Category: A to Z
-

WiFi Booster: Boost Your Signal Today
Discover how a WiFi Booster can revolutionize your internet experience by extending signal range and improving connectivity. Learn more now!
-

Security Devices in Computer Networks Unveiled
Dive into the essentials of security devices safeguarding computer networks. Explore their roles, types, and why they’re pivotal for digital safety.
-

Understanding Large Language Models: Behind the Magic
Explore the intricate world of Large Language Models (LLMs), as we demystify how they’re revolutionizing technology and shaping the future of AI.
-

Computer System Analyst: Demystifying the Role
Dive deep into the dynamic role of a computer system analyst. Explore tasks, skills, and the bridge between tech & business.
-

5G Network: Beyond Speed and Coverage
Explore the world of 5G Network – from its groundbreaking speed to its transformative impact on global tech. Dive in to understand its future potential.
-

Hackathon: Innovating Solutions at Lightning Speed
Dive deep into the exciting world of hackathons – where innovation meets collaboration, all under the ticking clock.
-
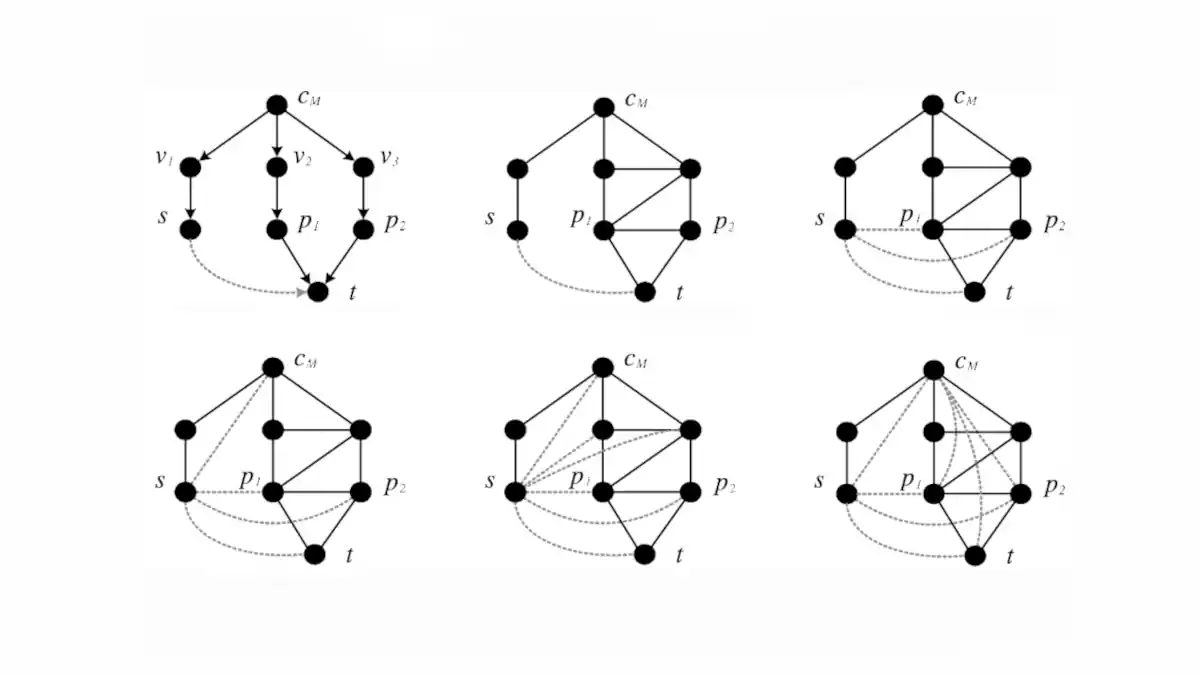
Bayesian Network: Deciphering its Intricacies
Dive deep into Bayesian Networks—a cornerstone of modern AI, merging statistics and graph theory to model complex systems
-

Data Science Basics: Deciphering Digital Data Deluge
Dive into Data Science basics – the transformative discipline where data meets decisions. Embark on a journey to unlock mysteries and shape the digital future.
-
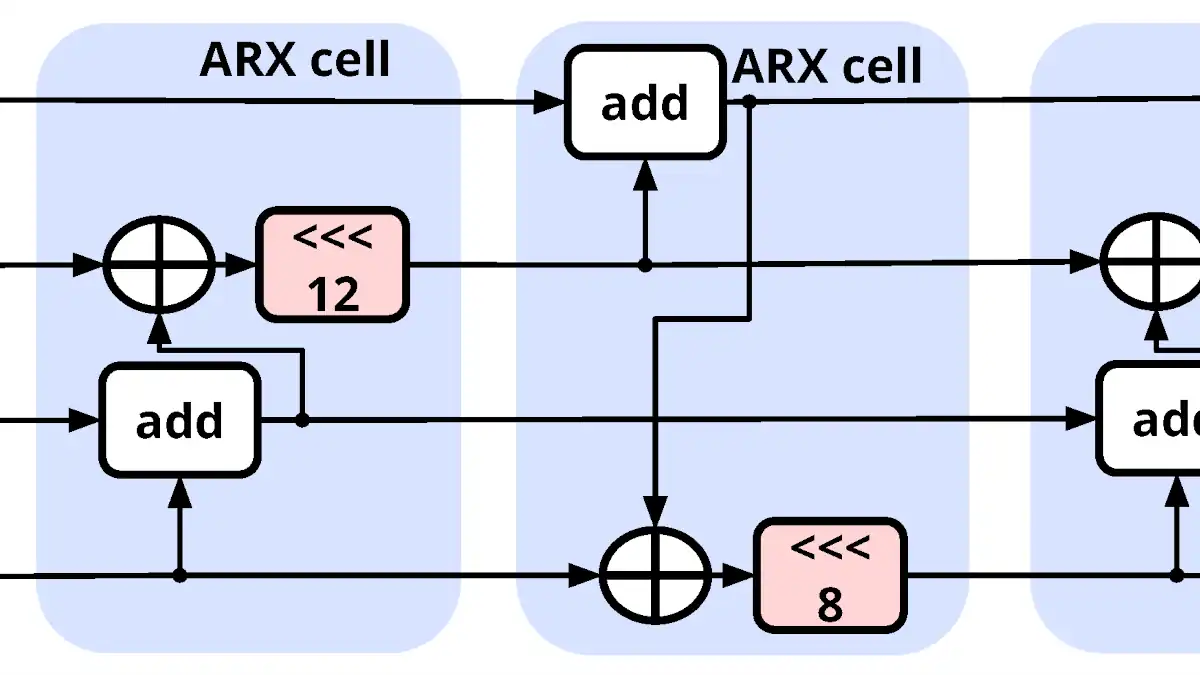
ChaCha20: The Dance of Cryptography
Dive deep into ChaCha20’s intricate dance of encryption. Explore the mathematics and design that make this cryptographic algorithm both potent and elegant.
-
![Machine Learning Basics [Start Here]](https://networkencyclopedia.com/wp-content/uploads/2023/08/machine-learning-basics.webp)
Machine Learning Basics [Start Here]
Unravel the intricate web of Machine Learning! Dive deep into its core, uncovering how it’s reshaping our world. A perfect beginner’s guide to AI’s marvel.
-
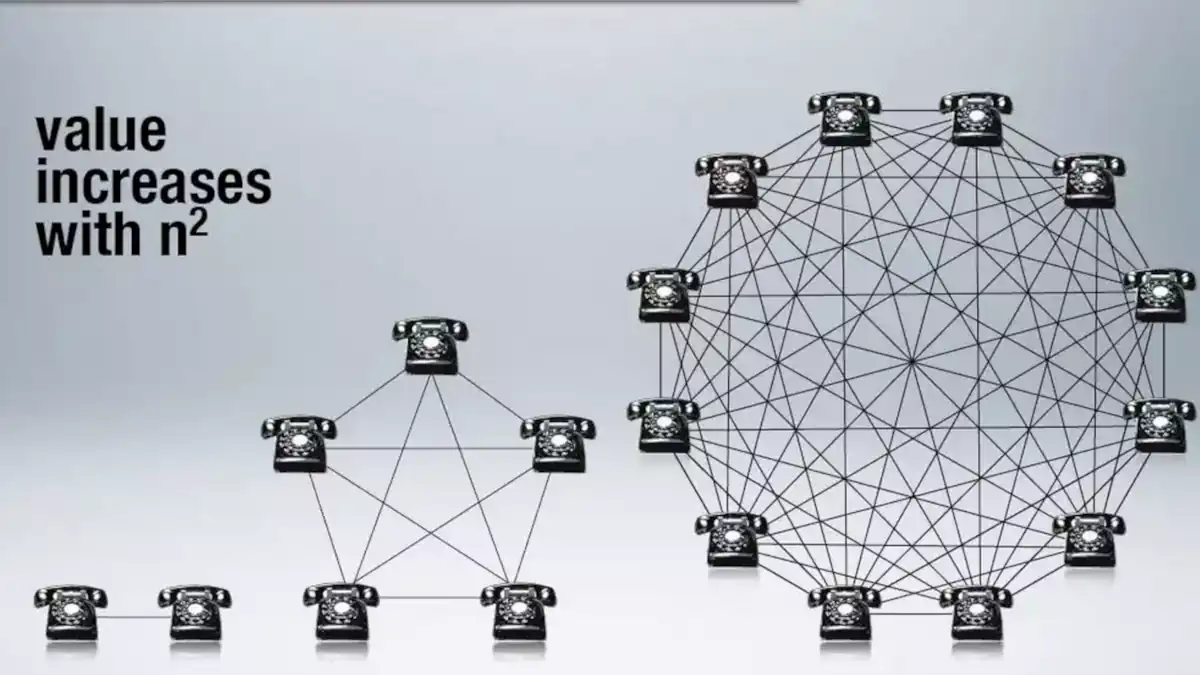
Metcalfe’s Law: Powering the Networked World
Unlock the profound insight of Metcalfe’s Law, understanding its impact on modern networks. Delve deep into the value, growth, and influence of connectivity.
-
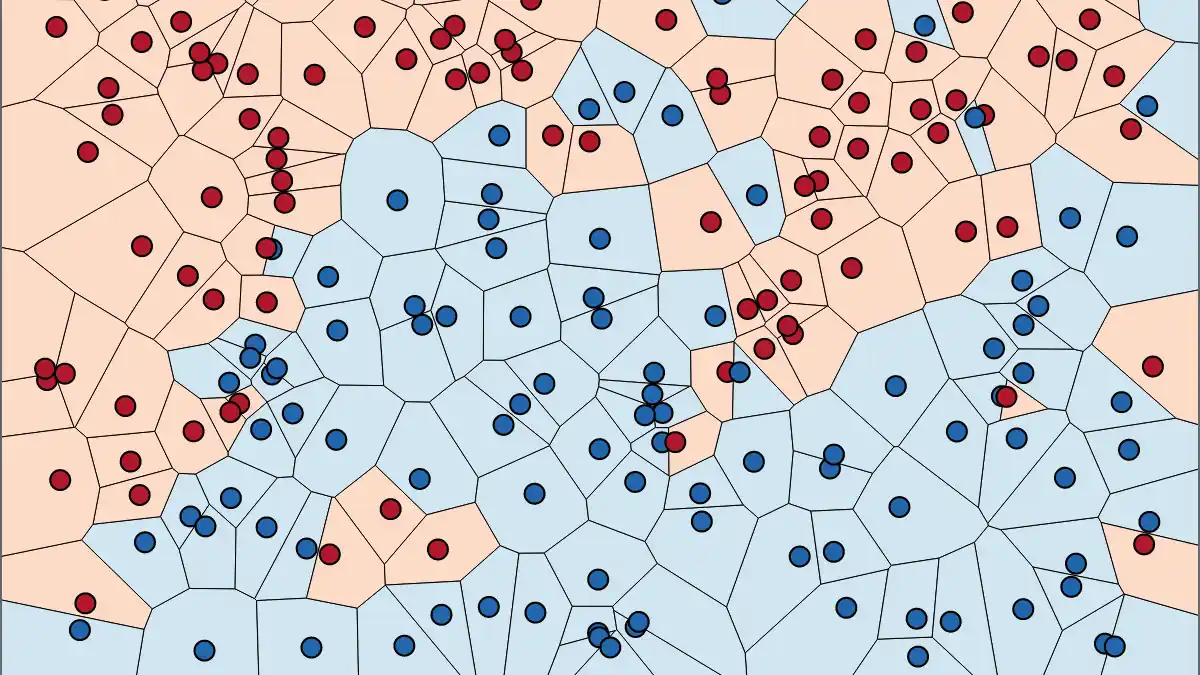
Cross-validation and kNN Algorithm
Cross-validation and the k-nearest neighbors (kNN) algorithm are staples in the machine learning practitioner’s toolkit. Let’s explore their intricacies.