Have you ever pondered the secrets your smartphone holds in that tiny SIM card? Welcome to the ultimate guide on Subscriber Identity Module (SIM)—the small yet powerful technology that connects you to the world. This article aims to uncover the layers of complexity behind SIM cards, offering a rich, insightful resource for tech enthusiasts, computer science students, and telecommunications professionals alike. Strap in for a technological deep dive that will take you from the origins of SIM technology to its modern applications and future possibilities.
Jump to:
- What is a Subscriber Identity Module (SIM)?
- Historical Context
- Technical Specifications
- How Does a SIM Card Work?
- Security Aspects
- Modern-day Applications and Use-cases
- SIM vs. Other Technologies
- Future Trends
- Conclusion
- References & Further Reading
What is a Subscriber Identity Module (SIM)?
Definition and Basic Functionality
A Subscriber Identity Module, commonly referred to as a SIM card, is an integrated circuit that securely stores essential information to authenticate and identify users on mobile networks. It plays a critical role in the Global System for Mobile Communications (GSM), as well as other cellular technologies like 3G, 4G, and even the latest 5G networks. When you make a call, send a text, or use data services, it’s the SIM card that establishes the connection between your mobile device and the network, acting as a form of digital ID.
The SIM card serves multiple purposes:
- Authentication: Verifies the user’s identity to the network.
- Data Storage: Holds information such as your phone number, PIN, PUK, and SMS messages.
- Carrier Details: Contains settings for internet connections and network identification codes.
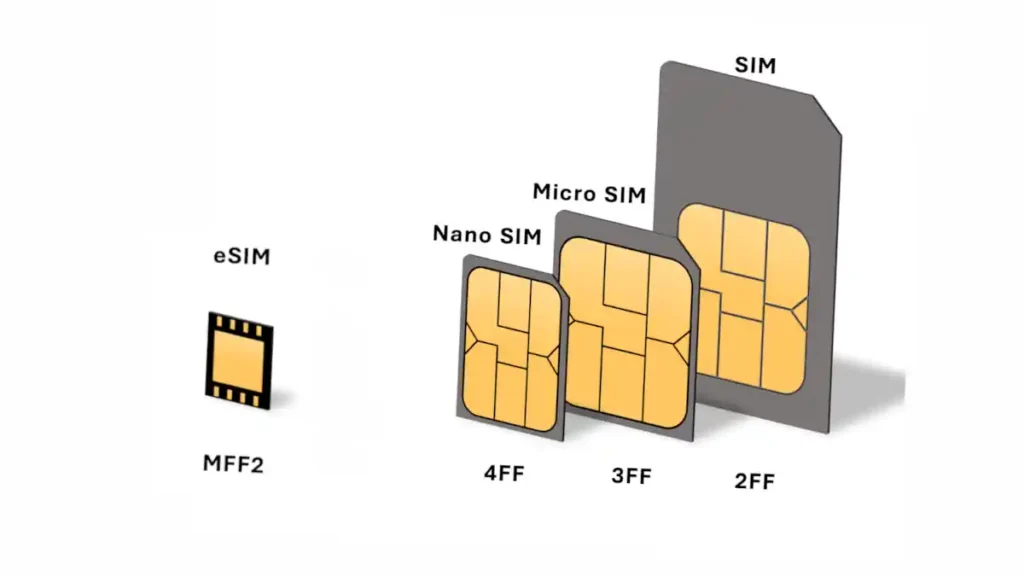
Types of SIM Cards
Over the years, the physical size of SIM cards has reduced, adapting to the ever-shrinking sizes of modern mobile devices. Here are the main types:
- Standard SIM: Measuring 25 x 15 mm, this was the original size and has now become relatively obsolete.
- Micro SIM: With dimensions of 15 x 12 mm, this variant gained popularity with the advent of smaller, sleeker smartphones.
- Nano SIM: The smallest form, measuring just 12.3 x 8.8 mm, is now the industry standard, particularly for high-end smartphones.
Understanding the different types of SIM cards is essential not just for consumers who want the right fit for their phones, but also for tech professionals aiming to develop new solutions or manage mobile services.
Historical Context
Early Adoption and Evolution
The story of the SIM card begins with the birth of GSM (Global System for Mobile Communications) in the early 1990s. The initial idea was simple yet revolutionary: to create a secure, universal standard for mobile communications. As mobile phones moved from analog to digital, the need for a sophisticated and secure method for storing subscriber information became paramount. Enter the SIM card—a groundbreaking technology that transitioned mobile phones from device-centric to user-centric tools.
SIM Card Milestones
- Early 1990s: First SIM cards are the size of a credit card.
- Late 1990s: Introduction of the smaller, “plug-in” SIM cards.
- 2003: The arrival of the Micro SIM, thanks to the miniaturization trend.
- 2012: Nano SIMs are introduced, becoming the new industry standard.
- 2016 and Beyond: Embedded SIM (eSIM) technology starts to emerge, allowing for even more streamlined and flexible mobile experiences.
Subscriber Identity Module Technical Specifications
Physical Characteristics
SIM cards have gone through various iterations, shrinking in size but expanding in capabilities. A typical SIM card consists of a microcontroller and internal memory, encased in a plastic card. Their dimensions, as discussed in the previous section, have been reducing over time—from the original credit card-sized format to the current Nano SIMs.
Data Storage and Encryption Methods
The data stored on a SIM card is encrypted for security. It includes:
- ICCID (Integrated Circuit Card Identifier): A unique identifier for the SIM card.
- IMSI (International Mobile Subscriber Identity): Used for identifying the user of a cellular network.
- Authentication Key (Ki): A secret key used for authentication and encryption.
The encryption algorithms A3 and A8 are commonly employed for securing the communication between the SIM card and the network. In modern SIMs, more advanced encryption methods like 3DES or AES have been introduced to fortify security measures.
The SIM also contains non-encrypted data like your phone number, text messages, and network settings. The storage capacity has evolved from a mere 32KB in early SIM cards to current versions that can hold up to 128KB or more.
How Does a SIM Card Work?
Authentication and Authorization Process
First, you insert the SIM card into your mobile device. Then, the phone powers up and initiates a handshake with the network. The network sends a random number to the SIM card. Your SIM crunches this number with a secret key. It sends the result back to the network. If the network recognizes the result, you’re in! Your phone gains access to all carrier services.
Carrier-specific vs. Unlocked SIMs
Carrier-specific SIM cards lock you into one network. On the flip side, unlocked SIMs offer more flexibility. You can switch networks just by replacing the SIM card. Some phones come carrier-locked but can be unlocked later, offering you the best of both worlds.
Security Aspects
SIM Cloning and Countermeasures
SIM cloning poses a big risk. Yet, modern SIM cards fight back with advanced security features. Today’s SIMs use dynamic encryption algorithms, making cloning nearly impossible. Plus, carriers often provide additional security measures, like a PIN requirement, to protect against unauthorized use.
Encryption Algorithms
Security doesn’t stop there. Your SIM card also uses different encryption algorithms for extra protection. The older A3 and A8 algorithms served us well in the past. Now, more robust algorithms like 3DES and AES are taking over. These modern algorithms raise the bar for SIM security, ensuring your data stays private.
Modern-day Applications and Use-cases
IoT Devices
Starting with the Internet of Things (IoT), SIM cards have transcended the realm of mere mobile phones. In the IoT landscape, these tiny pieces of hardware provide the essential connection between devices and the internet. For example, a home security camera outfitted with a SIM card can transmit data directly to your smartphone.
Dual SIM Functionality
Moving on, let’s explore dual SIM functionality. This isn’t just a fad; it’s a powerful tool for multitaskers. Whether you’re juggling work and personal calls or leveraging different network strengths, dual SIM phones offer unparalleled flexibility. You can have two numbers, two service providers, and even two different data plans—all on a single device.
eSIM and Its Advantages
Lastly, eSIM technology is changing the game. Unlike traditional SIM cards, eSIMs are built directly into your device. This eliminates the need for a physical card and makes switching between carriers as easy as tapping a few buttons. Additionally, eSIMs are more secure, leaving no avenue for physical tampering.
SIM vs. Other Technologies
Comparison with Other Storage and Authentication Methods
By now, you might be wondering how SIM cards stack up against other storage and authentication technologies. Take, for instance, RFID chips. They are commonly used in access cards and pet identification. Although similar in function, RFID chips lack the encryption standards and multifunctionality of SIM cards.
Similarly, flash drives serve as portable data storage. But they don’t offer the same level of security encryption or carrier authentication. In essence, while other technologies may appear similar, none offer the same balanced blend of functionality and security that SIM cards do.
Future Trends
Soft SIMs and Embedded SIMs
Transitioning into the future, let’s delve into Soft SIMs and Embedded SIMs. Soft SIMs are a major breakthrough, as they exist purely as software applications. This radical approach could eventually make traditional, physical SIM cards obsolete. On the other hand, Embedded SIMs or eUICCs are welded into the device, meaning they can’t be removed. This serves a dual purpose: it secures the device better and also enables easier switching between carriers remotely.
5G and SIM Technology
Additionally, 5G technology is transforming the role of SIM cards. With unparalleled speed and latency, 5G demands a new level of efficiency and security from SIMs. Future SIM technology will likely include advanced encryption methods and possibly new form factors to meet these evolving requirements.
Conclusion
Summary of Key Points
In closing, the Subscriber Identity Module or SIM card has come a long way from its early days. From merely facilitating mobile communication to becoming an integral part of IoT devices, dual-SIM functionalities, and even accommodating 5G technologies, SIM cards are indispensable.
Future Prospects and Technological Evolution
Looking ahead, the horizon holds promising advancements like Soft SIMs, eSIMs, and 5G-compatible SIM technologies. While the physical card may diminish in relevance, the core functionalities and security features will continue to evolve, matching pace with emerging technological trends.
References & Further Reading
- “The Evolution of SIM Cards in Mobile Communication” – [Journal of Telecommunications]
- “Mechanism for generic purpose SIM card communication and its applications” – [IEEE Publications]
- “Security and Privacy Preserving for IoT and 5G Networks: Techniques, Challenges, and New Directions“, by Ahmed A. Abd El-Latif (Editor), Bassem Abd-El-Atty (Editor), Salvador E. Venegas-Andraca (Amazon)
- “5G challenges should be overcome with a ‘security by design’ approach, says Orange CTO” – [Telecom Review]