In computer science and networking, the term “Credentials” is ubiquitous, serving as the cornerstone of various security and authentication protocols. However, the term isn’t confined to a single meaning; it’s a multi-faceted concept that encompasses several different types of authentication data and usage scenarios. From simple username-password combinations to more complex two-factor authentication methods, the role of credentials is central to establishing and maintaining secure environments. This article aims to delve into the multi-dimensional aspect of credentials, covering their various types, applications, and best practices.
In this article:
1. What are Credentials in computer networking?
- Credentials critical role play in authentication and security
- Username and Password
- Token-based Credentials
- Biometric Credentials
- Digital Certificates
- Local Systems (Windows, macOS, Linux)
- Networking (Wi-Fi, VPN)
- Web Services (OAuth, OpenID)
- Enterprise Solutions (Active Directory, LDAP)
- Brute Force Attacks
- Phishing
- Credential Stuffing
- Man-in-the-Middle Attacks
5. Best Practices for Managing Credentials
- Strong Password Policies
- Multi-Factor Authentication (MFA)
- Role-Based Access Control (RBAC)
- Regular Auditing and Monitoring
- Password Managers
- Secure Vaults
- Hardware Security Modules (HSMs)
- Passwordless Authentication
- Blockchain-based Credentials
- AI-driven Security Measures
8. Conclusion
1. What are Credentials in Computer Networking?
In the realm of computer networking, credentials function as the keys to the digital kingdom. Simply put, they are sets of information that prove you’re who you claim to be. More often than not, these come in the form of a username and password. However, as we’ll see later, the landscape is evolving rapidly, encompassing a diverse array of authentication data beyond just these two elements.
So, why are credentials indispensable? Well, they serve as the first line of defense in a layered security architecture. When you log in to a server, connect to a VPN, or access a secure website, it’s your credentials that affirm your identity. In turn, the system decides the level of access you should have, based on these credentials. This is not just about gaining entry; it’s about ensuring that the right individuals have the appropriate access level.
The stakes are high. Incorrectly managed, credentials become vulnerable to a myriad of attacks. Think about data breaches or unauthorized access—a colossal mess waiting to happen. Therefore, robust credential management isn’t a luxury; it’s a necessity. It provides the backbone for robust security policies and plays a critical role in compliance with various regulatory frameworks. In short, the care and management of credentials are not tasks to be taken lightly.
So, whether you’re a network administrator safeguarding sensitive information or a user looking to protect your personal data, understanding credentials is not just beneficial—it’s vital. As we navigate through the layers of credential types, their applications, and best practices, you’ll find that this seemingly simple concept is, in fact, a linchpin in the evolving framework of cybersecurity.
Armed with this foundational knowledge, we’ll dive deeper into the various types of credentials, their applications, and how to manage them securely. Stay tuned as we unlock the intricate world of credentials in computer networking.
2. Types of Credentials
Credentials are not a one-size-fits-all concept. The digital age has propelled us into an era where a single username and password combination is no longer the gold standard for security. Today, we’re looking at a spectrum of credential types, each with its own unique features, advantages, and security implications. Let’s break down the most common types and how they function in the realm of computer networking.
Username and Password
The classic duo. The username identifies you, and the password verifies you. This pair has been the cornerstone of authentication for decades. However, while easy to implement and use, they are increasingly becoming the weakest link in the security chain.

Simple passwords are easy to guess, and even complex ones can be cracked with enough computational power. This form of credentials is often supplemented by other types, especially in more secure environments, to create multi-factor authentication (MFA) setups.
Token-based Credentials
Welcome to the next level of security. Token-based credentials provide an additional layer of complexity and security. These can be either hardware tokens, like a security fob generating time-based codes, or software tokens, which are temporary, generated by an application. These tokens provide a dynamic element to the authentication process, making it more robust against attacks. They’re often used in two-factor (2FA) or multi-factor authentication (MFA) systems, paired with other forms of credentials for heightened security.
Biometric Credentials
Why remember something when you can just be yourself? Biometric credentials like fingerprints, face scans, and iris recognition provide a very personal layer of security. Unique to each individual, these credentials are extremely difficult to replicate. However, they come with their own set of challenges, such as potential errors in recognition or privacy concerns. Nevertheless, when implemented correctly, they offer a high level of security and are often used in secure corporate environments and cutting-edge consumer devices.
Digital Certificates
Here’s where we get into the realm of cryptographic security. Digital certificates involve the use of a public and a private cryptographic key pair that is provided by a Certificate Authority (CA). They are often used in secure communications over the Internet, as well as in corporate networks. Digital certificates provide a way to prove a user’s identity electronically and ensure the integrity of messages.
In summary, the landscape of credentials in computer networking is as varied as it is vital. The complexity of today’s digital interactions requires an equally nuanced approach to authentication and security. By understanding the various types of credentials, their applications, and their associated benefits and drawbacks, you arm yourself with the knowledge to create or navigate secure networks effectively.
3. Applications and Contexts
Credentials are not limited to a single application or context; rather, they permeate every layer of digital interaction. Whether you’re logging into your personal computer or connecting to a secure enterprise network, some form of credentials is invariably involved. Below, we examine various applications and contexts where different types of credentials are employed.
Local Systems (Windows, macOS, Linux)
Local systems, namely, your desktops and laptops running on Windows, macOS, or Linux, generally use a combination of usernames and passwords. Some modern systems also incorporate biometric credentials like fingerprint scans or facial recognition. For instance, Windows Hello and Apple’s Touch ID offer secure, biometrically-enabled logins. Linux, being highly customizable, can also be configured to use a range of credential types.
Networking (Wi-Fi, VPN)
In the realm of networking, passwords remain commonplace for Wi-Fi authentication. More secure networks, like VPNs, often require digital certificates or token-based credentials for access. For example, many corporations utilize VPNs with multi-factor authentication, where a username and password are just the first layer, supplemented by a token or a digital certificate to enhance security.
Web Services (OAuth, OpenID)
When it comes to web services, third-party authentication methods like OAuth and OpenID have gained traction. These technologies allow users to log in to various services using a single set of credentials. Typically, this involves token-based credentials granted after initial authentication, which permits the user access to multiple services without requiring them to log in repeatedly. This is a win-win, offering both convenience and an additional layer of security.
Enterprise Solutions (Active Directory, LDAP)
In larger organizational contexts, enterprise solutions like Microsoft’s Active Directory or Lightweight Directory Access Protocol (LDAP) are often used. These systems centralize credential management, allowing for intricate permission layers and robust security protocols. Active Directory, for example, can enforce policies like regular password changes and complexity requirements. It can also integrate with other credential types such as digital certificates or biometric data, creating a multi-factor authentication system that is both robust and scalable.
To sum up, the choice of credentials depends heavily on the context and the level of security required. Whether it’s a simple username-password combo for local systems or complex multi-factor authentication in enterprise solutions, credentials are the linchpin of digital security. Understanding the applications and contexts in which different types of credentials operate not only broadens your understanding of computer networking but also empowers you to implement effective and secure systems.
4. Security Concerns
Credentials, while essential for authentication and authorization, are also potential weak links in the security chain. In the wrong hands, they can serve as the keys to your digital kingdom, unlocking a wealth of sensitive information. Below, we delve into some of the most common threats that target credentials.
Brute Force Attacks
Brute force attacks involve automated attempts to guess a user’s password. This tactic is not sophisticated but can be effective against weak passwords. The advent of powerful computing resources has made it easier for attackers to try thousands of combinations in a short period, making even moderately strong passwords vulnerable.
Phishing
Phishing attacks are a little more nuanced. They often involve sending fraudulent messages that appear to come from reputable sources to trick users into revealing their credentials. From fake login pages to urgent security alerts, the range of phishing techniques is vast, but the goal is usually the same: to steal your username and password.
Credential Stuffing
Credential stuffing occurs when attackers use previously leaked username-password pairs to gain unauthorized access to accounts on different platforms. This is effective because many people reuse the same passwords across multiple services, making it easier for attackers to compromise several accounts in one swoop.
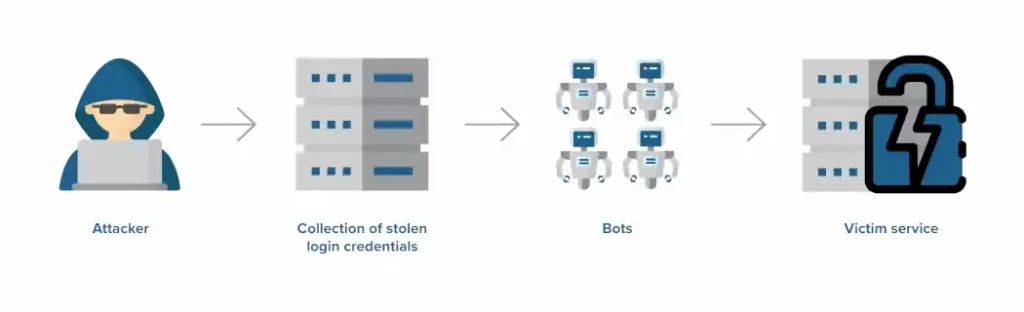
Man-in-the-Middle Attacks
In a Man-in-the-Middle (MitM) attack, the attacker secretly intercepts and possibly alters the communication between two parties. This could happen during the transmission of credentials over an unsecured network, allowing the attacker to capture and then use those credentials for unauthorized activities.
5. Best Practices for Managing Credentials
Considering the range of threats out there, effective credential management is a non-negotiable aspect of modern cybersecurity. Here are some best practices for managing your credentials effectively.
Strong Password Policies
Implementing a strong password policy is the first line of defense against brute-force and credential stuffing attacks. Encourage the use of long passwords that include a mix of letters, numbers, and special characters. Also, mandate frequent password changes to reduce the risk of unauthorized access.
Multi-Factor Authentication (MFA)
MFA adds an additional layer of security by requiring two or more verification methods—a password, a security token, or biometric verification, for example. This significantly reduces the risk of unauthorized access even if one set of credentials is compromised.
Role-Based Access Control (RBAC)
Role-Based Access Control allows you to assign system access to users based on their role within the organization. This minimizes the chances of unauthorized access to sensitive information, as users can only access the information necessary to perform their job functions.
Regular Auditing and Monitoring
Regular audits and monitoring can help you detect any unusual activity that may indicate a compromised account. Early detection is crucial for minimizing the damage caused by any security breach.
By incorporating these best practices into your credential management strategy, you not only protect individual accounts but also fortify your overall network security posture. This multi-pronged approach ensures that you are well-equipped to face the ever-evolving landscape of cybersecurity threats.
6. Credential Storage
In an era of proliferating digital services, managing multiple credentials has become a cumbersome yet critical task. Poor storage practices can become a point of failure in the security chain. Let’s explore some advanced options for securely storing your credentials.
Password Managers
A password manager stores and manages your passwords in an encrypted format and provides secure access to all your passwords with a single master password. The best password managers also include features like password generation and the ability to assess the strength of your existing passwords.
Secure Vaults
Secure vaults, or secret vaults, offer an encrypted database for storing sensitive credentials, keys, and other secure data. They are especially beneficial in enterprise settings where multiple personnel require access to shared credentials. These vaults generally support role-based access controls, making them a fine-grained tool for credential management.

Hardware Security Modules (HSMs)
HSMs are physical devices that safeguard and manage digital keys for strong authentication and provide cryptoprocessing. They are designed to be tamper-evident and to resist unauthorized access to the sensitive material they hold.
7. Emerging Trends
As the landscape of digital threats evolves, so does the technology to counter these threats. Emerging trends in credential management aim to enhance security while also offering a more user-friendly experience.
Passwordless Authentication
The concept of passwordless authentication eliminates the need for users to remember or input passwords, replacing them with more secure and convenient methods like biometric data or hardware tokens. This significantly reduces the risks associated with weak or reused passwords.
Blockchain-based Credentials
Blockchain technology offers a decentralized approach to credential management. By storing credentials in a blockchain, users can directly and securely interact with services without going through a central authority, thereby reducing the potential points of failure.
AI-driven Security Measures
Artificial Intelligence is increasingly being employed to detect abnormal usage patterns or anomalies, making it easier to spot potential security threats. AI algorithms can even predict future attack vectors and automatically bolster security measures.
8. Conclusion
Credential management is a cornerstone of digital security, both for individual users and within enterprise settings. This article has navigated through the types of credentials, their applications, security concerns, and best practices in credential management. Emerging trends like passwordless authentication and AI-driven security measures show a promising future in which managing our digital identities could be both simpler and safer. Whether you are an individual user or an IT administrator, being well-versed in the best practices and emerging trends in credential management will serve you well in the ever-changing digital landscape.