Secure Hypertext Transfer Protocol (S-HTTP) represents a significant advancement in the realm of internet security protocols, focusing on the encryption of HTTP traffic. It is designed to ensure secure and private communication over the World Wide Web. In this comprehensive guide, we delve into the intricacies of S-HTTP, from its foundational principles to its practical applications.
This article aims to provide a detailed understanding of S-HTTP, including its creation, evolution, current relevance, and how it stands in comparison with its more well-known counterpart, HTTPS.
In this article:
- What is S-HTTP?
- The Creation of S-HTTP
- How S-HTTP Works
- S-HTTP vs. HTTPS: Understanding the Differences
- Current Relevance of S-HTTP
- Challenges and Limitations of S-HTTP
- Future Outlook and Evolution of Secure Web Protocols
- References

1. What is S-HTTP (Secure Hypertext Transfer Protocol)?
Secure Hypertext Transfer Protocol (S-HTTP) is a protocol used for encrypting HTTP traffic, enhancing the security of data as it travels across the World Wide Web. Essentially, S-HTTP is designed to secure individual messages transmitted between clients and servers, differentiating itself from other security protocols by its granularity and message-oriented approach.
Basic Functionality and Principles
The primary functionality of S-HTTP is to provide end-to-end encryption of web communications. It achieves this by encrypting the data before transmission and decrypting it upon receipt. This process ensures confidentiality and protects against eavesdropping and tampering. S-HTTP supports various encryption algorithms, enabling flexible security arrangements based on the needs of the communication parties. Furthermore, it provides options for authentication, ensuring that both sender and receiver can verify each other’s identity, adding an additional layer of security to web interactions.
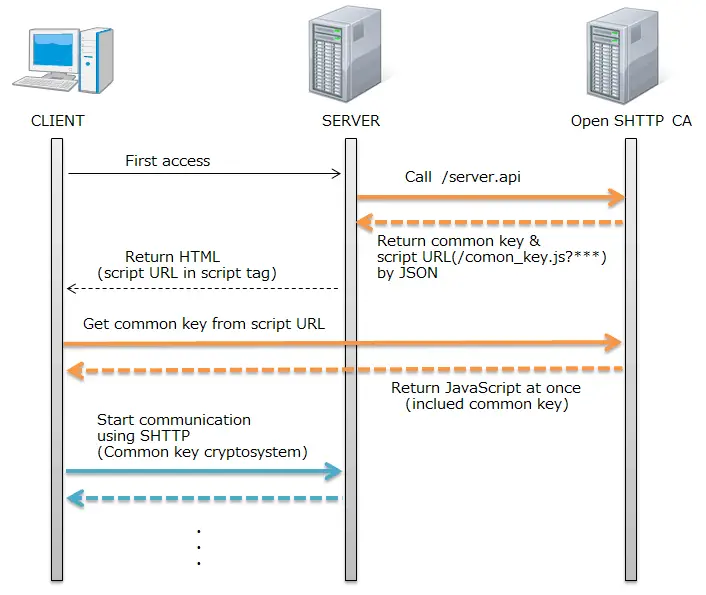
S-HTTP is also a server software
The Secure Hypertext Transfer Protocol is not as widely implemented as Secure Sockets Layer (SSL), which is independent of protocol and works with HTTP, Simple Mail Transfer Protocol (SMTP), Network News Transfer Protocol (NNTP), and other Internet protocols.
S-HTTP is also the name given to World Wide Web (WWW) server software that implements the S-HTTP protocol. This software was developed by Enterprise Integrations Technologies (EIT), the National Center for Supercomputing Applications (NCSA), and RSA Security.
2. The Creation of S-HTTP
Historical Context and Origin
S-HTTP was developed in the early 1990s, a time when the internet was rapidly expanding, and the need for secure communication methods was becoming increasingly apparent. The protocol was developed to address the lack of inherent security in the HTTP protocol, which is the foundational technology for data communication on the World Wide Web.
Key Contributors and Development Timeline
The development of S-HTTP was primarily led by R. T. Fielding and J. C. Mogul. Their work was instrumental in the early stages of defining and standardizing the protocol. The key milestones in the development of S-HTTP include:
- Initial Proposal: The concept of Secure Hypertext Transfer Protocol was proposed to address the growing concerns over web security and privacy.
- Collaboration and Standardization: Collaborative efforts among various internet security experts and organizations led to the refinement and standardization of the protocol.
- RFC Publication: The formal documentation of S-HTTP, known as RFC 2660, was published in 1999, detailing the specifications and use cases of the protocol. (see the references section)
The creation of S-HTTP marked a significant step in the evolution of web security, laying the groundwork for future developments in secure web communication.
3. How S-HTTP Works
Technical Mechanism and Encryption Process
S-HTTP operates by encrypting individual HTTP messages, unlike other protocols that encrypt the entire communication session. This mechanism provides flexibility in securing specific parts of the data being transmitted. Each message, whether it’s a request from the client or a response from the server, is encrypted independently.
The encryption process involves several key steps:
- Encryption Initiation: When a message is ready for transmission, S-HTTP initiates encryption using a selected algorithm.
- Key Exchange: S-HTTP supports various key exchange mechanisms. These keys are used to encrypt and decrypt messages at both ends.
- Data Encryption: The actual data in the HTTP message is encrypted using the agreed-upon encryption standards, rendering it unreadable to unauthorized parties.
- Transmission and Decryption: Once the encrypted message reaches its destination, it is decrypted using the corresponding decryption key.
Setting Up and Configuring S-HTTP
To set up S-HTTP:
- Server and Client Configuration: Both the server and client must support S-HTTP. This involves configuring the web server and client applications to handle S-HTTP requests and responses.
- Certificate Management: Obtain and install digital certificates to facilitate authentication and key exchange.
- Selecting Encryption Algorithms: Choose suitable encryption algorithms based on the required level of security and the capabilities of the server and client.
4. S-HTTP vs. HTTPS: Understanding the Differences
Comparative Analysis of Protocols
While both S-HTTP and HTTPS are designed to secure HTTP communications, they differ fundamentally in their approach:
- Encryption Scope: Secure-HTTP encrypts individual messages, whereas HTTPS encrypts the entire communication session.
- Flexibility: SHTTP offers more flexibility in terms of what parts of the communication are encrypted. HTTPS, on the other hand, provides a uniform layer of encryption over all data exchanged.
- Compatibility: The Secure Hypertext Transfer Protocol can coexist with regular HTTP on a single server, while HTTPS typically requires a dedicated port.
Use Cases and Suitability
- S-HTTP: Best suited for scenarios where selective encryption of messages is needed, such as in applications that only require certain parts of the communication to be secured.
- HTTPS: Ideal for general web browsing and transactions where uniform security is required for all data exchanges, like in e-commerce or online banking.
Understanding these differences is crucial for selecting the right protocol based on specific security requirements and the nature of the data being transmitted.
5. Current Relevance of S-HTTP
Is S-HTTP Still Used Today?
S-HTTP, despite its initial promise, has seen limited adoption in modern web communications. The protocol, while innovative, has been overshadowed by the widespread acceptance and implementation of HTTPS. Today, S-HTTP is rarely used in standard web applications or by major web browsers, making it more of a historical footnote in the evolution of secure web communication protocols.
Modern Implementations and Legacy
Although S-HTTP is not prevalent in current web applications, its legacy persists in the form of ideas and methodologies that have influenced modern encryption techniques. The concept of selectively encrypting web messages has been integrated into other technologies and protocols, albeit in different forms. S-HTTP’s emphasis on flexible encryption and message-specific security remains a relevant concept in the design of secure communication systems.
6. Challenges and Limitations of S-HTTP
Technical Constraints
One of the major technical challenges facing S-HTTP was the complexity of its implementation. The protocol’s message-specific encryption approach required more processing power and presented challenges in efficiently managing encryption keys. Moreover, the necessity for both client and server to support S-HTTP added to the complexity, making it less attractive compared to more straightforward alternatives like HTTPS.
Adoption and Compatibility Issues
S-HTTP’s adoption was hindered by several factors:
- Limited Browser and Server Support: Many web browsers and servers did not adopt S-HTTP, favoring the more straightforward HTTPS protocol.
- Compatibility with Web Infrastructure: The existing web infrastructure, including caching mechanisms and proxy servers, was optimized for HTTP and HTTPS, leading to compatibility issues with S-HTTP.
- Emergence of HTTPS as a Standard: The rapid adoption of HTTPS as the de facto standard for secure web communication further marginalized S-HTTP, as developers and organizations preferred the more universally accepted protocol.
These challenges limited the widespread adoption of S-HTTP, relegating it to a niche role in the history of web security protocols.
7. Future Outlook and Evolution of Secure Web Protocols
Emerging Trends in Web Security
The future of web security is likely to be shaped by several emerging trends:
- Advanced Encryption Techniques: The development of more sophisticated encryption methods to counteract evolving cyber threats.
- Quantum Computing: The advent of quantum computing poses new challenges to current encryption standards, driving the need for quantum-resistant protocols.
- AI and Machine Learning: The integration of AI and machine learning for predictive threat detection and automated security responses.
- Increased Focus on End-User Privacy: Growing concerns over data privacy are prompting the development of protocols that enhance user anonymity and data protection.
Predictions for the Future of Secure HTTP and Related Technologies
Finally, while S-HTTP itself may not see a revival, its principles could influence future protocols:
- Selective Encryption: The concept of selective encryption, central to Secure-HTTP, may find relevance in specialized applications requiring flexible security measures.
- Incorporation into Hybrid Protocols: Elements of the Secure Hypertext Transfer Protocol might be integrated into new or existing protocols to enhance their security capabilities, especially in environments where message-level encryption is crucial.
8. References
Books:
- “Network Security Essentials” by William Stallings – A comprehensive guide covering various aspects of web and network security.
- “SSL and TLS: Designing and Building Secure Systems” by Eric Rescorla – Provides insights into the design and implementation of secure web protocols.
Relevant RFCs: