in the mechanisms behind our daily digital interactions, our simple but comprehensive exploration of NLA is sure to enlighten you.
In this article:
- What is Network Level Authentication (NLA)?
- How Does Network Level Authentication Work?
- Network Level Authentication Vs. Standard Authentication
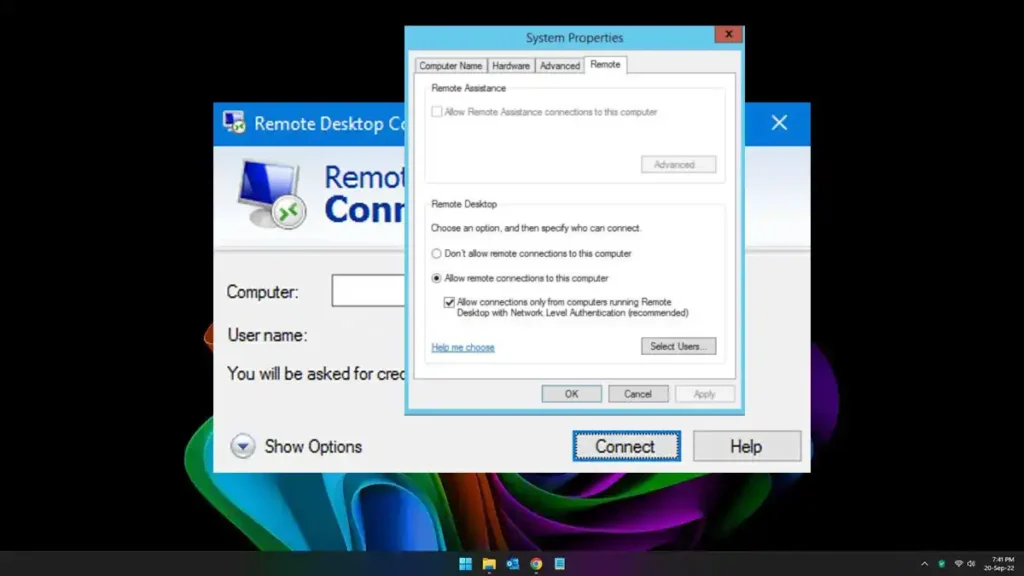
What is Network Level Authentication (NLA)?
Network Level Authentication, or NLA, is a security feature used in Remote Desktop Protocol (RDP) services. It’s like a trusted bouncer at the door of a private event – it ensures that only authorized users can establish a remote desktop session before full network access is granted.
In technical terms, NLA uses the Credential Security Support Provider (CredSSP) protocol to perform early user authentication, thereby adding an extra layer of security. This means the system checks the credentials of the user before creating a session or loading the full graphical user interface. By doing so, NLA significantly minimizes the resources a server uses per attempted connection and thereby mitigates the risks posed by denial-of-service (DoS) attacks.
How Does Network Level Authentication Work?
Network Level Authentication (NLA) works as a safety check at the initial stage of a Remote Desktop Protocol (RDP) connection. This safety check is based on the Credential Security Support Provider (CredSSP) protocol, which confirms the authenticity of the client and server.
During the NLA process, the client attempting to make a remote connection sends its credentials to the server. These credentials are encrypted and securely packaged using the Kerberos or NTLM (NT LAN Manager) authentication protocols. The server then checks these credentials before the full remote desktop connection is established.
If the credentials are verified, the server initiates the RDP session and loads the full graphical user interface for the user. If the credentials are incorrect or the user is not authorized, the server refuses the connection. This process happens before the server commits significant resources to the connection, thus protecting it from malicious attempts and preserving system resources.
Network Level Authentication Vs. Standard Authentication
When comparing Network Level Authentication (NLA) to Standard Authentication in a Remote Desktop Protocol (RDP) scenario, it’s crucial to understand their significant differences and the implications for system security and resource management.
Standard Authentication, which is sometimes referred to as ‘classic’ or ‘old-style’ RDP authentication, only occurs once the full RDP connection is established. This means the server has already committed system resources, including memory and CPU, to handle the connection. In this scenario, an unauthorized or malicious user could repeatedly attempt to connect, draining system resources and potentially leading to a Denial-of-Service (DoS) attack. Furthermore, it allows the full desktop environment to be exposed before authenticating, which might lead to potential security vulnerabilities.
On the other hand, NLA performs user authentication before fully establishing the RDP session. This early verification step means that system resources are only allocated once the user’s credentials are confirmed, thus saving significant resources and providing an extra layer of security. By mitigating potential DoS attacks and limiting exposure to malicious users, NLA provides a much stronger level of protection compared to Standard Authentication.