In today’s connected world, understanding how to diagnose network issues is invaluable. One of the most basic yet powerful tools in the toolbox of network administrators, tech-savvy individuals, and even average computer users is the Ping command. But what exactly is Ping, and how does it function? In this comprehensive article, we’ll delve into what Ping is, break down how it operates, explore various command options, and provide practical examples. Moreover, we’ll investigate potential security issues associated with using Ping. Stick around to unveil all the facets of this indispensable utility.
Jump to:
- What is Ping?
- How It Works
- Ping Command Options
- Ping Command Examples
- Ping Security issues
- Alternatives to the Ping Tool
1. What is Ping?
PING stands for Packet Internet Groper, a TCP/IP utility that verifies the integrity of a network connection with a host on a TCP/IP network. The ping command is one of the first commands to use to troubleshoot communication problems on a TCP/IP network.
2. How It Works
At the command prompt, type ping followed by either the IP address or the fully qualified domain name (if the Domain Name System is implemented) of the host for which you want to test networking connectivity. One or multiple Internet Control Message Protocol (ICMP) echo packets are sent to the host, and if connectivity is working, an equal number of echo replies are received. The replies show the packet size in bytes, response time in milliseconds, and Time to Live (TTL) of the echo reply.
The TTL is decremented for each hop along the way and indicates the number of routers (hops) passed through along the network path.
The usual procedure for using ping to troubleshoot a TCP/IP network follows:
- Verify that TCP/IP is installed and running by pinging the local loopback address using ping 127.0.0.1.
- Ping your own IP address and host name.
- Ping the IP address of the default gateway for your local network.
- Ping the IP address of a host on a remote network.
If these steps produce the expected results, TCP/IP is installed and running on your network.
This command is available only if the Internet Protocol (TCP/IP) protocol is installed as a component in the properties of a network adapter in Network Connections.
Ping /?
For advanced syntax features, simply type ping instead of ping /?.+
3. Ping Command Options
| Item | Explanation |
| -t | Using this option will ping the target until you force it to stop by using Ctrl-C. |
| -a | This ping command option will resolve, if possible, the host name of an IP address target. |
| -n count | This option sets the number of ICMP Echo Requests to send, from 1 to 4294967295. The ping command will send 4 by default if -n isn’t used. |
| -l size | Use this option to set the size, in bytes, of the echo request packet from 32 to 65,527. The ping command will send a 32-byte echo request if you don’t use the -l option. |
| -f | Use this ping command option to prevent ICMP Echo Requests from being fragmented by routers between you and the target. The -f option is most often used to troubleshoot Path Maximum Transmission Unit (PMTU) issues. |
| -i TTL | This option sets the Time to Live (TTL) value, the maximum of which is 255. |
| -v TOS | This option allows you to set a Type of Service (TOS) value. Beginning in Windows 7, this option no longer functions but still exists for compatibility reasons. |
| -r count | Use this ping command option to specify the number of hops between your computer and the target computer or device that you’d like to be recorded and displayed. The maximum value for count is 9, so use the tracert command instead if you’re interested in viewing all the hops between two devices. |
| -s count | Use this option to report the time, in Internet Timestamp format, that each echo request is received and echo reply is sent. The maximum value for count is 4, meaning that only the first four hops can be time stamped. |
| -w timeout | Specifying a timeout value when executing the ping command adjusts the amount of time, in milliseconds, that ping waits for each reply. If you don’t use the -w option, the default timeout value of 4000 is used, which is 4 seconds. |
| -R | This option tells the ping command to trace the round trip path. |
| -S srcaddr | Use this option to specify the source address. |
| -p | Use this switch to ping a Hyper-V Network Virtualization provider address. |
| -4 | This forces the ping command to use IPv4 only but is only necessary if target is a hostname and not an IP address. |
| -6 | This forces the ping command to use IPv6 only but as with the -4 option, is only necessary when pinging a hostname. |
| target | This is the destination you wish to ping, either an IP address or a hostname. |
| /? | Use the help switch with the ping command to show detailed help about the command’s several options. |
Additional information about PING options: The -f, -v, -r, -s, -j, and -k options work when pinging IPv4 addresses only. The -R and -S options only work with IPv6.
4. Ping Command Examples
ping -n 7 -l 2000 www.google.com
In this example, the ping command is used to ping the host name www.google.com. The -n option tells the ping command to send 7 ICMP Echo Requests instead of the default of 4, and the -l option sets the packet size for each request to 1000 bytes instead of the default of 32 bytes.
The result displayed in the Command Prompt window will look something like this:
Reply from 216.58.211.36: bytes=1000 time=21ms TTL=55 Reply from 216.58.211.36: bytes=1000 time=20ms TTL=55 Reply from 216.58.211.36: bytes=1000 time=20ms TTL=55 Reply from 216.58.211.36: bytes=1000 time=21ms TTL=55 Reply from 216.58.211.36: bytes=1000 time=20ms TTL=55 Reply from 216.58.211.36: bytes=1000 time=20ms TTL=55 Reply from 216.58.211.36: bytes=1000 time=21ms TTL=55 Ping statistics for 216.58.211.36: Packets: Sent = 7, Received = 7, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 29ms, Maximum = 31ms, Average = 30ms
The 0% loss reported under Ping statistics for 74.217.1.142 explains that each ICMP Echo Request message sent to www.google.com was returned. This means that, as far as this network connection goes, it can communicate with Google’s website just fine.
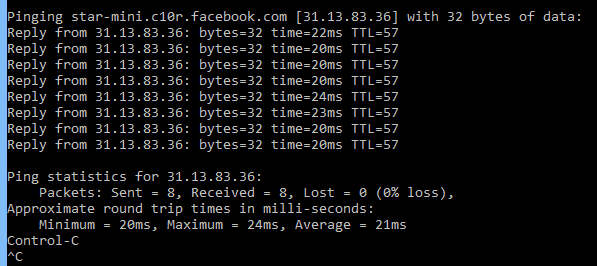
ping -t www.facebook.com
In this example, the ping command is used to ping the host name www.facebook.com with the -t option. This option will keep the ping active until Control-C is pressed to stop it.
Reply from 31.13.83.36: bytes=32 time=22ms TTL=57 Reply from 31.13.83.36: bytes=32 time=20ms TTL=57 Reply from 31.13.83.36: bytes=32 time=20ms TTL=57 Reply from 31.13.83.36: bytes=32 time=20ms TTL=57 Reply from 31.13.83.36: bytes=32 time=24ms TTL=57 Reply from 31.13.83.36: bytes=32 time=23ms TTL=57 Reply from 31.13.83.36: bytes=32 time=20ms TTL=57 Reply from 31.13.83.36: bytes=32 time=20ms TTL=57 Ping statistics for 31.13.83.36: Packets: Sent = 8, Received = 8, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 20ms, Maximum = 24ms, Average = 21ms Control-C ^C
5. Ping Security issues
To conduct a denial-of-service attack, an attacker may send ping requests as fast as possible, possibly overwhelming the victim with ICMP echo requests. This technique is called a ping flood.
Ping requests to multiple addresses, ping sweeps, may be used to obtain a list of all hosts on a network.
Troubleshoot with Ping
If you can ping a host’s IP address but not its fully qualified domain name (FQDN), you probably have a name resolution problem. Check your Domain Name System (DNS) configuration and make sure that the DNS server is running, or check your Hosts file if it is implemented.
6. Alternatives to the Ping Tool
While the Ping command is a versatile tool for troubleshooting and assessing network connectivity, it’s not the only game in town. Let’s take a moment to explore some alternatives that offer different features or capabilities:
Traceroute/tracert
This utility maps out the various hops a packet takes as it travels across a network. Unlike Ping, which only tells you if a destination is reachable, Traceroute shows you the path a packet takes to get there.
MTR (My TraceRoute)
MTR combines the functionality of Ping and Traceroute, offering real-time data about the route that packets take through a network. It continuously pings each hop along the route, providing a detailed picture of network performance.
Nmap (Network Mapper)
While Nmap’s primary function is not network pinging, it does include capabilities to test network connectivity. Plus, Nmap offers a wide range of network discovery and security auditing features.
Telnet
An older utility, Telnet can check the connectivity to a specific port on a server. This is useful if you’re trying to determine if a service (like a web server or email server) is up and running.
Arping
Arping is like the Ping command, but it operates at the ARP (Address Resolution Protocol) level instead of using ICMP (Internet Control Message Protocol). It’s beneficial for local network diagnostics.
Netcat
Netcat, also known as the “Swiss Army knife of networking,” offers an extensive range of functionalities including port scanning, transferring files, and of course, network testing.
Each of these tools has its own set of capabilities, advantages, and disadvantages, making them more or less suitable for specific scenarios. Depending on your needs, you might find one of these alternatives to be more useful for your diagnostic or network management tasks.