In the evolving landscape of network administration and security, the tools and utilities we use have transformed dramatically. One such tool, which once held prominence in the Windows NT era, was the ‘Network Monitor Agent’. Let’s delve into its history, understand its functions, and explore its evolution into the sophisticated network monitoring tools we utilize today.
In this article:
- What was the Network Monitor Agent?
- Transition to Modern Monitoring Tools
- Was the Network Monitor Agent a Sniffer?
- The Importance of Network Monitoring Today
- Conclusion
- References
1. What was the Network Monitor Agent?
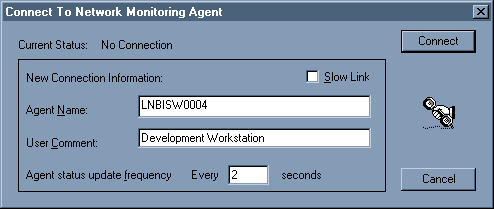
Network Monitor Agent was a Microsoft Windows NT service that allowed a computer to capture all traffic on the local network segment, which it can then collect centrally and display on a computer running Network Monitor. Network Monitor Agent also provides the Network Segment object for Performance Monitor.
Primarily a service within Microsoft Windows NT, Network Monitor Agent was designed to capture all local network segment traffic. This captured data could then be centralized and displayed on a computer equipped with the Network Monitor tool. Additionally, this agent extended its utility by offering the ‘Network Segment’ object for the Performance Monitor.
Key Features:
- Traffic Capture: The agent’s main role was to record all traffic data on the local network segment, which could be useful for analysis and troubleshooting.
- Performance Monitoring: By integrating with Performance Monitor, it could provide insights into network performance metrics.
- Compatibility: Beyond Windows NT, rudimentary versions of this service were available for Windows 95 and 98, making it versatile for its time.
Installing Network Monitor Agent on Windows NT
To install Network Monitor Agent in Windows NT, use the Network utility in Control Panel. Then use the Network Monitor Agent utility in Control Panel to configure, capture, and display packets to prevent unauthorized monitoring of your server. Installing Network Monitor Agent also enables the Network Segment object in Performance Monitor.
To start the Network Monitor Service from the command line use the command:
C:> net start nmagent2. Transition to Modern Monitoring Tools
As the intricacies of Windows environments and network architectures evolved, so did the tools designed to manage, monitor, and safeguard them. While the Network Monitor Agent was a fit for its era, the modern world, characterized by expansive and multifaceted networks, called for more sophisticated and integrated solutions.
The Inclusion of Resource Monitor
One of the most prominent tools integrated within modern Windows versions is the Resource Monitor. This utility provides an insightful overview of the computer’s network, memory, disk, and CPU activity. Within its network tab, users can view real-time data about network activity, covering various aspects like listening ports, network utilization rates, and active connections. This comprehensive functionality offers a glimpse into the heart of network operations, reflecting the capabilities once provided by the Network Monitor Agent but enhanced for today’s advanced systems.
Other Modern Alternatives:
- Wireshark: An industry benchmark for network protocol analysis, Wireshark allows for deep investigation into network traffic, revealing detailed information and analytics.
- Microsoft Message Analyzer: Evolving from the legacy of Network Monitor, this tool extends capabilities for capturing, displaying, and analyzing network data.
- SolarWinds Network Performance Monitor: Offering real-time views and intuitive dashboards, this tool is pivotal in overseeing optimal network performance in diverse settings.
3. Was the Network Monitor Agent a Sniffer?
Yes, the Network Monitor Agent can be categorized as a type of network sniffer. At its core, a network sniffer is a tool or utility that captures and analyzes packets of data flowing through a network. These sniffers are invaluable in understanding network operations, troubleshooting issues, and ensuring optimal performance. Network sniffers can be either hardware devices or software applications that intercept and log traffic passing over digital networks.
The Network Monitor Agent, in its essence, was designed to capture all traffic on the local network segment. By allowing for this comprehensive capture, it functioned similarly to what many would term as a “sniffer”. It enabled administrators and technicians to peek into the data being transmitted and received on a network, offering insights into traffic patterns, potential bottlenecks, and other pertinent networking dynamics.
4. The Importance of Network Monitoring Today
As our digital world continues to evolve at a rapid pace, the importance of network monitoring has only grown. Here’s why network monitoring remains crucial in today’s landscape:
- Complex Network Architectures: Modern networks are intricate, spanning across multiple devices, platforms, and even geographies. Monitoring tools ensure that all these interlinked components function seamlessly.
- Security Concerns: With increasing cyber threats, monitoring network traffic can help identify suspicious activities, potential breaches, or malware communications before they cause significant damage.
- Optimal Performance: As businesses rely more on digital operations, any network downtime or inefficiency can lead to significant financial and reputational losses. Monitoring helps preemptively identify and address potential issues.
- Cloud Integration: With many enterprises shifting to cloud infrastructures, monitoring tools aid in overseeing these cloud interactions, ensuring data integrity and swift communications.
- IoT and Edge Computing: The proliferation of Internet of Things (IoT) devices and the move towards edge computing means there are more endpoints than ever to monitor, manage, and secure.
- Data-Driven Decisions: Network monitoring tools not only identify problems but also provide valuable data. This data can be harnessed to make informed decisions about network upgrades, capacity planning, and optimization strategies.
5. Conclusion
In conclusion, while the tools and technologies might have evolved from the days of the Network Monitor Agent, the underlying need for vigilant and effective network monitoring has remained a constant. As networks become the backbone of modern business operations and everyday life, ensuring their health and security is paramount.
From the singular focus of Account Domains to the expansive vista of Active Directory, Microsoft’s journey reflects the industry’s broader shift towards complexity, flexibility, and scalability. Understanding this transition is key to appreciating the nuances of account and resource management in today’s Windows environments.