Category: Letter S
-

Small Form-Factor Pluggable (SFP)
In this article, we will explore the Small Form-Factor Pluggable (SFP) and delve into its features, benefits, and its significance in modern network architectures.
-
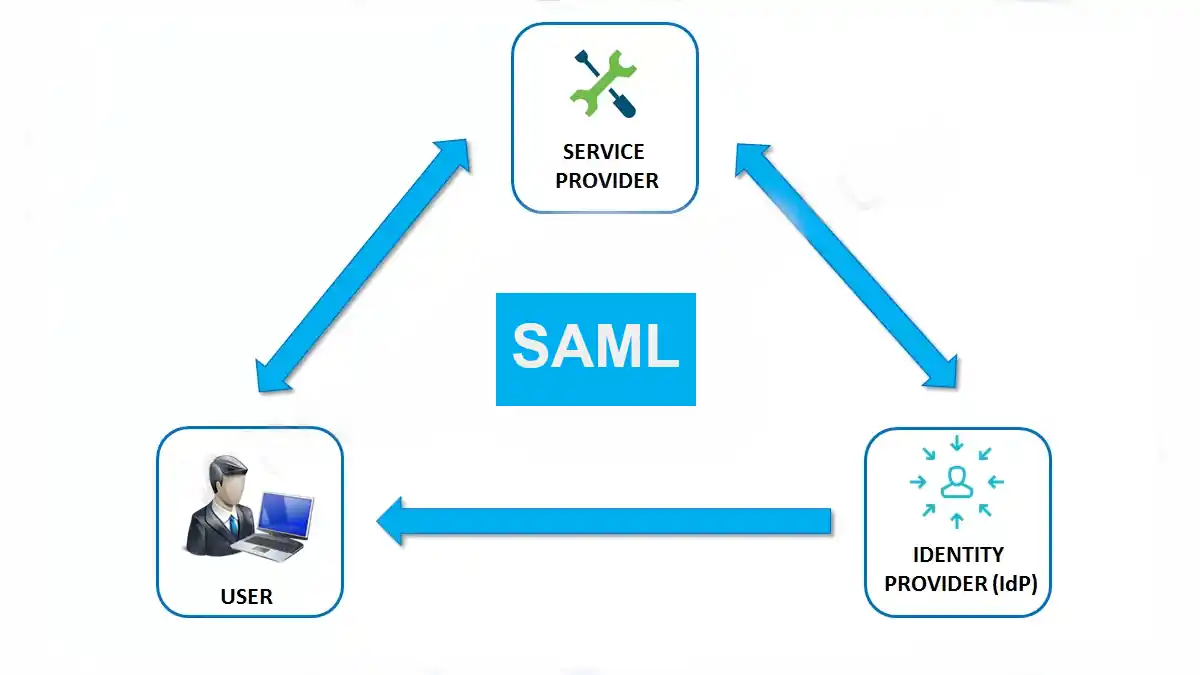
Security Assertion Markup Language (SAML)
It’s time to talk about Security Assertion Markup Language (SAML). Welcome to the exciting realm of network security and access management!
-

Demystifying Storage Area Network (SAN)
In this blog post, we will embark on a journey to unravel the mysteries of SANs, exploring their fundamental concepts, benefits, and real-world applications.
-

Software-Defined Networking (SDN): The Future of Networking?
Software-Defined Networking (SDN) is a network architecture approach that decouples the control plane from the data plane, enabling centralized control of the entire network through software.
-
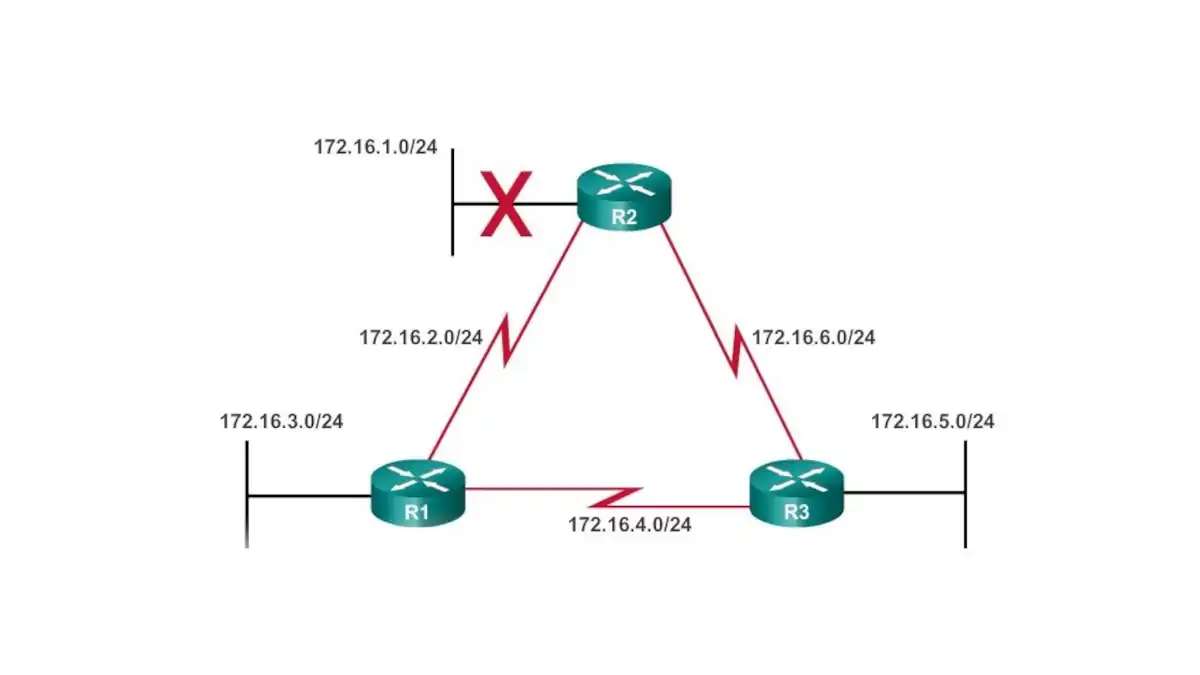
What is the Slow Convergence Problem in routing protocols?
The slow convergence problem refers to the time it takes for a routing protocol to converge, or to reach a stable state in which all routers in the network have the same view of the network topology and can accurately route packets to their destinations.
-
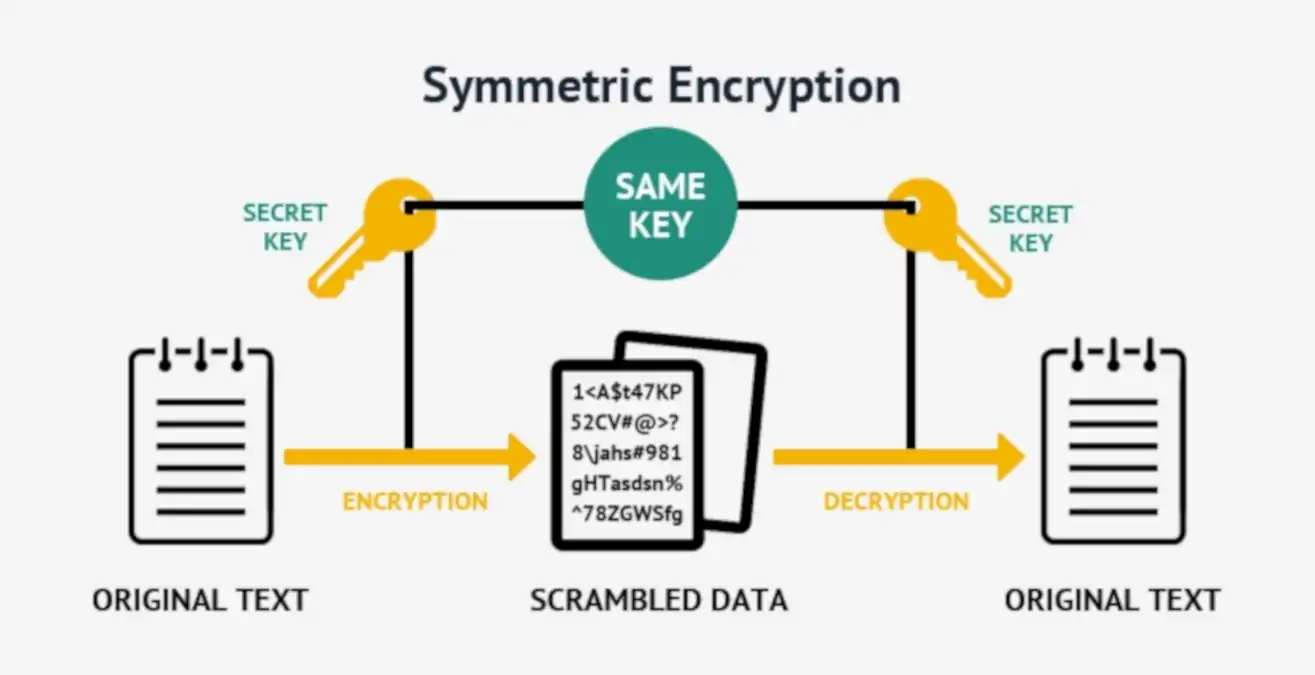
Symmetric Encryption
Symmetric encryption, or single-key encryption, is the most well-understood cryptography primitive.
-
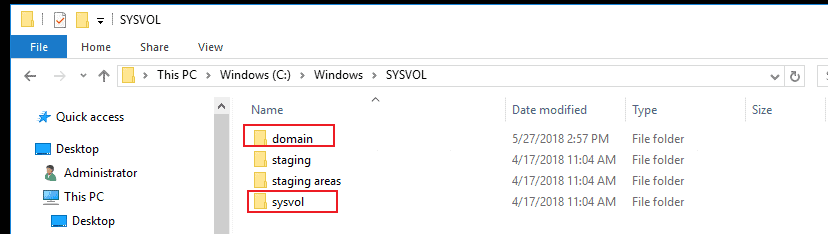
SYSVOL Share in Active Directory: A Comprehensive Guide
Dive into the essentials of SYSVOL Share in Active Directory, exploring its functions, structure, and importance in Windows domain environments.
-
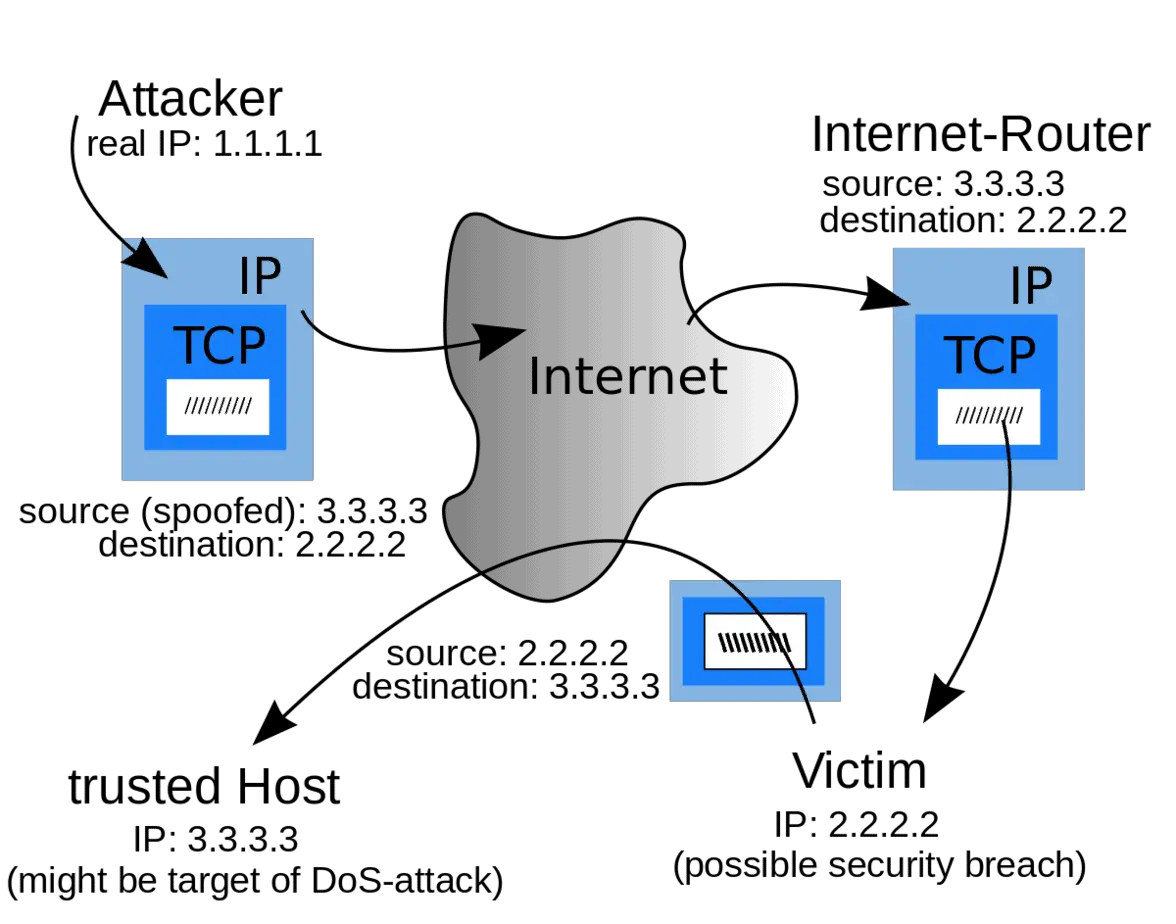
What is an IP Spoofing Attack?
IP spoofing is a technique used to gain unauthorized access to computer systems or networks by disguising the source IP address of a packet. This goal is accomplished by altering the source addresses of packets, making them appear as though they came from a trusted user within the network, rather than from a distrusted outside…
-
Server Management Tools
Server Management Tools are a set of tools hosted in Azure and available for free with a new web-based graphic user interface. Learn how to easily use those tools. As infrastructure and deployments become more hybrid in nature, where we have workloads spread across clouds, the management effort to control all these different areas increases…
-

Structured Query Language (SQL)
Definition of Structured Query Language in the Network Encyclopedia. What is Structured Query Language (SQL)? SQL stands for Structured Query Language, a standards-based language used by relational database management programs primarily for constructing queries. Structured Query Language was originally developed by IBM for mainframe computing environments and is widely used in relational database management systems.…
-
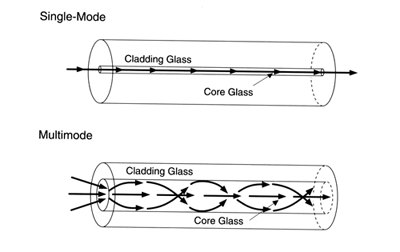
Single-Mode Fiber-Optic Cabling:
Imagine a highway so efficient that only one type of vehicle could drive on it — one that’s incredibly fast and never gets caught in traffic. Now, replace that vehicle with a beam of light, and you have the essence of single-mode fiber-optic cabling. In this article, we’re going to explore the fascinating world of…
