Subnet Mask is a 32-bit number that is used to partition IP addresses into a network ID and a host ID (network and host bits). Subnet masks are used by TCP/IP services and applications to determine whether a given IP address on an internetwork is a local network address or a remote network address.
This article delves into the core fundamentals of subnet masks, covering their role, structure, and application in computer networking.
In this article:
- Understanding the Basics
- Subnet Mask Structure
- Creating Subnets
- Subnet Calculations
- Working with Subnet Tools
- Common Errors and Troubleshooting
- Subnetting in Cloud and Virtual Networks
- Future Trends
- Summary and Key Takeaways
- References
1. Understanding the Basics
Definitions
A subnet mask is essentially a 32-bit number that classifies IP addresses into two components: the network portion and the host portion. Comprising a series of ones followed by zeros, it plays a pivotal role in IP routing.
Role in Networking
In networking, the subnet mask serves to partition an IP network into smaller, more manageable pieces. Furthermore, it assists routers in identifying the destination subnet of a given IP address. Consequently, the router directs traffic optimally.
IPv4 vs. IPv6
IPv4 and IPv6 both utilize subnet masks, albeit differently. IPv4 employs a 32-bit address, whereas IPv6 leverages a 128-bit address. IPv6 generally uses CIDR (Classless Inter-Domain Routing) notation for subnets, eschewing the traditional dotted-decimal format.
2. Subnet Mask Structure
Subnet masks are represented as four-octet dotted-decimal numbers, just as IP addresses are, except that the most common values for an octet in a subnet mask are 0 and 255. In binary notation, decimal 0 represents the octet 00000000, and decimal 255 represents 11111111.
Bitwise Representation
A subnet mask consists of 32 binary digits, the first n of which are 1s and the remaining of which are 0s. When the subnet mask is logically ANDed with a 32-bit IP address of a TCP/IP host, the result is the network ID of the host – the portion of the host’s IP address that identifies which network the host is on. When the inverse of the subnet mask (for example, NOT mask) is logically ANDed with the IP address of the host, the result is the host ID of the host – the portion of the host’s IP address that uniquely identifies the host on its network.
For example, consider the IP address 207.61.16.119 and the subnet mask 255.255.255.0. Converting these two numbers to binary and ANDing them gives the host’s Network ID:
Host = 11001111 00111101 00010000 01110111
Mask = 11111111 11111111 11111111 00000000
AND = 11001111 00111101 00010000 00000000
= 207.61.16.0 = network ID
Taking the logical NOT of the subnet mask and ANDing it with the host’s IP address gives the host’s Host ID:
Host = 11001111 00111101 00010000 01110111
NOT Mask = 00000000 00000000 00000000 11111111
AND = 00000000 00000000 00000000 01110111
= 0.0.0.119 = host ID
Notations: CIDR vs. Decimal
Subnet masks are expressed either in CIDR notation or dotted-decimal format. CIDR notation simply appends a slash followed by the number of ones in the mask. For example, /24 equates to 255.255.255.0. Meanwhile, dotted-decimal format writes the mask as four octets separated by dots.
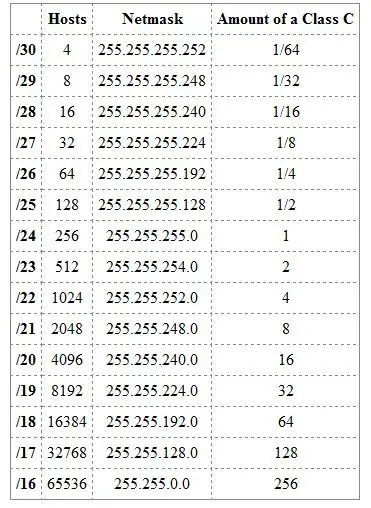
Types of Subnet Masks
Two types of subnet masks are used in TCP/IP networking:
- Default subnet masks: Partition IP addresses into their network ID and host ID portions
- Custom subnet masks: Further partition the network ID into a number of separate subnets by using a process called subnetting
Default subnet masks
The default subnet masks for IP address classes A, B, and C are shown in the following table. The table also shows how these subnet masks would partition an IP address such as w.x.y.z into a network ID and a host ID portion.
Default Subnet Masks for IP Addresses
| Class | Default Subnet Mask | Network ID | Host ID |
| A | 255.0.0.0 | w | x.y.z |
| B | 255.255.0.0 | w.z | y.z |
| C | 255.255.255.0 | w.x.y | z |
Ascend routers
Some TCP/IP configuration programs, such as those for Ascend routers, use a different notation for specifying subnet masks. They append a suffix of the form /n to the host’s IP address to indicate the subnet mask, in which n equals the number of binary 1s in the subnet mask. Thus, for example, 207.61.16.119/24 signifies 207.61.16.119/255.255.255.0.
3. Creating Subnets
Manual Subnetting
Manual subnetting involves calculating network and host portions yourself. Typically, you’d start with a single network and divide it into smaller subnets to suit your needs. Manual subnetting provides granular control but requires a strong understanding of bitwise operations. Read our article specifically about the process of subnetting.
Automatic Subnetting
Automatic subnetting relies on software tools to generate subnets. These tools perform the complex calculations for you, thus eliminating human error. While convenient, automated methods may not offer the fine-grained control that some advanced configurations require.
Use Cases
Subnetting finds applications in various settings: isolating network traffic, enhancing security, or optimizing resource allocation. In data centers, different subnets can segregate traffic types. In enterprise networks, subnets often separate departments or even individual teams.
4. Subnet Calculations
Network Address
The network address is the lowest IP in a subnet, obtained by bitwise ANDing an IP address with its subnet mask. It signifies the beginning of the IP range and is not assignable to a host.
Broadcast Address
The broadcast address is the highest IP in the subnet, derived by setting all host bits to 1 in the network address. It serves to send data to all hosts within the subnet. Like the network address, it is not usable for a host.
Range of Hosts
The range of hosts comprises the IP addresses that fall between the network and broadcast addresses. These are the assignable IPs. Calculating this range requires understanding both the network and broadcast addresses.
In summary, the creation of subnets—whether manual or automatic—serves diverse needs in networking. As we’ve seen, subnet calculations form the bedrock of this practice, requiring precise identification of network, broadcast, and host addresses. The upcoming chapters will expand on tools and best practices for implementing these concepts effectively.
5. Working with Subnet Tools
Subnet Calculators
Subnet calculators simplify the task of subnetting by automating the math. Simply input your IP address and subnet mask, and these tools will output the network address, broadcast address, and range of hosts. They are invaluable for quickly validating configurations.
Command-Line Tools
Command-line utilities like ipconfig (Windows) and ifconfig or ip (Linux) offer more advanced functionalities. These tools not only display the current subnet mask but also allow for dynamic changes. Additionally, netstat can provide routing tables, showcasing the efficiency of your subnetting strategy.
6. Common Errors and Troubleshooting
Misconfiguration
One of the most common errors is misconfiguration of the subnet mask, leading to network isolation or routing inefficiencies. Always double-check your settings and consult network documentation to avoid such issues.
Diagnosis with ping and traceroute
To troubleshoot, use the ping command to test connectivity between hosts in the same subnet. For more advanced diagnosis, traceroute maps the path packets take, identifying where a failure might occur. Both are instrumental in pinpointing problems related to subnetting.
In summary, various tools are available for working with subnets—ranging from automated calculators to more hands-on command-line utilities. Regardless of your approach, errors can occur, making troubleshooting skills crucial. Utilizing basic commands like ping and traceroute can often resolve these issues efficiently. The next chapters will explore subnetting in cloud environments and the trends shaping its future.
7. Subnetting in Cloud and Virtual Networks
AWS VPC
Amazon Web Services (AWS) offers a Virtual Private Cloud (VPC) where you can create your own subnets. These subnets can be either public or private, allowing for complex networking architectures. Subnetting in AWS VPC is integral for load balancing, high availability, and security configurations.
Azure Subnets
Similarly, Microsoft Azure provides Virtual Network (VNet) capabilities, wherein you can define your own subnets. Azure allows for integration with on-premises networks and offers advanced features like Network Security Groups (NSGs) to enforce subnet-level policies.
8. Future Trends
Scalability Concerns
With the growing complexity of networks, scalability becomes a pressing issue. Future solutions may look toward hierarchical or nested subnetting as a way to cope with this challenge, enabling easier management and greater efficiency.
Integration with SDN
Software-Defined Networking (SDN) is reshaping the landscape. As SDN solutions become more prevalent, we can expect tighter integration with subnetting features. This evolution will likely provide more automated, intelligent routing options, potentially minimizing the need for manual subnetting.
9. Summary and Key Takeaways
In sum, subnetting is a cornerstone of network engineering, impacting everything from basic network configurations to advanced cloud architectures. Through a comprehensive understanding of its roles, calculations, and tools, one gains the skill set required for effective network design and troubleshooting.
10. References
- What is the Subnet Mask? (YouTube Video)
- Comer, Douglas E. “Internetworking with TCP/IP, Volume 1.”
- Tanenbaum, Andrew S. “Computer Networks.”
- Hallberg, Bruce. “Networking: A Beginner’s Guide.”
- RFC 950 – Internet Standard Subnetting Procedure
- RFC 1518 – An Architecture for IP Address Allocation with CIDR
- RFC 4291 – IP Version 6 Addressing Architecture