Access masks are crucial components in operating systems, particularly for managing permissions and access control.
This article delves into the concept of access masks, outlining their evolution from older Windows versions to their current state in modern operating systems. As technology progresses, understanding these changes is vital for computer engineers, students, and professionals alike. This comprehensive guide will navigate you through the intricacies of access masks, their role in security, and their application in various operating systems.
Table of Contents:
- What is an Access Mask?
- Components of an Access Mask
- Access Masks in Modern Windows
- Access Masks in Other Operating Systems
- Programming with Access Masks
- Access Masks and Security
- Troubleshooting Common Issues
- Conclusion
- References

1. What is an Access Mask?
Definition and Basic Concept
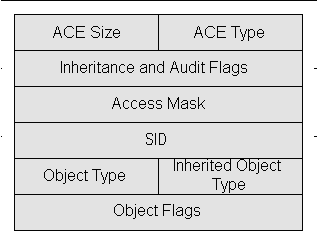
An access mask is a 32-bit integer used in computing, particularly in operating systems, as part of an access control entry (ACE) to specify the permitted or denied rights for a user or group. It acts as a bitmask, where different bits represent different rights and permissions. This mechanism is fundamental in managing file and object permissions, ensuring that users and processes operate within their authorized capacities.
Access masks play a pivotal role in security models by defining what actions (like read, write, execute) can be performed on objects like files, directories, or system resources. These masks are part of a broader security descriptor, which includes owner and group information, discretionary access control lists (DACLs), and system access control lists (SACLs).
Historical Overview in Windows OS
In earlier versions of Windows, such as Windows NT and Windows XP, access masks were integral to the operating system’s security architecture. They were used extensively to manage permissions in the NTFS file system and other resources like registry keys and process handles. Each object had a security descriptor, and the access mask within it determined which operations were permissible.
Over time, as Windows evolved, so did the implementation and complexity of access masks. With the advent of more sophisticated security requirements and features in newer versions of Windows, like Windows 10 and Windows Server editions, access masks have become more nuanced. They now support more granular permissions and are essential in advanced security features like User Account Control (UAC) and role-based access control (RBAC).
2. Components of an Access Mask
Detailed Breakdown of Access Mask Structure
The 32-bit structure of an access mask in Windows can be broken down into several components:
- Standard Rights (16 bits): These are common across all types of securable objects and include permissions like delete, read permissions, change permissions, and take ownership.
- Specific Rights (16 bits): These are object-specific and define permissions relevant to the particular type of object, such as file read/write or registry key modification.
- Generic Rights: These are high-level rights that map to standard and specific rights, making it easier to set common permissions across different object types. They include generic read, write, execute, and all.
Examples of Standard Access Rights
- Read (Generic Read): This right typically allows reading data from a file or a registry key.
- Write (Generic Write): It permits the modification of a file or registry key.
- Execute (Generic Execute): In the context of a file, this might allow running an executable; for a directory, it might allow traversing the directory.
- Full Control (Generic All): This grants all possible permissions on the object, including modifying permissions and ownership.
By understanding these components, administrators and developers can effectively manage and implement security policies in a Windows environment. The next chapters will explore how these concepts are applied in modern operating systems and their programming implications.
3. Access Masks in Modern Windows
Changes in Recent Windows Versions
In recent iterations of Windows, including Windows 10 and Windows Server editions, there have been significant enhancements to how access masks function and are utilized. These changes reflect the evolving landscape of security and the need for more robust, flexible control mechanisms.
- Enhanced Granularity: Modern versions have introduced more detailed permission sets, allowing finer control over what users and processes can do. This is particularly evident in complex environments like corporate networks and cloud services.
- Integration with Advanced Security Features: Access masks are now closely integrated with features like User Account Control (UAC) and Windows Defender. UAC, for example, uses access masks to help manage application privileges and prevent unauthorized system changes.
- Improved Compatibility and Standardization: There’s a concerted effort to standardize permissions across different Windows services and applications, making it easier for administrators to manage permissions uniformly.
Practical Examples and Scenarios
- File System Security: In Windows 10, an access mask can be used to finely tune who can access specific files or directories, including read, write, execute, or full control permissions.
- Registry Key Management: Administrators can set specific access masks on registry keys to restrict who can modify system settings, vital for maintaining system integrity and security.
- Application Management: Access masks determine the level of access an application has, crucial in environments where applications need to be restricted for security or performance reasons.
4. Access Masks in Other Operating Systems
Comparison with Linux and macOS
Access control mechanisms in operating systems like Linux and macOS follow similar fundamental principles but differ in implementation and nomenclature.
- Linux: Instead of access masks, Linux primarily uses a combination of permissions (read, write, execute) and access control lists (ACLs). Linux’s permissions are more straightforward, with a focus on user, group, and others, but ACLs in Linux offer a level of detail comparable to access masks in Windows.
- macOS: Being a UNIX-based system, macOS also employs a permission and ACL system akin to Linux. However, it integrates more closely with its graphical user interface and has unique features tailored to its ecosystem.
Universal Principles and Differences
The universal principle across these operating systems is the need to control access to system resources and data. However, the implementation differs:
- Windows: Uses a more structured approach with access masks forming part of a broader security descriptor.
- Linux/macOS: Leans towards a more straightforward permission set but with the flexibility of ACLs for detailed access control.
Understanding these differences is crucial for cross-platform system administrators and software developers who need to ensure compatibility and security across different operating environments.
5. Programming with Access Masks
Using Access Masks in Software Development
In software development, particularly when developing applications for Windows environments, understanding and effectively using access masks is crucial. Access masks are often used when writing programs that interact with the operating system’s security model, such as when creating, accessing, or modifying files, directories, or other securable objects.
- API Integration: Windows provides a set of APIs for managing security attributes, including access masks. These APIs are part of the Windows Security Model and are accessible through languages like C++, C#, and PowerShell.
- Contextual Use: Developers need to consider the context in which the access mask is used, such as in file operations, process management, or registry access, as this dictates the specific rights that need to be set.
API and Coding Examples
- C++ Example (File Access):
// Setting a file's access mask in C++
PSECURITY_DESCRIPTOR pSD;
DWORD dwRes = GetNamedSecurityInfo(L"example.txt", SE_FILE_OBJECT,
DACL_SECURITY_INFORMATION, NULL, NULL, NULL, NULL, &pSD);
if (dwRes == ERROR_SUCCESS) {
// Modify the DACL in the security descriptor.
// Set specific access mask permissions as needed.
}
- C# Example (Directory Access):
// Setting directory access mask in C#
DirectoryInfo dInfo = new DirectoryInfo(@"C:\exampleFolder");
DirectorySecurity dSecurity = dInfo.GetAccessControl();
dSecurity.AddAccessRule(new FileSystemAccessRule("user", FileSystemRights.Read, AccessControlType.Allow));
dInfo.SetAccessControl(dSecurity);
6. Access Masks and Security
Role in System Security and User Management
Access masks are a fundamental part of system security in Windows, playing a critical role in defining who has access to what resources and how they can interact with those resources. They are essential for implementing least privilege principles, ensuring that users and applications only have the minimum levels of access necessary for their functions.
- Fine-Grained Access Control: By specifying detailed permissions, access masks help prevent unauthorized access and potential security breaches.
- Audit and Compliance: Access masks are integral in auditing access to sensitive data and ensuring compliance with security policies and regulations.
Best Practices for Administrators
- Regular Review and Update of Permissions: Administrators should periodically review and update the access masks to ensure they reflect current requirements and security standards.
- Principle of Least Privilege: Always assign the minimum necessary rights to users and applications.
- Testing and Validation: Before implementing changes in a live environment, test the access masks in a controlled setting to ensure they work as intended without disrupting normal operations.
- Documentation and Change Management: Maintain clear documentation of all permissions and changes made, aiding in troubleshooting and future audits.
- Education and Training: Ensure that all relevant personnel are educated about the importance of access masks and how to manage them effectively.
By adhering to these best practices, administrators can leverage access masks to enhance the security and efficiency of their systems, ensuring robust protection against unauthorized access and potential security threats.
7. Troubleshooting Common Issues
Identifying and Resolving Access Mask Problems
Access mask issues often manifest as permission errors, where users cannot access resources or perform actions they are supposed to be able to. Identifying these problems usually involves examining the security settings of the resource and the permissions of the user or application encountering the issue.
- Incorrect Permissions: Commonly, issues arise from incorrectly set permissions. This can be due to a misunderstanding of the necessary rights or a mistake during configuration.
- Inheritance Issues: In Windows, permissions can be inherited from parent objects. Problems can occur when inherited permissions conflict with explicit permissions.
Tools and Techniques for Diagnostics
- Security Auditing Tools: Windows Event Viewer can be used to track permission-related events, helping identify where and why access is being denied.
- Command-Line Utilities: Tools like
icaclsin Windows allow administrators to view and modify access masks from the command line, offering a powerful way to troubleshoot and resolve issues. - Third-Party Software: There are various security management tools available that can provide more detailed analyses and easier interfaces for managing complex permission structures.
8. Conclusion
Access masks are a cornerstone of modern operating system security, playing a vital role in resource and user management. Their complexity and importance have grown alongside advancements in operating systems and the increasing need for granular control over permissions. Understanding, effectively implementing, and troubleshooting access masks is essential for system administrators, security professionals, and software developers working in diverse IT environments.
9. References
Books:
- “Windows Internals, Part 1” by Mark Russinovich, Alex Ionescu, and David A. Solomon – A comprehensive guide to the architecture and internal mechanisms of Windows OS.
- “Operating Systems: Principles and Practice” by Thomas Anderson and Michael Dahlin – Offers insights into the fundamental concepts of operating systems, including security models.
RFCs:
- RFC 4949 – “Internet Security Glossary, Version 2” – Provides definitions and explanations of various security-related terms, including those relevant to access control and permissions.
- RFC 3644 – “Policy Quality of Service (QoS) Information Model” – While focused on QoS, this RFC provides useful background on policy-based management, relevant to access mask configuration.