It’s time to talk about Security Assertion Markup Language (SAML). Welcome to the exciting realm of network security and access management!
In today’s digital landscape, where the online world intertwines with our daily lives, ensuring secure and streamlined access to various services has become paramount. Imagine a world where you can seamlessly hop from one system to another, without the hassle of remembering multiple usernames and passwords. Sounds like a dream, right? Well, hold onto your seats because we’re about to dive into the captivating world of Security Assertion Markup Language, better known as SAML.
Picture this: You’re a user in a vast digital universe, navigating through a multitude of systems, each demanding its own set of credentials. Logging in here, logging in there – it feels like an endless labyrinth of passwords and usernames. But fear not, for SAML is here to liberate you from this chaos and empower your digital journey with a touch of enchantment.
In this article:
- What is SAML?
- SAML Architecture
- SAML protocol
- SAML Assertions
- Single Sign-On (SSO)
- Federated Identity Management
- Is Google login an example of SAML?
- References
SAML, the secret ingredient to frictionless access, brings forth the magic of Single Sign-On (SSO) and Federated Identity Management. It’s a captivating tale of collaboration between identity providers and service providers, weaving together a seamless fabric of trust and convenience. With “Security Assertion Markup Language” as your guide, you can bid farewell to the shackles of remembering countless login credentials and embark on a journey where accessing various systems is as effortless as a wave of a wand.
But what exactly is SAML, you may wonder?
Think of it as a powerful enchantress, armed with XML-based sorcery, facilitating the secure exchange of authentication and authorization information. It’s the language spoken by identity providers and service providers, enabling them to share secrets in the form of digitally signed XML documents called SAML assertions. These magical assertions contain all the necessary information to unlock the gates of access, providing a golden ticket to authenticated users.
In this mesmerizing journey into the heart of SAML, we’ll unravel the mysteries behind its architecture, discover the roles of its enchanting entities – the Identity Provider (IdP) and Service Provider (SP), and witness the spellbinding SAML protocol in action. Brace yourselves for an adventure filled with trust, authentication, and seamless access like never before.
So, grab your wands, fasten your seatbelts, and join us as we embark on a thrilling exploration of SAML’s power to revolutionize the way we access services in the digital realm. Get ready to unlock the door to frictionless access, leaving behind the hassle of multiple credentials and stepping into a world where SAML reigns supreme. Welcome to the enchanting world of SAML – the key to unlocking seamless access!
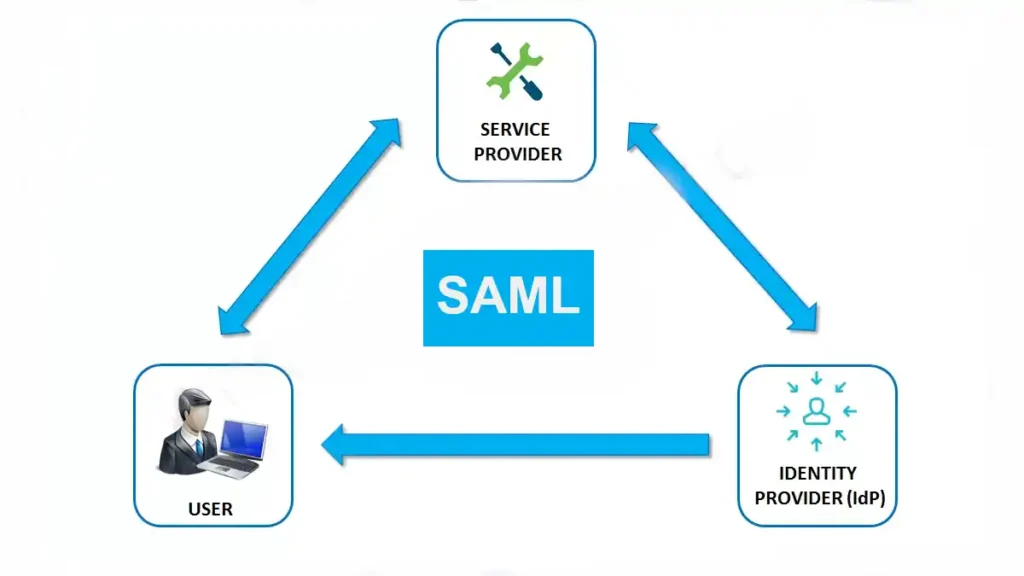
SAML Architecture
It’s time to unlock the gates to SAML’s architectural wonders. Brace yourselves for a journey into the heart of SAML’s enchanting realm, where trust and seamless access intertwine.
As we embark on this adventure, imagine yourself standing at the threshold of a grand palace, its architecture mirroring the intricate dance of security and convenience. This palace represents the foundation upon which Security Assertion Markup Language weaves its spellbinding charm. Let’s take a closer look at its magnificent architecture and the key players who breathe life into its magical structure.
The SAML architecture is like a symphony, with three harmonious entities working in tandem to orchestrate the dance of secure access: the Identity Provider (IdP), the Service Provider (SP), and our trusted companion, the User. Together, they form the backbone of SAML’s captivating tale.
Identity Provider (IdP)
Ah, the mystical Identity Provider, the guardian of authentication and the keeper of secrets. Picture the IdP as a wise old wizard, entrusted with the responsibility of verifying a user’s identity. When our intrepid user seeks access to a service, they first encounter the IdP, who carefully scrutinizes their credentials, harnessing the power of spells like multi-factor authentication to ensure their authenticity. Once satisfied, the IdP works its magic, conjuring up a sacred artifact known as the SAML assertion – a digital proof of the user’s identity and attributes.
Service Provider (SP)
Meet the Service Provider, a gracious host welcoming users into its realm of services and resources. The SP is like a mystical realm, abundant with treasures and experiences tailored to the user’s needs. Armed with the SAML assertion, our user approaches the SP’s domain, eager to unlock its secrets. The SP, ever vigilant, examines the SAML assertion with great care, verifying its authenticity and extracting the user’s identity and attributes. In a grand display of trust, the SP grants the user access to its wonders, eliminating the need for repetitive authentication rituals.
User
You, dear reader, are the hero of our tale – the User. You navigate the vast digital landscape, seeking access to various services. With Security Assertion Markup Language as your ally, you stand at the crossroads of convenience and security. The SAML journey begins with your authentic self, venturing forth to the IdP, proving your identity, and acquiring the magical SAML assertion. Armed with this artifact, you approach the SP’s realm, where the doors swing open, granting you access to a world of services without the burden of multiple logins. SAML empowers you, the User, to traverse systems effortlessly, unlocking a realm where seamless access becomes reality.
Now that we’ve met the mystical entities of the SAML architecture, let’s peek behind the curtain and witness the spellbinding SAML protocol in action.
SAML protocol in action
In our previous chapters, we discovered the magical architecture that underpins SAML’s power to grant seamless access. Now, it’s time to witness the enchanting dance of the SAML protocol – where requests and responses entwine, forging a path of trust and secure access.
Imagine a grand ballroom, adorned with shimmering lights and filled with graceful dancers. This ballroom represents the stage upon which the SAML protocol performs its captivating choreography. So, let’s put on our dancing shoes and join the SAML protocol as it takes center stage, orchestrating the harmonious exchange of information between the Identity Provider (IdP) and the Service Provider (SP).
The Prelude
Our dance begins with a user seeking access to a service provided by the SP. The user approaches the SP’s realm, ready to embark on a magical journey. However, before our user can enter, the SP gracefully extends a hand and presents a SAML request – a gentle plea for the user’s identity. This request contains vital information about the desired service and acts as a key to unlock the doors of access.
The Entrancing Response
The IdP, standing across the ballroom, receives the SP’s request with a knowing smile. With a wave of its wand, the IdP conjures up a bewitching response – the SAML response. Within this response lies the coveted SAML assertion, brimming with the user’s identity and attributes. The IdP signs this mystical artifact, ensuring its integrity and authenticity. As the response gracefully glides across the ballroom, it carries with it the promise of trust and access.
The Dance of Trust
The SP eagerly awaits the arrival of the SAML response, eyes gleaming with anticipation. As it receives the response, the SP scrutinizes the signature, validating its authenticity and integrity. With a graceful flourish, the SP unveils the user’s identity, extracting the essence from the SAML assertion. In this mesmerizing moment, trust is established, and the doors to the SP’s realm swing open wide, welcoming the user with open arms.
The Finale
With the SAML protocol’s dance complete, our user triumphantly enters the SP’s realm, surrounded by a chorus of seamless access and convenience. No longer burdened by multiple logins and endless passwords, our user is free to explore the realm’s treasures, tapping into the services and resources that await their arrival.
As we witness the Security Assertion Markup Language protocol’s dance unfold, we can’t help but marvel at its elegance and power. It’s a dance that transcends boundaries, allowing users to seamlessly access services across realms and domains. The SAML protocol weaves a tapestry of trust and secure access, ensuring that our digital journeys are not hindered by the chains of authentication.
But dear readers, our SAML journey is far from over. In our next chapter, we will embark on an exploration of SAML’s magical artifacts – the SAML assertions. These digital tokens hold the key to unlocking the user’s identity and attributes, paving the way for a world where access becomes a seamless, enchanting experience.
SAML Assertions
We have arrived at a pivotal chapter in our exploration of the enchanting Security Assertion Markup Language (SAML). Prepare to be spellbound as we unravel the secrets of SAML assertions – the mystical artifacts that hold the key to unlocking the user’s identity and attributes.
Imagine a treasure chest filled with shimmering jewels, each one representing a unique facet of the user’s identity. These jewels are the SAML assertions, powerful artifacts crafted by the Identity Provider (IdP) to vouch for the user’s authenticity. Let us delve into their captivating nature and witness the wonders they bestow upon our digital realm.
The Essence of Identity
SAML assertions are like mirrors that reflect the user’s true identity. They contain a wealth of information, capturing the user’s name, email address, group memberships, and other attributes relevant to accessing services. Just as a magical potion reveals the true form of an enchantress, SAML assertions reveal the essence of the user, enabling Service Providers (SPs) to make informed access control decisions.
The Seal of Authenticity
To ensure the integrity and trustworthiness of the SAML assertions, the IdP graces them with a digital signature. This signature acts as a seal of authenticity, guaranteeing that the assertions have not been tampered with and originate from a trusted source. Like an ancient artifact imbued with the power of protection, the digital signature shields the SAML assertions from the forces of deception.
The Web of Trust
SAML assertions thrive in a web of trust, where IdPs and SPs establish mutual confidence. Just as wizards exchange ancient spells to solidify alliances, IdPs and SPs share cryptographic keys and certificates to forge trust relationships. When an SP receives a SAML assertion, it verifies the digital signature using the shared trust, ensuring that the user’s identity remains untainted and access remains secure.
The Enchanting Attributes
Within the depths of SAML assertions lie a tapestry of attributes, like threads woven together to form a grand design. These attributes hold the key to accessing the realm of services, granting the user permissions and privileges tailored to their needs. Whether it’s the role they play, their organizational affiliations, or their preferences, SAML assertions unlock a world of personalized experiences.
The Passport to Access
Just as a traveler presents their passport at the border, the user presents the SAML assertion as their ticket to accessing services. When the user arrives at the SP’s domain, they present their SAML assertion, a testament to their verified identity. The SP, in turn, verifies the assertion, ensuring that it carries the mark of trust and grants access to the realm’s treasures.
But dear adventurers, our journey through SAML’s realm is not yet complete. In our next chapter, we will explore the wondrous realms of Single Sign-On (SSO) and federated identity management, where SAML assertions work their magic to create a seamless and unified access experience across systems and domains.
Single Sign-On (SSO)
Single Sign-On (SSO) in the realm of Security Assertion Markup Language (SAML) is a magical enchantment that simplifies the authentication process and grants users access to multiple services with a single login. It is the key that unlocks the doors to a realm of convenience and efficiency.
In the world of SAML, SSO allows users to authenticate themselves once with an Identity Provider (IdP) and then seamlessly access multiple Service Providers (SPs) without the need for additional logins. It eliminates the frustration of remembering and managing numerous usernames and passwords for different services.
What is Federated Identity Management in SAML?
Federated Identity Management in the realm of Security Assertion Markup Language (SAML) is a majestic alliance that brings together Identity Providers (IdPs) and Service Providers (SPs) to establish a web of trust and enable seamless authentication and access across multiple realms. It is a harmonious dance of collaboration and shared responsibility that enhances security and simplifies user experiences.
In the realm of SAML, federated identity management acts as a bridge between different domains and systems, enabling users to navigate effortlessly while their identities remain protected.
Is Google Login an example of SAML?
No, Google Login does not use SAML as its primary authentication mechanism. Google utilizes its own authentication protocol called OAuth, which is specifically designed for granting access to Google services and APIs. OAuth allows users to authorize third-party applications to access their Google account information without sharing their actual login credentials.
However, Google does support SAML as a means of authentication for enterprise customers using its Google Workspace (formerly G Suite) suite of productivity tools. In this scenario, organizations can set up SAML-based Single Sign-On (SSO) with their Google Workspace accounts. When users log in to their organization’s identity provider, the SAML protocol is used to authenticate them, and upon successful verification, they are granted access to Google Workspace services without needing to provide separate credentials.
So, while Google login for individual Google services relies on OAuth, the usage of SAML comes into play when integrating Google Workspace with enterprise identity systems for SSO purposes.
References
The SAML specifications are defined and documented in a series of RFCs that provide a standardized framework for implementing the SAML protocol.
- RFC 8414: “OAuth 2.0 Authorization Server Metadata”
- RFC 7522: “Security Assertion Markup Language (SAML) 2.0 Profile for OAuth 2.0 Client Authentication and Authorization Grants”
- RFC 7523: “JSON Web Token (JWT) Profile for OAuth 2.0 Client Authentication and Authorization Grants”
- RFC 7644: “System for Cross-domain Identity Management: Protocol”