Server Message Block (SMB) is more than just a protocol for sharing files and printers across Windows networks. It is a fundamental technology that underpins network communication, enabling a multitude of applications to interact seamlessly over a network. Originating from IBM and evolving through Microsoft’s stewardship, SMB has grown from a simple file sharing mechanism to a complex, secure, and efficient protocol that supports the sophisticated needs of modern networked environments.
This article delves into the intricacies of SMB, offering insights into its workings, evolution, and pivotal role in contemporary computing.
Table of Contents:
- What is Server Message Block (SMB)?
- The Evolution of SMB: From IBM to SMB 3.1.1
- How Does SMB Work? Understanding the Protocol’s Mechanics
- SMB Protocol Dialects and Their Significance
- SMB vs. CIFS: Clarifying the Confusion
- SMB Security: From Vulnerabilities to Fortification
- Practical Applications of SMB in Modern Networks
- Comparing SMB and NFS: Choosing the Right Protocol
- Future Directions of SMB: Trends and Developments
- References

1. What is Server Message Block?
Server Message Block, also known as SMB, is a high-level file-sharing protocol jointly developed by Microsoft, IBM, and Intel for passing data between computers on a network. Microsoft Windows and OS/2 use Server Message Block (SMB). Many UNIX operating systems also support it.
SMB operates as an application-layer protocol, meaning it enables applications on a computer to read and write to files and request services from server programs in a computer network. The protocol not only facilitates file sharing but also supports complex operations like network browsing and printer access, making it a versatile tool in network administration and operations.
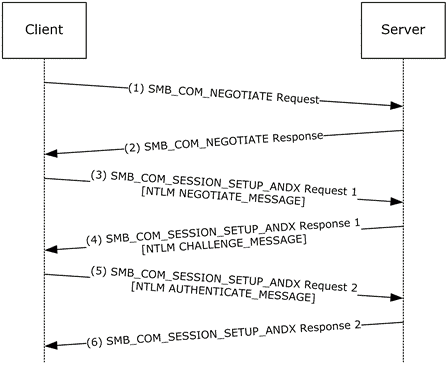
2. The Evolution of SMB: From IBM to SMB 3.1.1
The journey of SMB began in 1983, developed by Barry A. Feigenbaum at IBM, with the intent of turning standalone computers into connected workstations capable of sharing resources efficiently. Microsoft adopted SMB in the early 1990s, marking the beginning of a series of significant enhancements that would transform SMB into a robust, secure, and efficient protocol. The evolution of SMB can be segmented into its major versions:
- SMB 1.0 (1996): Introduced by Microsoft, laying the groundwork for network file and printer sharing.
- SMB 2.0 (2006): A major overhaul that improved performance, reduced complexity, and enhanced security.
- SMB 3.0 (2012): Integrated in Windows Server 2012, it introduced features like end-to-end encryption, improving security and efficiency.
- SMB 3.1.1 (2015): The latest version, further refining security features to protect against modern cybersecurity threats.
This evolution reflects SMB’s adaptation to the changing landscape of network computing, balancing ease of use with the need for secure, efficient communication.
3. How Does SMB Work? Understanding the Protocol’s Mechanics
At its core, Server Message Block (SMB) functions as a request-response or client-server protocol. This means that a client (user) sends requests to a server (networked device) to perform operations like opening, reading, writing, or closing files. SMB operates atop the session layer in the OSI model, enabling it to rely on lower-level protocols for the actual network communication, typically TCP/IP in modern networks.
Request-Response Mechanism
When a user attempts to access a file on a remote server, the SMB client on the user’s computer sends a request to the SMB server hosting the file. This request specifies the desired operation, such as reading a file. The server then processes this request, accesses the file, and sends the data back to the client, or performs the requested operation and sends a response indicating the success or failure of the operation.
Packet Structure
SMB communications are encapsulated in packets that include a header and a payload. The header contains information about the message, including the type of request or response, while the payload carries the data pertinent to the request, such as file contents or directory listings.
Session Management
SMB manages sessions between clients and servers, ensuring a secure and persistent connection for the duration of the interaction. This involves authentication processes to verify the identity of the users and the establishment of a secure channel for communication.
4. SMB Protocol Dialects and Their Significance
SMB protocol dialects refer to the different versions or variants of the SMB protocol that have been developed over the years. Each dialect represents an evolution in the capabilities, performance, and security of SMB, responding to the changing needs of networked environments.
Major SMB Dialects
- SMB 1.0: The original version, which laid the foundation for file and printer sharing but is considered less secure and efficient by modern standards.
- SMB 2.0: Introduced significant improvements in performance (reduced chattiness, increased scalability) and security over SMB 1.0.
- SMB 2.1: Added minor enhancements, including support for symbolic links.
- SMB 3.0: A major update that introduced advanced features like end-to-end encryption, improved performance through multichannel support, and enhanced fault tolerance.
- SMB 3.1.1: The latest dialect, offering even stronger security through pre-authentication integrity to prevent man-in-the-middle attacks.
Significance of Dialects
The evolution of SMB dialects highlights the protocol’s adaptability to the requirements of network security, performance, and functionality. Each dialect builds upon the strengths of its predecessors while addressing their limitations, reflecting the protocol’s ongoing refinement in response to technological advancements and cybersecurity threats.
For instance, the shift from SMB 1.0 to SMB 2.0 and beyond significantly reduced the protocol’s chattiness—a measure of the number of commands and responses exchanged—resulting in faster data transfers and reduced network congestion. The introduction of encryption in SMB 3.0 marked a pivotal advancement in securing data in transit, addressing vulnerabilities that had been exploited in ransomware attacks.
5. SMB vs. CIFS: Clarifying the Confusion
The terms Server Message Block (SMB) and Common Internet File System (CIFS) are often used interchangeably, leading to confusion about their distinctions and similarities. Understanding the relationship between SMB and CIFS is crucial for comprehending the evolution of network file sharing protocols and their application in modern computing environments.
SMB: The Foundation
SMB, as previously discussed, is a protocol developed for network file and printer sharing. It allows computers to read and write files over a network, request services, and communicate with each other in a client-server model. SMB has evolved through various versions, improving in security, efficiency, and functionality over time.
CIFS: A Version of SMB
CIFS is essentially a version of SMB. Specifically, it refers to the version of SMB that was popularized and standardized by Microsoft in the 1990s. CIFS was designed to provide a more efficient and robust protocol for network file sharing over the Internet. While it introduced improvements and extensions to the original SMB protocol, it is essentially SMB under a different name, primarily focusing on Internet-based file sharing.
Key Differences and Similarities
- Compatibility: CIFS is a dialect of SMB, specifically SMB1.0. This means that while all CIFS communications are SMB, not all SMB communications are CIFS.
- Performance: CIFS is known for being more verbose than newer versions of SMB, leading to higher protocol overhead and potentially slower performance over networks with high latency.
- Features: Newer versions of SMB (e.g., SMB 2.x, SMB 3.x) introduced significant enhancements not found in CIFS, including better performance, more efficient network utilization, and advanced security features like encryption.
Modern Usage
In today’s network environments, the use of CIFS is generally discouraged in favor of more modern SMB versions due to their improved security, efficiency, and compatibility with contemporary operating systems and network configurations.
6. SMB Security: From Vulnerabilities to Fortification
Security within the SMB protocol has been a major focus, especially in light of past vulnerabilities that have been exploited in widespread cyber attacks. Understanding these vulnerabilities and the measures taken to fortify SMB against such threats is essential for ensuring network security.
Historical Vulnerabilities
- WannaCry and Petya Ransomware: These notorious ransomware attacks exploited vulnerabilities in SMB 1.0, highlighting the dangers of outdated protocols and the importance of network security hygiene.
- Man-in-the-Middle (MitM) Attacks: Earlier versions of SMB were susceptible to MitM attacks, where attackers could intercept and manipulate data being transferred between clients and servers.
Security Enhancements in SMB
- End-to-End Encryption: Introduced in SMB 3.0, encryption ensures that data transferred over the network is secure and unreadable by unauthorized parties, significantly reducing the risk of data interception and tampering.
- Pre-Authentication Integrity: SMB 3.1.1 introduced pre-authentication integrity checks using SHA-512 hashing to protect against MitM attacks by ensuring that the integrity of the communication is maintained from start to finish.
- Secure Dialect Negotiation: This feature prevents downgrade attacks by ensuring that connections use the highest protocol version supported by both the client and server.
Best Practices for SMB Security
- Disable SMB 1.0: Given its known vulnerabilities, disabling SMB 1.0 on all networked devices is a critical step in securing network communications.
- Keep Systems Updated: Regularly updating operating systems and SMB implementations can protect against known vulnerabilities.
- Use SMB Signing and Encryption: Enabling these features can prevent unauthorized interception and manipulation of SMB data.
- Network Segmentation: Restricting SMB traffic to segmented parts of the network can limit the spread of any potential breaches.
7. Practical Applications of SMB in Modern Networks
Server Message Block (SMB) protocol finds its utility in a myriad of modern networking scenarios, underlining its versatility beyond simple file sharing. Its applications span across various domains, offering solutions that cater to efficiency, security, and seamless connectivity in networked environments.
File Sharing and Access
At its core, SMB facilitates the sharing of files across different devices on a network. This allows for easy access, editing, and management of files stored on remote servers, making it indispensable in environments where collaboration and data accessibility are key, such as in corporate networks or educational institutions.
Printer Sharing
SMB also simplifies the process of printer sharing, enabling multiple users to access a single printer over a network. This eliminates the need for direct physical connections to printers, optimizing resources and reducing costs.
Interoperability Between Operating Systems
With its support across Windows, Linux (via Samba), and macOS, SMB ensures interoperability between different operating systems. This cross-platform support is crucial for mixed-OS environments, facilitating seamless file and resource sharing regardless of the underlying operating system.
Remote Application Access
SMB is used in scenarios where applications on a client computer need to access data on servers as if it were locally available. This capability is particularly useful for database and customer relationship management (CRM) applications that operate over networks.
Cloud Integration and Distributed File Systems
Modern implementations of SMB support cloud integration and distributed file systems, allowing businesses to extend their storage capabilities and enhance data redundancy and accessibility. SMB’s role in cloud services underscores its adaptability to evolving technology landscapes.
8. Comparing SMB and NFS: Choosing the Right Protocol
While SMB and Network File System (NFS) both serve the primary purpose of enabling file sharing over networks, they cater to different use cases and environments, making the choice between them dependent on specific requirements.
Protocol Design
- SMB: Designed primarily for Windows environments, SMB supports a wide range of features beyond file sharing, including printer sharing, complex file permissions, and more. It is optimized for interoperability across different operating systems.
- NFS: Developed for UNIX systems, NFS offers a simpler design focused on file sharing, with a strong emphasis on performance and compatibility within UNIX and Linux environments.
Performance and Efficiency
- NFS is often cited for better performance in Linux or UNIX environments, particularly because of its simpler protocol and efficient handling of file operations.
- SMB, with its more complex protocol, may introduce additional overhead but offers significant performance improvements in its latest versions, especially when integrated into Windows environments.
Security
- SMB has evolved to include robust security features like end-to-end encryption and pre-authentication integrity checks, making it well-suited for secure data transfers.
- NFS has also incorporated security improvements, but its security model is fundamentally different, relying on network security practices and UNIX file permissions.
Use Cases
- SMB is preferred in mixed-OS environments, particularly where Windows is prevalent, and when advanced features like printer sharing or integrated Windows authentication are required.
- NFS shines in UNIX/Linux environments, offering high performance and efficiency, making it ideal for applications that require high-speed access to large volumes of data.
10. References
- Books:
- “Implementing CIFS: The Common Internet File System” by Christopher R. Hertel
- “Windows Server 2019 Inside Out” by Orin Thomas
- RFCs:
- Online Resources: